Do not trust the CRITICAL_PROCESS_DIED error displayed on scam websites
Phishing/ScamAlso Known As: "CRITICAL_PROCESS_DIED" tech support scam
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is "CRITICAL_PROCESS_DIED"?
"CRITICAL_PROCESS_DIED" is a fake error/stop code, the notification of which appears on a technical support scam website. Scammers behind this web page attempt to trick visitors into calling the number provided and paying for a supposedly legitimate technical support service.
We strongly advise against trusting this scam or calling the people (cyber criminals) responsible for it. People do not generally visit these sites intentionally - they are redirected to them through other dubious web pages, deceptive ads, or by installed potentially unwanted apps (PUAs).
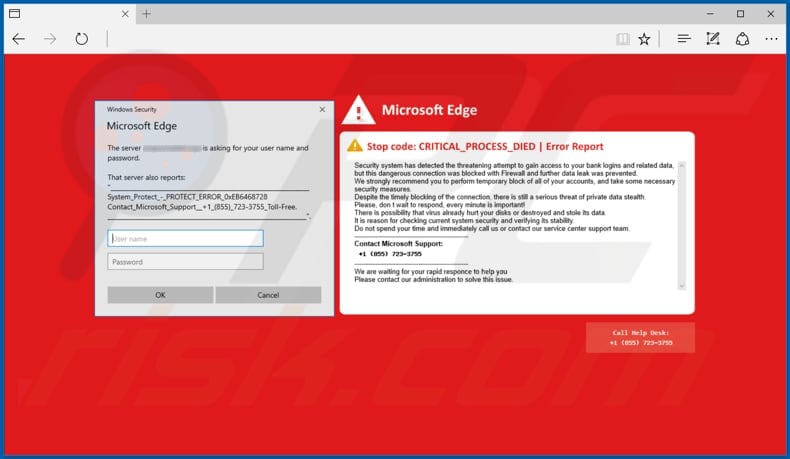
This technical support scam states that the security system has detected an attempt to gain access to the visitor's bank logins and other banking-related details. It also states that this attempt was blocked with the Firewall, however, visitors are advised to temporarily block all accounts and take necessary security measures.
They are encouraged to check current system security and stability immediately by calling the +1 (855) 723-3755 number, which is disguised as the number of the Microsoft Support/Help Desk. This scam site also asks visitors to provide their Windows usernames and passwords.
There are a number of other cases whereby scammers claim to be members of the Microsoft support team. Note that Microsoft has nothing do to with any of these 'technical support', or other, scams. Generally, people who call scammers are offered paid services or software.
The scammers behind such scams attempt to extort money from unsuspecting people. If your browser opens this, or another scam, ignored it and close the website. If this cannot be done normally (by closing the opened tab or window), end the browser process through Task Manager. Do not restore the closed browsing session, since this will reopen the same scam website.
These scam websites are usually opened by a PUA that is installed on the browser and/or operating system. These apps usually gather browsing-related information. For example, IP addresses, entered search queries, addresses of opened websites, geolocations, etc.
Sometimes they also record sensitive, personal information. The developers can then sell the details to third parties who misuse them to generate revenue. Some of these parties might be cyber criminals. PUAs often serve intrusive advertisements in the form of coupons, banners, surveys, pop-ups, and so on.
The ads conceal underlying content of visited websites and, if clicked, also open untrustworthy websites or execute scripts designed to download and/or install other unwanted apps. PUAs can lead to problems relating to online privacy, browsing safety, and other issues. Furthermore, users risk having their identities stolen.
| Name | "CRITICAL_PROCESS_DIED" tech support scam |
| Threat Type | Phishing, Scam, Social Engineering, Fraud. |
| Fake Claim | According to this tech support scam page, it has detected an attempt to gain access to the visitor's banking details. |
| Tech Support Scammer Phone Number | +1 (855) 723-3755 |
| Symptoms | Fake error messages, fake system warnings, pop-up errors, hoax computer scan. |
| Distribution methods | Compromised websites, rogue online pop-up ads, potentially unwanted applications. |
| Damage | Loss of sensitive private information, monetary loss, identity theft, possible malware infections. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Many deceptive websites are used to trick unsuspecting people into paying for supposedly legitimate services and/or software. Typically, these web pages display fake virus, error alerts and other fake notifications. Examples of other scams are "Activation Warning Alert", "Microsoft Protected Your Computer" and "Call Microsoft Helpline".
Potentially unwanted apps that make browsers open these deceptive websites are also very similar. In most cases, they open untrustworthy websites, collect information and serve intrusive ads. They are often promoted as useful and legitimate apps, however, they are useless and cause various problems.
How did potentially unwanted applications install on my computer?
Generally, people do not download or install PUAs willingly - they are tricked when these apps are included as additional offers in the download and/or installation set-ups of regular software. This PUA distribution method is called "bundling". Typically, offers to download and/or install PUAs are mentioned in settings of set-ups such as "Custom", "Advanced", and other similar sections.
To prevent PUAs from being downloaded/installed, you must change the settings (dismiss offers to download and/or install unwanted apps), however, many people often fail to check them, thereby granting PUAs permission to be installed/downloaded. They are sometimes downloaded or installed through deceptive ads - if clicked, these execute certain malicious scripts.
How to avoid installation of potentially unwanted applications
The safest way to download software and files is using official, trustworthy websites and direct links. Various third party downloaders, installers, torrent clients, eMule (and other Peer-to-Peer networks), unofficial websites, etc., should not be used.
Do not finish any download or installation process without checking "Advanced", "Custom" and other settings that are included in the setup. Dismiss offers to download and/or install unwanted software. It is not safe to click intrusive ads (especially if they are displayed on untrustworthy websites).
These can lead to other dubious websites or cause download/installation of potentially malicious apps.
Finally, remove all unwanted extensions, plug-ins and add-ons from the web browser, and software of this kind from the operating system. If your computer is already infected with PUAs, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate them.
Text presented in the left pop-up window of the "CRITICAL_PROCESS_DIED" scam website:
Windows Security
Microsoft Edge
The server ****** is asking for your user name and password.That server also reports:
"__________
System_Protect_-_PROTECT_ERROR_0xEB6468728
Contact_Microsoft_Support__+1_(855)_723-3755_Toll-Free.
__________".
Text presented in the right pop-up window of the "CRITICAL_PROCESS_DIED" scam website:
Microsoft Edge
Stop code: CRITICAL_PROCESS_DIED | Error Report
Security system has detected the threatening attempt to gain access to your bank logins and related data, but this dangerous connection was blocked with Firewall and further data leak was prevented.
We strongly recommend you to perform temporary block of all your accounts, and take some necessary security measures.
Despite the timely blocking of the connection, there is still a serious threat of private data stealth.
Please don t wait to respond, every minute is important!
There is possibility that virus already hurt your disks or destroyed and stole its data.
It is reason for checking current system security and verifying its stability.
Do not spend your time and immediately call us or contact our service center support team.
------------
Contact Microsoft Support:
+1 (855) 723-3755
------------
We are waiting for your rapid responce to help you
Please contact our administration to solve this issue.
Call Help Desk:
+1 (855) 723-3755
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is "CRITICAL_PROCESS_DIED" tech support scam?
- How to identify a pop-up scam?
- How do pop-up scams work?
- How to remove fake pop-ups?
- How to prevent fake pop-ups?
- What to do if you fell for a pop-up scam?
How to identify a pop-up scam?
Pop-up windows with various fake messages are a common type of lures cybercriminals use. They collect sensitive personal data, trick Internet users into calling fake tech support numbers, subscribe to useless online services, invest in shady cryptocurrency schemes, etc.
While in the majority of cases these pop-ups don't infect users' devices with malware, they can cause direct monetary loss or could result in identity theft.
Cybercriminals strive to create their rogue pop-up windows to look trustworthy, however, scams typically have the following characteristics:
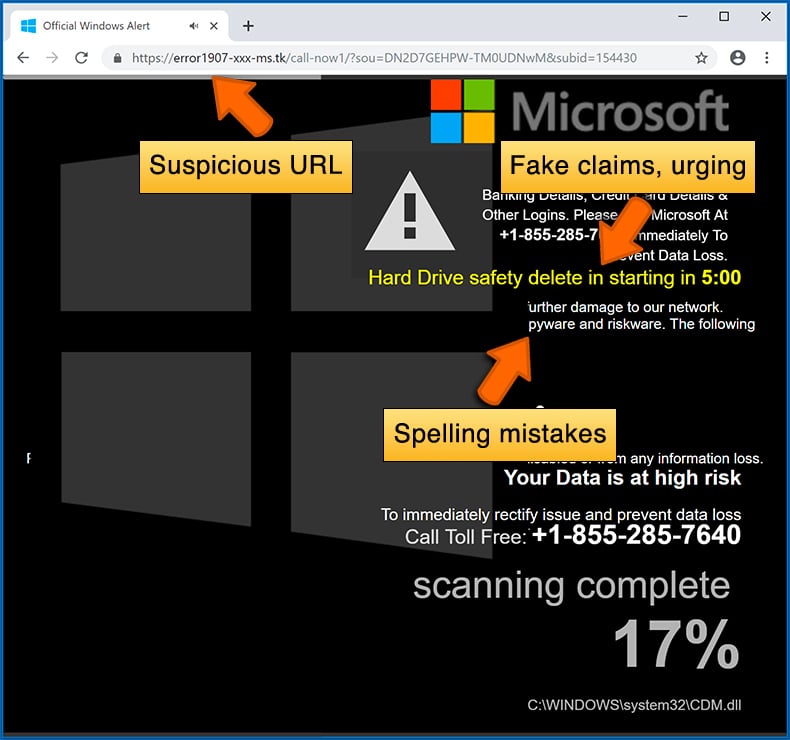
- Spelling mistakes and non-professional images - Closely inspect the information displayed in a pop-up. Spelling mistakes and unprofessional images could be a sign of a scam.
- Sense of urgency - Countdown timer with a couple of minutes on it, asking you to enter your personal information or subscribe to some online service.
- Statements that you won something - If you haven't participated in a lottery, online competition, etc., and you see a pop-up window stating that you won.
- Computer or mobile device scan - A pop-up window that scans your device and informs of detected issues - is undoubtedly a scam; webpages cannot perform such actions.
- Exclusivity - Pop-up windows stating that only you are given secret access to a financial scheme that can quickly make you rich.
Example of a pop-up scam:
How do pop-up scams work?
Cybercriminals and deceptive marketers usually use various advertising networks, search engine poisoning techniques, and shady websites to generate traffic to their pop-ups. Users land on their online lures after clicking on fake download buttons, using a torrent website, or simply clicking on an Internet search engine result.
Based on users' location and device information, they are presented with a scam pop-up. Lures presented in such pop-ups range from get-rich-quick schemes to fake virus scans.
How to remove fake pop-ups?
In most cases, pop-up scams do not infect users' devices with malware. If you encountered a scam pop-up, simply closing it should be enough. In some cases scam, pop-ups may be hard to close; in such cases - close your Internet browser and restart it.
In extremely rare cases, you might need to reset your Internet browser. For this, use our instructions explaining how to reset Internet browser settings.
How to prevent fake pop-ups?
To prevent seeing pop-up scams, you should visit only reputable websites. Torrent, Crack, free online movie streaming, YouTube video download, and other websites of similar reputation commonly redirect Internet users to pop-up scams.
To minimize the risk of encountering pop-up scams, you should keep your Internet browsers up-to-date and use reputable anti-malware application. For this purpose, we recommend Combo Cleaner Antivirus for Windows.
What to do if you fell for a pop-up scam?
This depends on the type of scam that you fell for. Most commonly, pop-up scams try to trick users into sending money, giving away personal information, or giving access to one's device.
- If you sent money to scammers: You should contact your financial institution and explain that you were scammed. If informed promptly, there's a chance to get your money back.
- If you gave away your personal information: You should change your passwords and enable two-factor authentication in all online services that you use. Visit Federal Trade Commission to report identity theft and get personalized recovery steps.
- If you let scammers connect to your device: You should scan your computer with reputable anti-malware (we recommend Combo Cleaner Antivirus for Windows) - cyber criminals could have planted trojans, keyloggers, and other malware, don't use your computer until removing possible threats.
- Help other Internet users: report Internet scams to Federal Trade Commission.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion