Remove apps that force browsers to open message-alert.info
Notification SpamAlso Known As: message-alert.info pop-up
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is message-alert[.]info?
message-alert[.]info is similar to many other rogue web pages. For example, find-soulmates[.]com, histleolderlandch[.]info and best-girls-ever[.]com.
All of these websites load dubious content or redirect visitors to other untrustworthy sites. Generally, browsers open sites such as message-alert[.]info when potentially unwanted applications (PUAs) are installed on them. Most PUAs serve intrusive ads and gather information (browsing data and other details).
![message-alert[.]info pop-up redirects](/images/stories/screenshots201910/message-alert-info-ads-homepage.jpg)
Typically, PUAs force users to visit sites such as message-alert[.]info by regularly opening them in new browser windows or tabs. Once opened, they open more (about two or three) untrustworthy sites or load dubious content. The way they behave depends on visitors' geolocations.
In any case, neither message-alert[.]info nor websites that are opened through it are trustworthy. This site also tricks visitors into allowing it to show notifications. Like most sites of this type, message-alert[.]info uses a 'clickbait' technique.
It encourages users to click the "Allow" button to supposedly play a video, however, once clicked, message-alert[.]info receives permission to show notifications.
The notifications might contain ads, links to untrustworthy websites and other dubious content. Furthermore, most PUAs collect data such as IP addresses, entered search queries, geolocations, addresses of visited websites, and other browsing-related information. Some apps record personal, sensitive data.
The developers sell the details to third parties (potentially, cyber criminals) who misuse them to generate revenue. These actions can lead to problems relating to privacy, browsing safety or even identity theft.
Many PUAs feed users with coupons, pop-ups, surveys, banners and other intrusive advertisements, which conceal underlying content of visited web pages and redirect people who click them to dubious, potentially malicious sites.
Some of these ads can execute scripts designed to download and/or install PUAs or even malware. Therefore, uninstall all PUAs from the operating system and browser immediately.
| Name | message-alert.info pop-up |
| Threat Type | Push notifications ads, Unwanted ads, Pop-up ads. |
| Detection Names | Full List Of Detections (VirusTotal) |
| Serving IP Address | 213.227.145.147 |
| Observed Domains | ivw3e.message-alert[.]info, aovts.message-alert[.]info, hm7im.message-alert[.]info, lg8rn.message-alert[.]info, 7a0vn.message-alert[.]info, qtbyo.message-alert[.]info, d7cts.message-alert[.]info, i6vrr.message-alert[.]info, 7o71m.message-alert[.]info |
| Related Domains | |
| Symptoms | Seeing advertisements not originating from the sites you are browsing. Intrusive pop-up ads. Decreased internet browsing speed. |
| Distribution Methods | Deceptive pop-up ads, potentially unwanted applications (adware). |
| Damage | Decreased computer performance, browser tracking - privacy issues, possible additional malware infections. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Most potentially unwanted applications are advertised as legitimate, useful, etc., however, few operate as promised. In most cases, they open dubious sites, collect browsing-related details and/or display ads. They are designed only to help the developers to generate revenue, and they place users at risk of a number of problems.
How did adware install on my computer?
Typically, unintentional downloads and installations are caused through deceptive ads capable of running certain scripts, or via the set-ups of other (mostly free) software. Developers often distribute PUAs using the "bundling" method. They use this method to trick people into downloading and/or installing unwanted apps together with regular software.
They include PUAs into the download and installation set-ups of various software and present them as 'additional offers'.
Typically, the offers are mentioned in settings of set-ups such as "Advanced", "Custom", and so on. People who download and install software without checking and changing the settings often give permission for unwanted apps to be downloaded and installed by default.
How to avoid installation of potentially unwanted applications
To prevent unwanted apps from being downloaded and/or installed, download software from official websites and via direct download links. All other channels, tools such as third party downloaders, installers, unofficial websites, Peer-to-Peer networks (torrent clients, eMule), etc., should not be trusted (they are often used to distribute unwanted software).
Check "Custom", "Advanced" and other similar settings of the download and/or installation setup and decline offers to download/install unwanted software. Do not trust or click intrusive ads, especially if they appear on dubious web pages.
Once clicked, they often redirect users to untrustworthy websites (such as gambling, adult dating, pornography, and so on) or cause unwanted downloads/installations. If there is a reason to believe that a PUA is already installed, remove all unwanted, suspicious extensions, add-ons or plug-ins from the browser, and programs of this type from the computer immediately.
If your computer is already infected with rogue applications, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate them.
Appearance of message-alert[.]info website (GIF):
![message-alert[.]info website appearance (GIF)](/images/stories/screenshots201910/message-alert-info-ads-appearance.gif)
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is message-alert.info pop-up?
- STEP 1. Remove spam notifications from Google Chrome
- STEP 2. Remove spam notifications from Google Chrome (Android)
- STEP 3. Remove spam notifications from Mozilla Firefox
- STEP 4. Remove spam notifications from Microsoft Edge
- STEP 5. Remove spam notifications from Safari (macOS)
Disable unwanted browser notifications:
Video showing how to disable web browser notifications:
 Remove spam notifications from Google Chrome:
Remove spam notifications from Google Chrome:
Click the Menu button (three dots) on the right upper corner of the screen and select "Settings". In the opened window select "Privacy and security", then click on "Site Settings" and choose "Notifications".
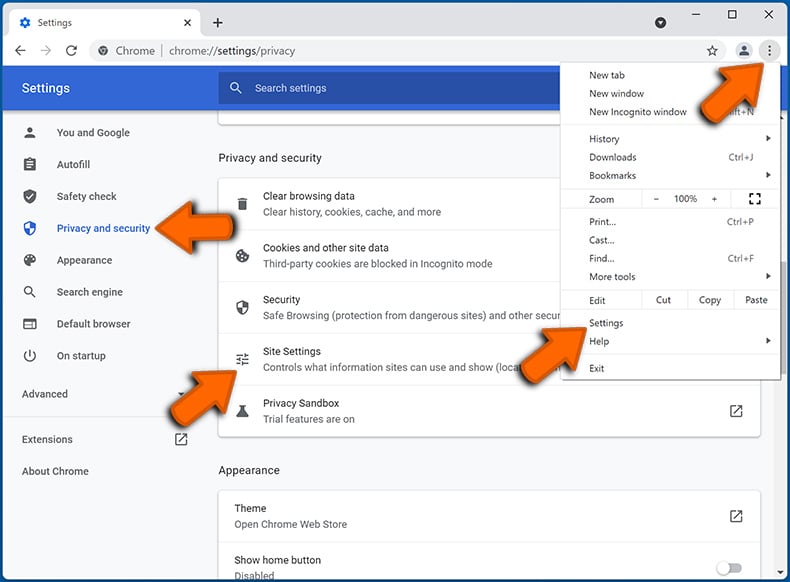
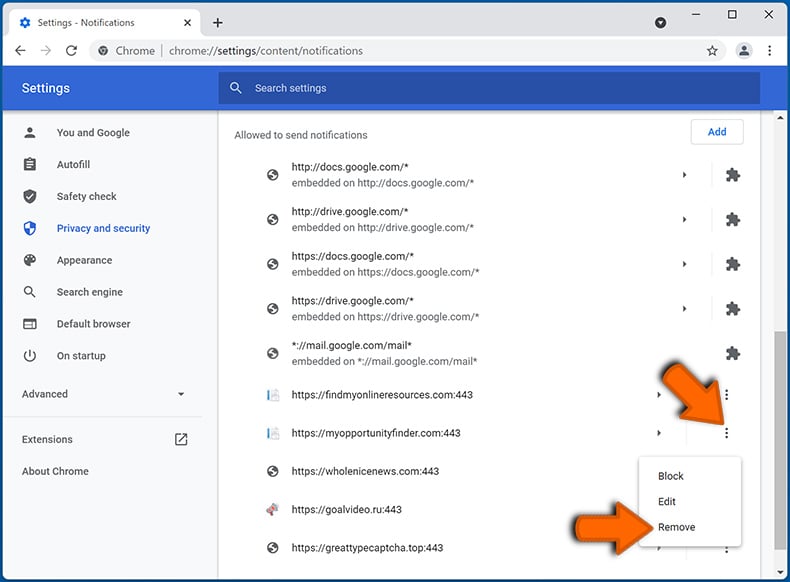
In the "Allowed to send notifications" list search for websites that you want to stop receiving notifications from. Click on the three dots icon near the website URL and click "Block" or "Remove" (if you click "Remove" and visit the malicious site once more, it will ask to enable notifications again).
 Remove spam notifications from Google Chrome (Android):
Remove spam notifications from Google Chrome (Android):
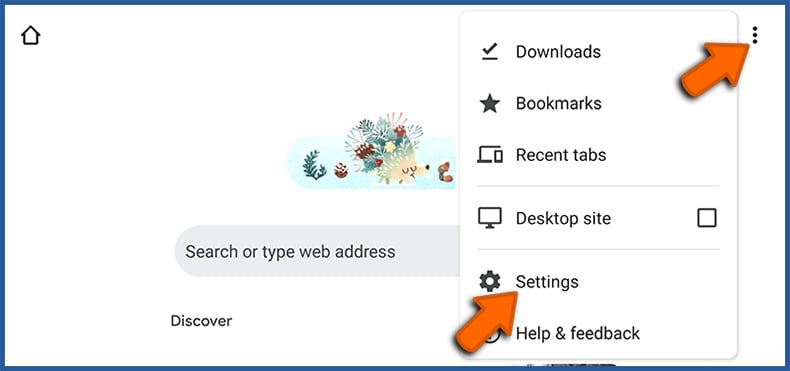
Tap the Menu button (three dots) on the right upper corner of the screen and select "Settings". Scroll down, tap on "Site settings" and then "Notifications".
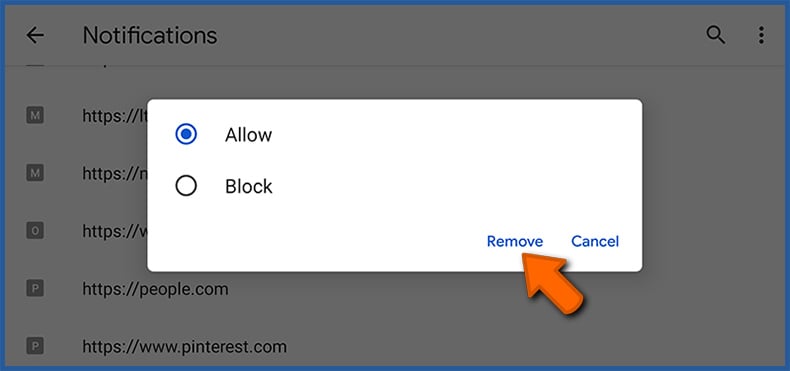
In the opened window, locate all suspicious URLs and tap on them one-by-one. Once the pop-up shows up, select either "Block" or "Remove" (if you tap "Remove" and visit the malicious site once more, it will ask to enable notifications again).
 Remove spam notifications from Mozilla Firefox:
Remove spam notifications from Mozilla Firefox:
Click the Menu button (three bars) on the right upper corner of the screen. Select "Settings" and click on "Privacy & Security" in the toolbar on the left hand side of the screen. Scroll down to the "Permissions" section and click the "Settings" button next to "Notifications".
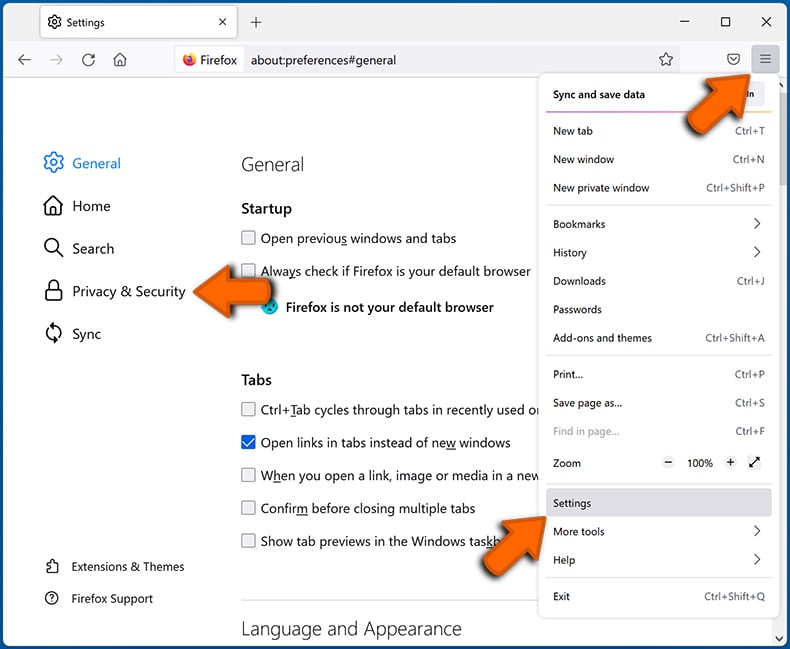
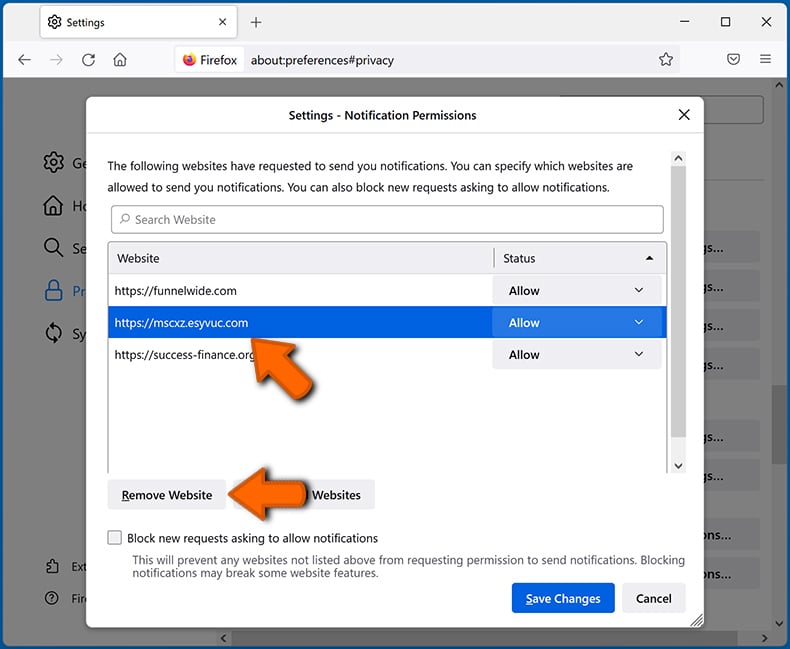
In the opened window, locate all suspicious URLs and block them using the drop-down menu or either remove them by clicking "Remove Website" at the bottom of the window (if you click "Remove Website" and visit the malicious site once more, it will ask to enable notifications again).
 Remove spam notifications from Microsoft Edge:
Remove spam notifications from Microsoft Edge:
Click the menu button (three dots) on the right upper corner of the Edge window and select "Settings". Click on "Cookies and site permissions" in the toolbar on the left hand side of the screen and select "Notifications".
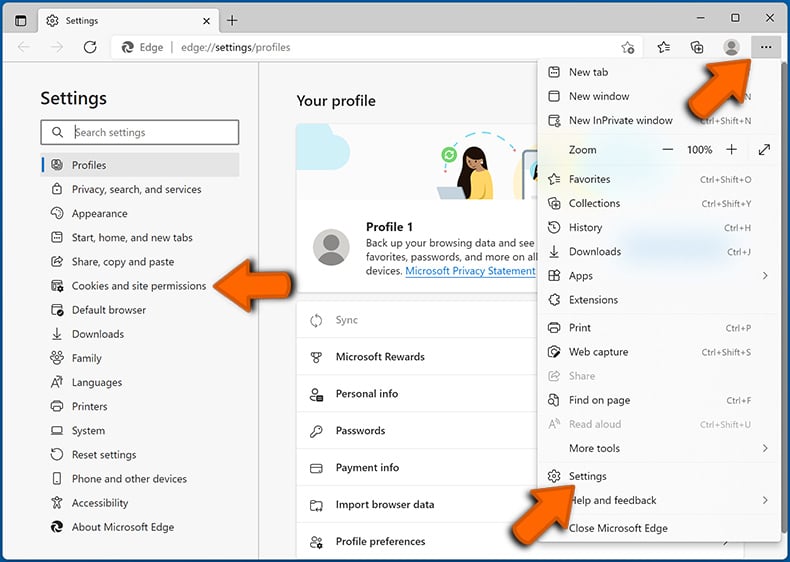
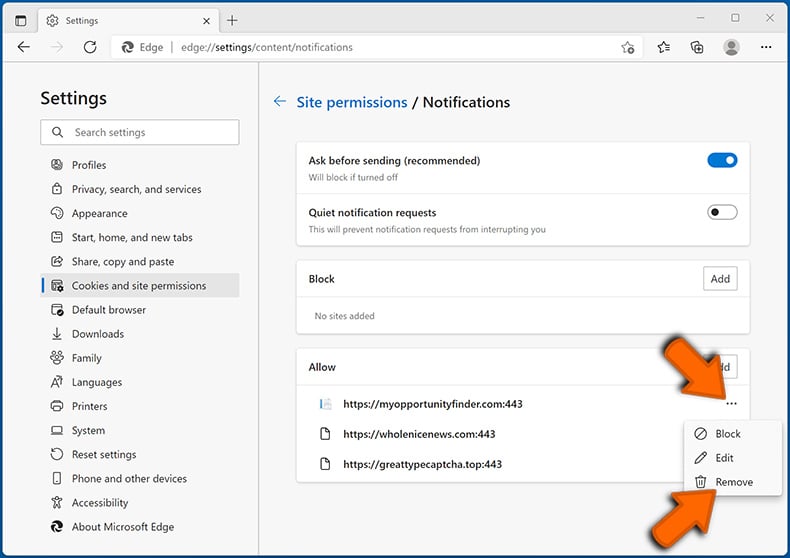
Click three dots on the right hand side of each suspicious URL under "Allow" section and click "Block" or "Remove" (if you click "Remove" and visit the malicious site once more, it will ask to enable notifications again).
 Remove spam notifications from Safari (macOS):
Remove spam notifications from Safari (macOS):
Click "Safari" button on the left upper corner of the screen and select "Preferences...". Select the "Websites" tab and then select "Notifications" section on the left pane.
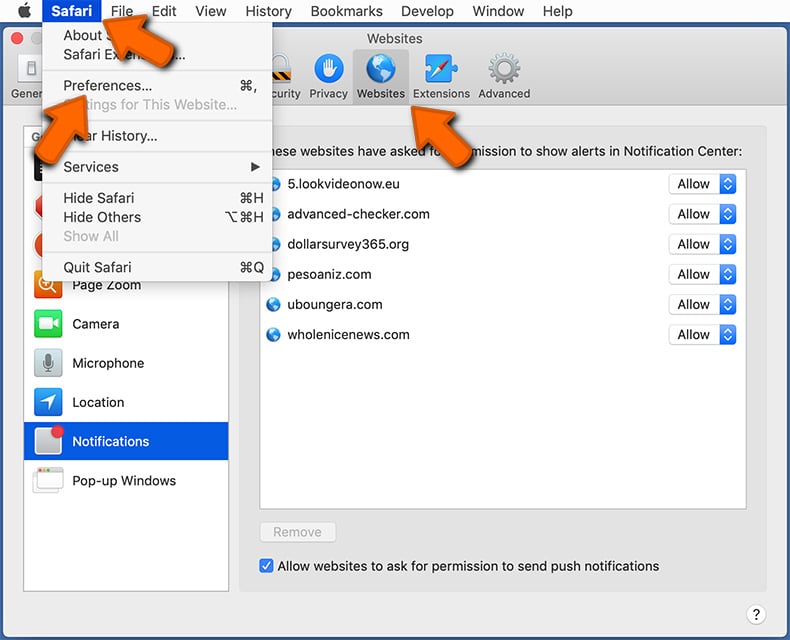
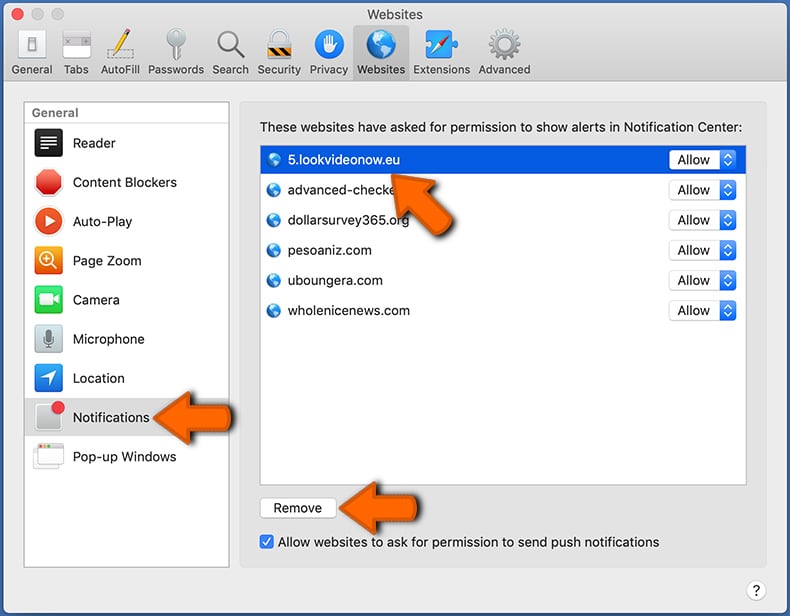
Check for suspicious URLs and apply the "Deny" option using the drop-down menu or either remove them by clicking "Remove" at the bottom of the window (if you click "Remove" and visit the malicious site once more, it will ask to enable notifications again)
How to avoid browser notification spam?
Internet users should be very skeptical when being asked to allow notifications. While this is a useful feature that allows you to receive timely news from websites you like, deceptive marketers frequently abuse it.
Only allow notifications from websites that you fully trust. For added security - use an anti-malware application with a real-time web browsing monitor to block shady websites that tries to trick you into allowing spam notifications. We recommend using Combo Cleaner Antivirus for Windows.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion