Do not call the numbers provided in the BazarCall email campaign
Phishing/ScamAlso Known As: BazaCall scam
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is BazarCall scam?
BazarCall is the name of the email campaign used with the purpose to trick recipients into installing malware on their computers. Cybercriminals behind this campaign send subscription-themed emails encouraging recipients to call the provided phone number to cancel or renew a subscription plan.
After calling the provided number, recipients are usually asked to visit a malicious website and download a file designed to install malware. Research shows that the BazarCall campaign is used to distribute BazarLoader malware that provides the attackers backdoor access to the infected computers.
It is possible that this campaign is used to deliver other malicious software as well.
BazarCall scam overview
There are multiple BazarCall campaign variants used to trick recipients into infecting their computers with BazarLoader (or other malware). The main differences between them are the number that recipients are asked to call and the name of a company name cybercriminals use as a disguise.
It is known that one email is disguised as a letter from Paradise Books asking to call the +1-816-307-4271 number, and another one disguised as a letter Medical Reminder Service asking to call the +1-816-897-0374 number. Although, it is likely that there are other variants with different company names and telephone numbers.
The main purpose of these emails is to trick recipients into believing that some subscription is expiring soon/trial period is almost over and calling the provided number to extend or cancel that subscription. Once called, the scam can vary.
Often (following a potentially lengthy conversation concerning verification, cancellation, security, etc.) victims are asked to visit a website, then download and execute (open) a file. If the file is infectious, once opened - it triggers malware download/installation processes.
Research shows that at least one of the websites is hosting a malicious Microsoft Excel document designed to install BazarLoader. Nevertheless, those pages may be designed to download other files designed to install other malware.
BazarLoader functions as a backdoor trojan - it installs additional malware. It is known that one of the malicious programs that this trojan is used to distribute is the RYUK ransomware.
Ransomware is a type of malware that encrypts files and keeps them inaccessible unless victims decrypt them with a decryption tool purchased from the attackers. Although, BazarLoader may be used to distribute other ransomware, cryptocurrency miners, remote access trojans, etc.
Typically, cybercriminals use malware like BazarLoader to distribute malicious software designed to encrypt files, steal personal information, mine cryptocurrency, or provide the attackers a remote access to the infected computer.
However, users may be asked to download a legitimate file, such as an installer for a remote access tool (e.g., AnyDesk, TeamViewer, UltraViewer, etc.). Scammers can use various excuses to access victims' devices, e.g., aid with refund processes, security checks, malware/hacker removal, etc. The end result is often an actual malware infection, but it can also be accompanied by fake fees or other scams aimed to extract money from victims.
In most cases, recipients who fall for these scams become victims of identity theft, suffer monetary loss, lose access to personal accounts, files stored on their computers, and (or) encounter other problems. Therefore, emails of this type have to be ignored and reported.
| Name | BazarCall (BazaCall) Scam |
| Threat Type | Phishing, Scam, Social Engineering |
| Fake Claim | Subscription plan is expiring soon/trial period is almost over |
| Related Domains | getmers[.]us, worldbooks[.]us, justpayless[.]net |
| Detection Names (getmers[.]us) | BitDefender (Malware), CRDF (Malicious), ESET (Malware), Fortinet (Malware), Full List Of Detections (VirusTotal) |
| Serving IP Address (getmers[.]us) | 162.255.119.132 |
| Detection Names (worldbooks[.]us) | CyRadar (Malicious), ESTsecurity-Threat Inside (Malicious), Fortinet (Malware), Full List Of Detections (VirusTotal) |
| Serving IP Address (worldbooks[.]us) | 103.224.212.222 |
| Detection Names (justpayless[.]net) | Certego (Malicious), CRDF (Malicious), CyRadar (Malicious), ESET (Malware), Fortinet (Malware), Full List Of Detections (VirusTotal) |
| Serving IP Address (justpayless[.]net) | 8.211.2.246 |
| Detection Names (subscription_1618608166.xlsb) | Avast (Other:Malware-gen [Trj]), BitDefender (Trojan.Agent.FFXL), ESET-NOD32 (A Variant Of Generik.HNQJYDZ), Kaspersky (HEUR:Trojan.MSOffice.Stratos.gen), Microsoft (TrojanDownloader:O97M/EncDoc.AVP!MTB), Full List Of Detections (VirusTotal) |
| Disguise | Letter from Paradise Books, Medical Reminder Service |
| Scammer Numbers | +1-816-897-0374, +1-816-307-4271 |
| Symptoms | Unauthorized online purchases, changed online account passwords, identity theft, illegal access of the computer. |
| Distribution methods | Deceptive emails, rogue online pop-up ads, search engine poisoning techniques, misspelled domains. |
| Damage | Loss of sensitive private information, monetary loss, identity theft. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Similar spam campaign examples
Another example of an email scam used to trick users into calling the provided number and then downloading a malicious file designed to infect computers with malware is "Your Free Trial Period Is Almost Over Email Scam" (this article contains a number of examples of emails used to trick recipients into installing the BazarLoader malware).
Other examples of similar email spam campaigns include "Apple Invoice email scam", "Windows Defender email scam", "Geek Squad email scam", "Windows Defender Advanced Threat Protection email scam", and countless others.
As a rule, cybercriminals behind such emails pretend to be legitimate companies, organizations, service providers, or other genuine entities.
How do spam campaigns infect computers?
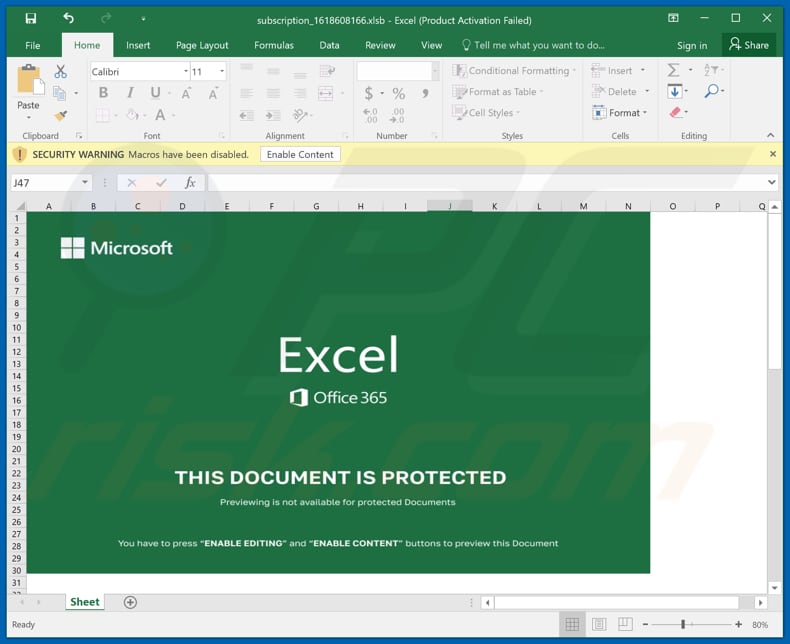
It is known that one of the files used to distribute BazarLoader via the BazarCall campaign is a malicious Microsoft Excel document. That document installs malicious software only if users enable macros commands (editing/content).
Although, malicious documents opened with Microsoft Office versions released before Microsoft Office 2010 install malware without asking to enable macros commands. It is because those versions do not have the "Protected View" mode, which prevents malicious documents from installing malware right after they are opened.
More examples of files that cybercriminals may use to deliver malware are executable files (e.g., EXE), JavaScript files, PDF documents, other Microsoft Word documents, ZIP, RAR, and other archive files. As mentioned in the first paragraph, BazarLoader is not the only malware that cybercriminals may distribute via BazarCall campaign.
How to avoid installation of malware?
Avoid opening files downloaded from questionable websites, via Peer-to-Peer networks, third-party downloaders, and so on. It is safe to open files or use programs that were downloaded from legitimate pages and via direct links.
Another important thing is not to open files or website links in irrelevant emails that are received from suspicious or unknown senders. Quite often, emails of this kind contain malicious files, links designed to deliver malware. Installed operating system and software should be kept up to date.
It has to be achieved using implemented functions, tools provided by the official developers. It is strongly recommended not to trust any other tools (unofficial, third-party updaters, or 'cracking' tools).
It is common that those tools are bundled with malware. Another detail about 'cracking' tools is that it is illegal to use them to bypass software activation.
Additionally, it is advisable to scan the operating system for viruses regularly and do it using reputable antivirus or ant-spyware software. If you've already opened malicious attachments, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
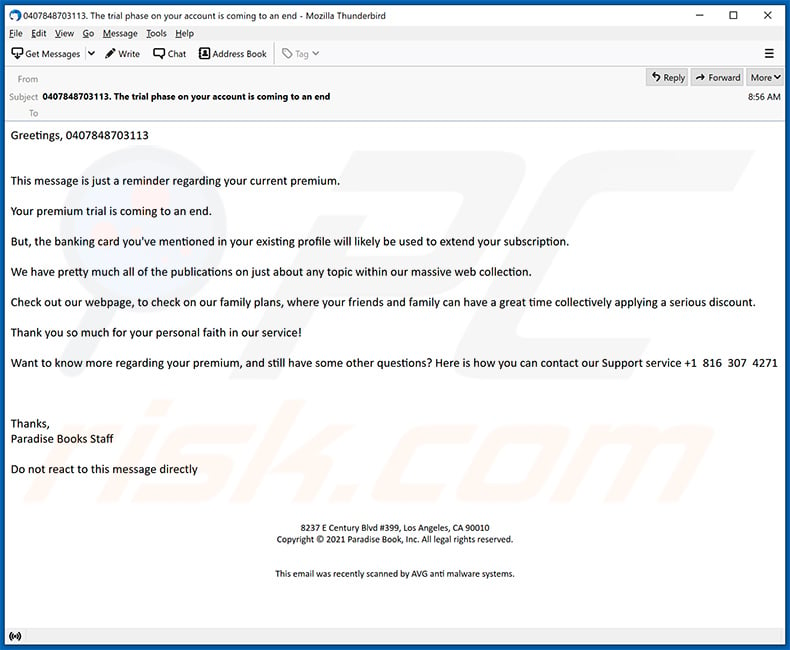
Text presented in the main BazarCall email:
Subject: 0407848703113. The trial phase on your account is coming to an end
Greetings, 0407848703113
This message is just a reminder regarding your current premium.Your premium trial is coming to an end.
But, the banking card you've mentioned in your existing profile will likely be used to extend your subscription.
We have pretty much all of the publications on just about any topic within our massive web collection.
Check out our webpage, to check on our family plans, where your friends and family can have a great time collectively applying a serious discount.
Thank yoou so much for your personal faith in our service!
Want to know more regarding your premium, and still have some other questions? Here is how you can contact our Support service +1 816 307 4271
Thanks,
Paradise Books StaffDo not react to this message directly
8237 E Century Blvd #399, Los Angeles, CA 90010
Copyright © 2021 Paradise Book, Inc. All legal rights reserved.
This email was recently scanned by AVG anti malware systems.
Website used to distribute malware via this email variant:
Malicious Excel document designed to install BazarLoader:
Screenshot of the second BazarCall email variant:
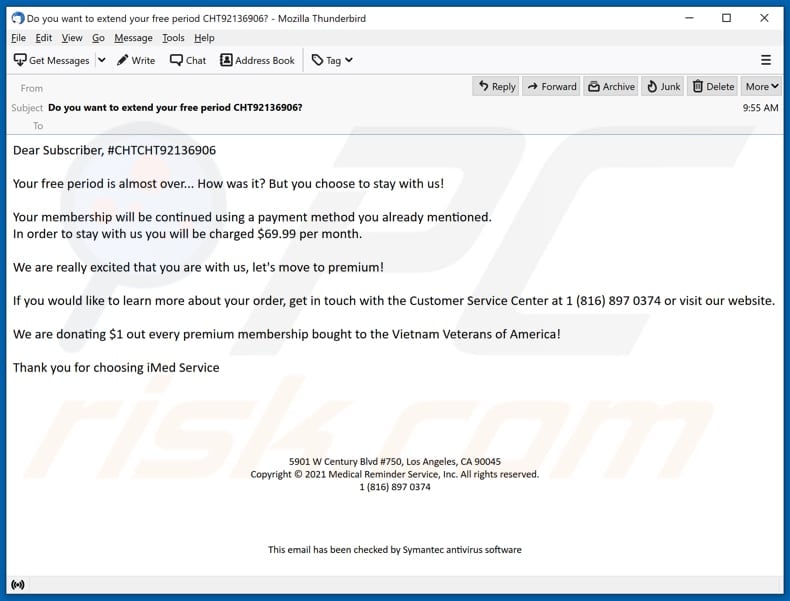
Text in this variant:
Subject: Do you want to extend your free period CHT92136906?
Dear Subscriber, #CHTCHT92136906
Your free period is almost over... How was it? But you choose to stay with us!
Your membership will be continued using a payment method you already mentioned.
In order to stay with us you will be charged $69.99 per month.We are really excited that you are with us, let's move to premium!
If you would like to learn more about your order, get in touch with the Customer Service Center at 1 (816) 897 0374 or visit our website.
We are donating $1 out every premium membership bought to the Vietnam Veterans of America!
Thank you for choosing iMed Service
Website used to distribute malware via this variant:
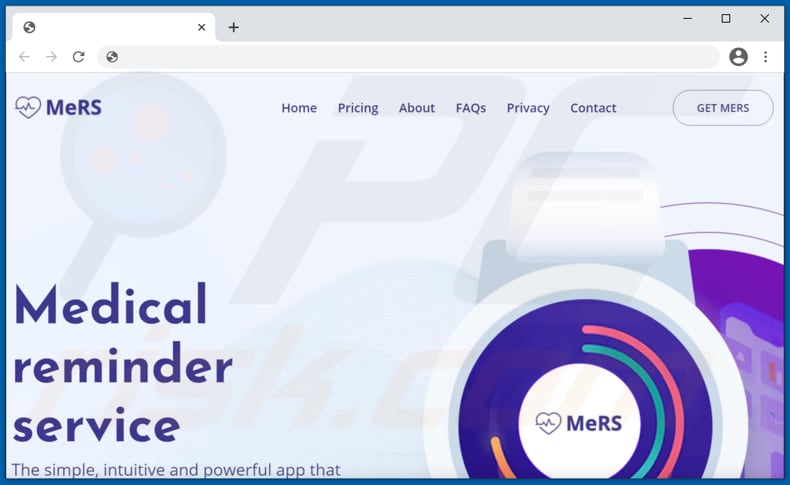
Here's a video of a malware researcher trying to contact cyber criminals behind this email scam. Crooks eventually attempt to trick the caller into downloading and opening a malicious MS Excel document designed to inject BazarLoader malware into the system:
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is BazarCall scam?
- STEP 1. Manual removal of possible malware infections.
- STEP 2. Check if your computer is clean.
How to remove malware manually?
Manual malware removal is a complicated task - usually it is best to allow antivirus or anti-malware programs to do this automatically. To remove this malware we recommend using Combo Cleaner Antivirus for Windows.
If you wish to remove malware manually, the first step is to identify the name of the malware that you are trying to remove. Here is an example of a suspicious program running on a user's computer:
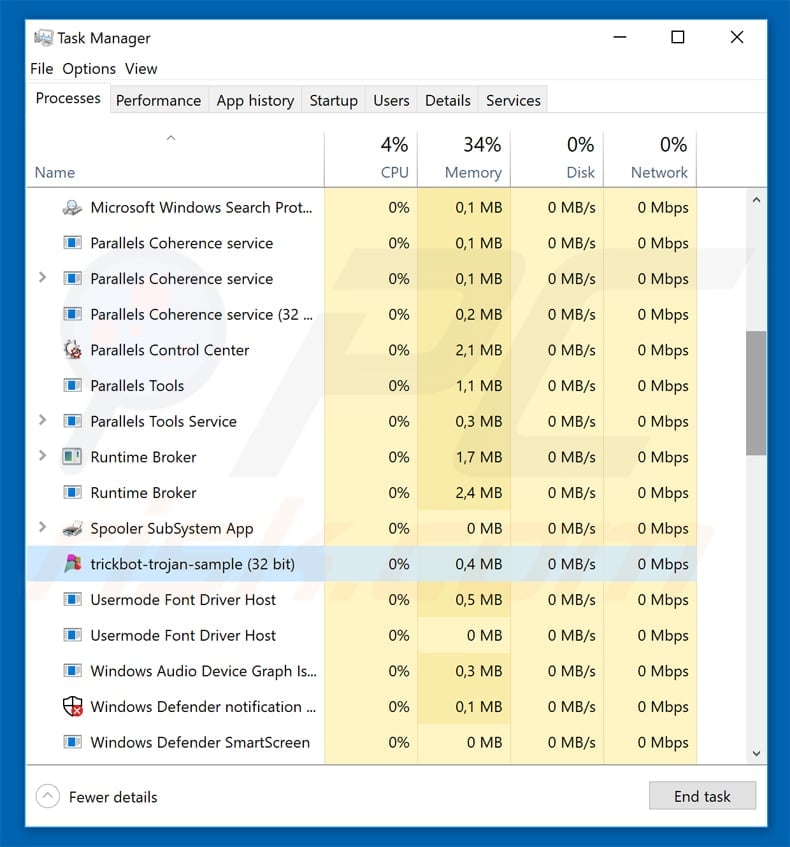
If you checked the list of programs running on your computer, for example, using task manager, and identified a program that looks suspicious, you should continue with these steps:
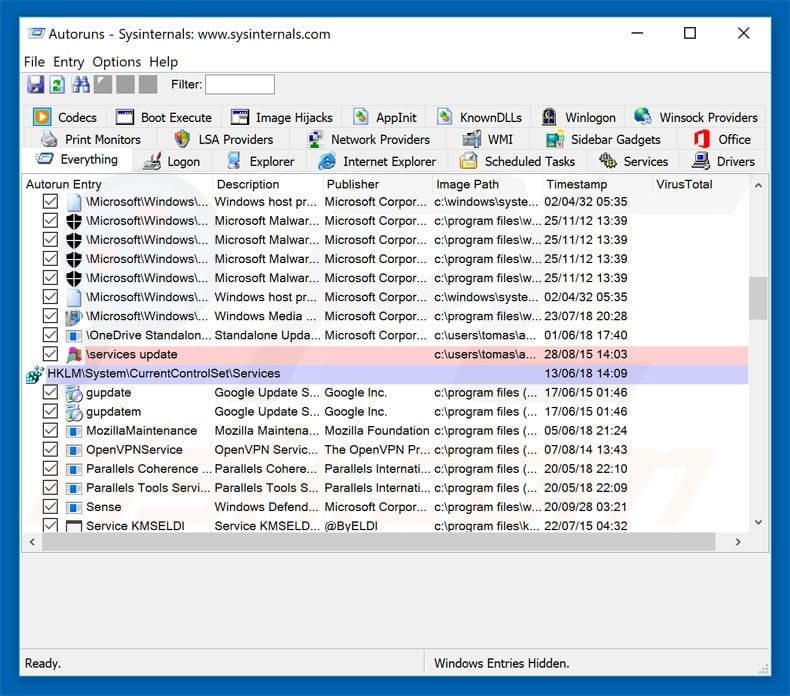
 Download a program called Autoruns. This program shows auto-start applications, Registry, and file system locations:
Download a program called Autoruns. This program shows auto-start applications, Registry, and file system locations:
 Restart your computer into Safe Mode:
Restart your computer into Safe Mode:
Windows XP and Windows 7 users: Start your computer in Safe Mode. Click Start, click Shut Down, click Restart, click OK.
During your computer start process, press the F8 key on your keyboard multiple times until you see the Windows Advanced Option menu, and then select Safe Mode with Networking from the list.
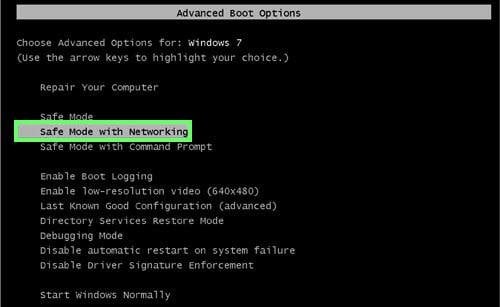
Video showing how to start Windows 7 in "Safe Mode with Networking":
Windows 8 users: Start Windows 8 is Safe Mode with Networking - Go to Windows 8 Start Screen, type Advanced, in the search results select Settings. Click Advanced startup options, in the opened "General PC Settings" window, select Advanced startup.
Click the "Restart now" button. Your computer will now restart into the "Advanced Startup options menu". Click the "Troubleshoot" button, and then click the "Advanced options" button.
In the advanced option screen, click "Startup settings". Click the "Restart" button. Your PC will restart into the Startup Settings screen. Press F5 to boot in Safe Mode with Networking.
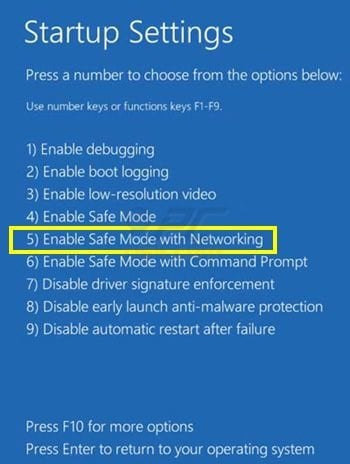
Video showing how to start Windows 8 in "Safe Mode with Networking":
Windows 10 users: Click the Windows logo and select the Power icon. In the opened menu click "Restart" while holding "Shift" button on your keyboard. In the "choose an option" window click on the "Troubleshoot", next select "Advanced options".
In the advanced options menu select "Startup Settings" and click on the "Restart" button. In the following window you should click the "F5" button on your keyboard. This will restart your operating system in safe mode with networking.
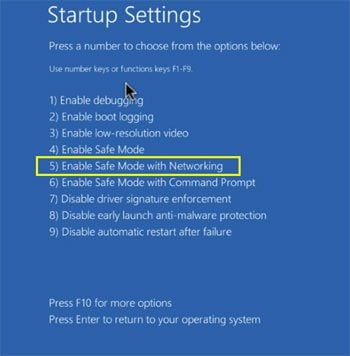
Video showing how to start Windows 10 in "Safe Mode with Networking":
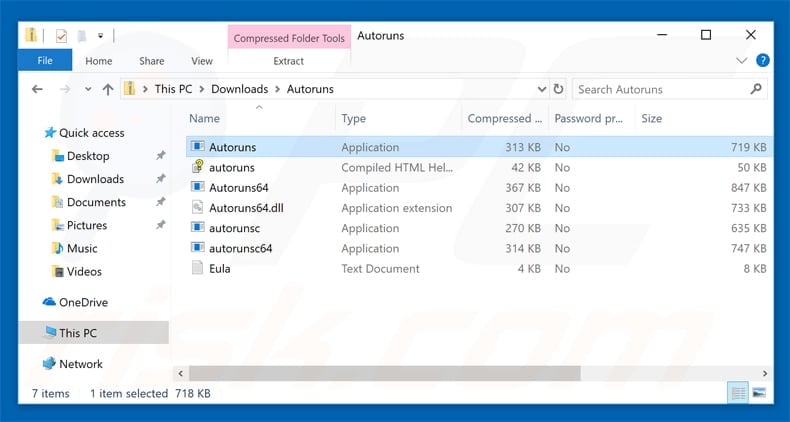
 Extract the downloaded archive and run the Autoruns.exe file.
Extract the downloaded archive and run the Autoruns.exe file.
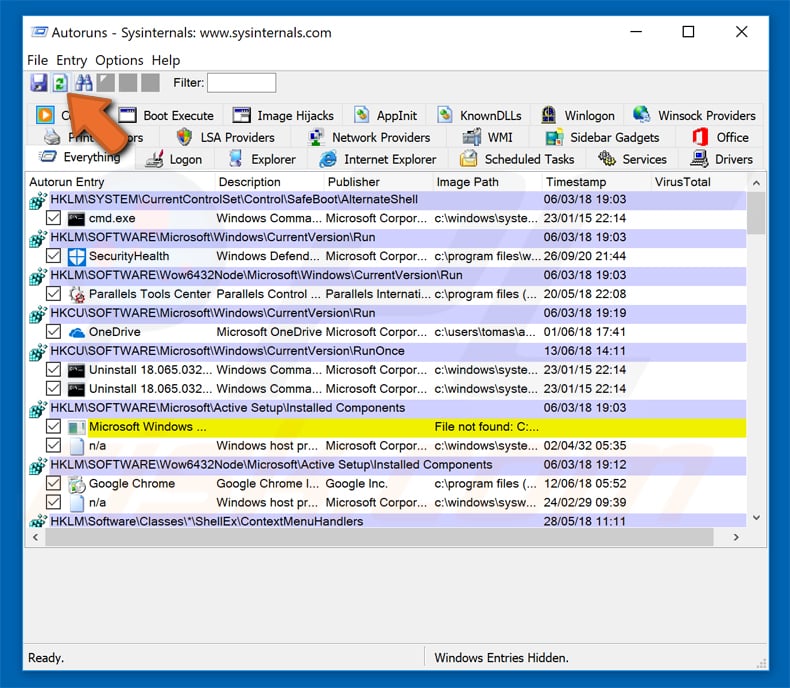
 In the Autoruns application, click "Options" at the top and uncheck "Hide Empty Locations" and "Hide Windows Entries" options. After this procedure, click the "Refresh" icon.
In the Autoruns application, click "Options" at the top and uncheck "Hide Empty Locations" and "Hide Windows Entries" options. After this procedure, click the "Refresh" icon.
 Check the list provided by the Autoruns application and locate the malware file that you want to eliminate.
Check the list provided by the Autoruns application and locate the malware file that you want to eliminate.
You should write down its full path and name. Note that some malware hides process names under legitimate Windows process names. At this stage, it is very important to avoid removing system files.
After you locate the suspicious program you wish to remove, right click your mouse over its name and choose "Delete".
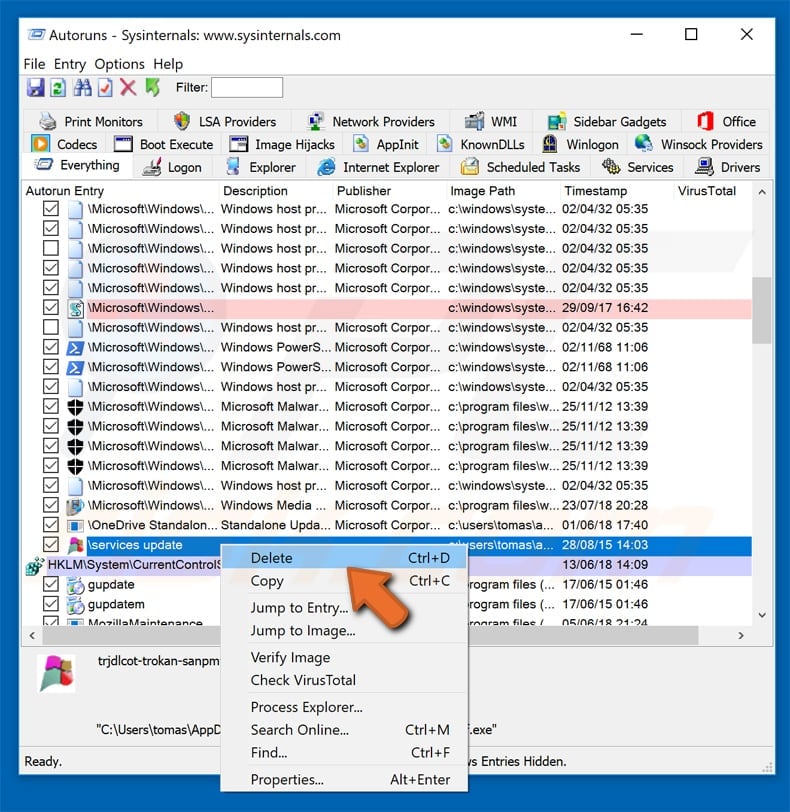
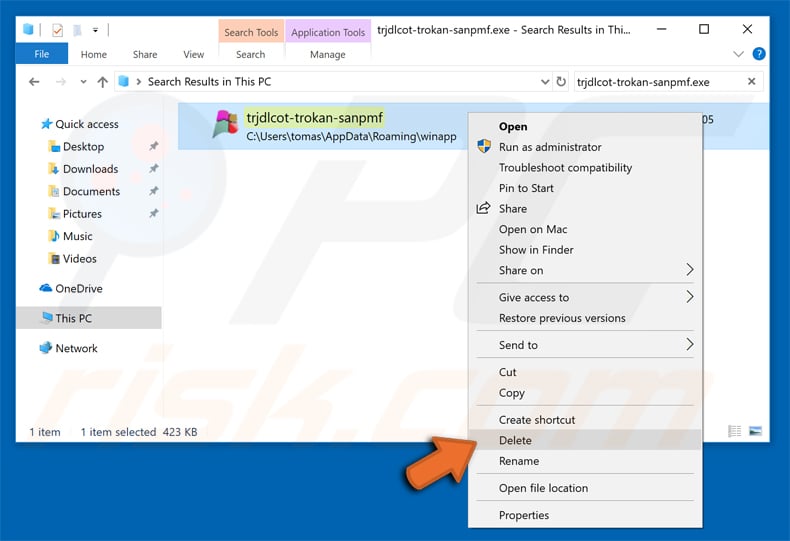
After removing the malware through the Autoruns application (this ensures that the malware will not run automatically on the next system startup), you should search for the malware name on your computer.
Be sure to enable hidden files and folders before proceeding. If you find the filename of the malware, be sure to remove it.
Reboot your computer in normal mode. Following these steps should remove any malware from your computer. Note that manual threat removal requires advanced computer skills.
If you do not have these skills, leave malware removal to antivirus and anti-malware programs. These steps might not work with advanced malware infections.
As always it is best to prevent infection than try to remove malware later. To keep your computer safe, install the latest operating system updates and use antivirus software.
To be sure your computer is free of malware infections, we recommend scanning it with Combo Cleaner Antivirus for Windows.
Frequently Asked Questions (FAQ)
Why did I receive this email?
This mail is not personal; thousands of users receive identical emails.
I have provided my personal information when tricked by a scam, what should I do?
If you have disclosed account credentials - immediately change the passwords of all potentially compromised accounts and inform their official support. And if you've provided other private data (e.g., ID card details, credit card numbers, etc.) - contact the appropriate authorities without delay.
I have allowed cyber criminals to remotely access my computer, what should I do?
If you have allowed cyber criminals to access your device remotely, you must first disconnect it from the Internet. Afterward, uninstall the remote access software that the criminals used (e.g., TeamViewer, UltraViewer, AnyDesk, etc.) since they may not need your permission to reconnect. Lastly, use an anti-virus to perform a full system scan and remove all detected threats.
I have read a scam email but didn't open any files promoted through it, is my computer infected?
No, merely reading/opening an email will not trigger any system infection processes. Devices are infected when malicious files or links are opened/clicked.
I have downloaded and opened a file promoted through a scam email, is my computer infected?
Whether your system was infected might depend on the opened file's format. If it was a malicious executable (.exe, .run, etc.) - most likely, yes - your device was infected. However, you might have avoided an infection if it was a document (.doc, .pdf, .xls, etc.). Virulent files in these formats can require extra interactions (e.g., enabling macro commands) to begin downloading/installing malware.
Will Combo Cleaner remove malware infections?
Yes, Combo Cleaner is designed to detect and remove threats. It can eliminate most of the known malware infections. Keep in mind that running a full system scan is essential - as sophisticated malicious programs tend to hide deep within systems.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion