Avoid getting scammed by sites claiming that your iPhone has been hacked
Mac VirusAlso Known As: "Your Device Apple iPhone Has Been Hacked" pop-up
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is "Your Device Apple iPhone Has Been Hacked"?
"Your Device Apple iPhone Has Been Hacked" is a scam that our researchers discovered while inspecting dubious websites. As the name implies, it claims that the visitor's iPhone has been infected and hacked.
It must be emphasized that no site can detect such (or other) issues on users' devices - therefore, any that make such claims are scams. Additionally, it has to be stressed that this deceptive content is in no way associated with the actual Apple Inc. despite being presented as an alert from "AppleCare Plus/ Protection System".
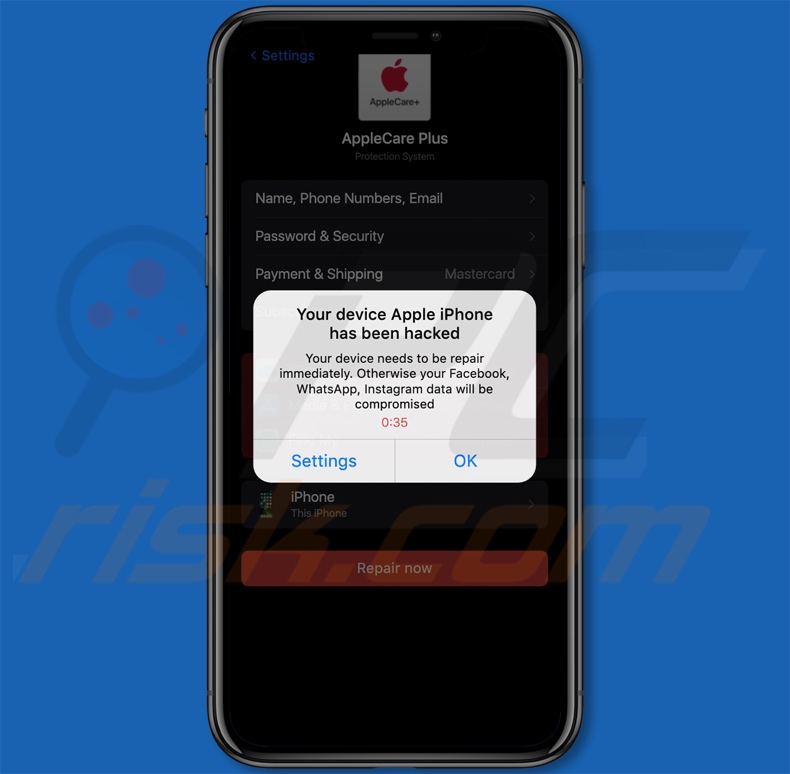
Your Device Apple iPhone Has Been Hacked overview
When we accessed a webpage promoting this scam, it displayed a pop-up stating that the visitor's Apple iPhone has been hacked and that the hackers are currently monitoring all activities.
After this window was closed, the page presented us with another one. This one informed that the device requires immediate repair - else the user risks their Facebook, WhatsApp, and Instagram data being compromised.
The background page was disguised as an "AppleCare Plus/ Protection System" settings list that contained a whole host of sensitive data categories and marked "iCloud", "Media & Purchases", and "Find My" app/services as "Compromised". When we pressed the "Repair now" button at the bottom of the page, it resulted in a redirect to an application promoted by this scam.
As mentioned in the introduction, all the claims made by "Your Device Apple iPhone Has Been Hacked" are false. In most cases, scams of this kind are used to push unreliable and harmful software, e.g., adware, browser hijackers, fake anti-viruses, and various PUAs.
We have even observed instances of this scam model being used to distribute trojans, ransomware, cryptominers, and other malware. Some fake virus alerts also operate as phishing scams.
It must be mentioned that scammers may use this deceptive content to endorse genuine products/services in the hopes of receiving illegitimate commissions. However, there are no guarantees that a scam will continue to promote such content. Hence, we strongly recommend downloading only from official and verified sources.
To summarize, by trusting scams like "Your Device Apple iPhone Has Been Hacked" - users may experience system infections, severe privacy issues, financial losses, and even identity theft.
| Name | "Your Device Apple iPhone Has Been Hacked" pop-up |
| Threat Type | Phishing, Scam, Mac malware, Mac virus |
| Fake Claim | iPhone has been hacked and sensitive data is at risk. |
| Related Domains | linkthetrafficmedia[.]com |
| Detection Names (linkthetrafficmedia[.]com) | N/A (VirusTotal) |
| Serving IP Address (linkthetrafficmedia[.]com) | 104.21.94.70 |
| Symptoms | Your Mac becomes slower than normal, you see unwanted pop-up ads, you are redirected to dubious websites. |
| Distribution methods | Deceptive pop-up ads, free software installers (bundling), fake Flash Player installers, torrent file downloads. |
| Damage | Internet browser tracking (potential privacy issues), display of unwanted ads, redirects to dubious websites, loss of private information. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Similar scam examples
We have analyzed thousands of online scams; "You May Have Viruses On After Visiting An Adult Website", "Apple Security Center scam", and "McAfee - Your iPhone is infected with 5 viruses!" are merely a few examples of ones thematically similar to "Your Device Apple iPhone Has Been Hacked".
The Internet is rife with deceptive and malicious material. In addition to virus/hacker warnings, other scam models include outdated software alerts, reward programs, lotteries, giveaways, undelivered package notifications, etc. Due to how widespread scams are, we highly recommend being vigilant when browsing.
How did I open a scam website?
Scam sites are often accessed via others that use rogue advertising networks. The former can be force-open immediately upon access or when hosted content is clicked (i.e., ads, buttons, links, text input fields, etc.). Additionally, misspelling a website's URL can result in a redirect (or a redirection chain leading) to a deceptive webpage.
Spam browser notifications and intrusive adverts promote scams as well. Adware can also display advertisements endorsing this content and/or force-open sites that host it.
How to avoid visiting scam websites?
Deceptive websites are most commonly entered via redirects caused by pages using rogue advertising networks, mistyped URLs, spam browser notifications, intrusive ads, and installed adware.
Therefore, we advise against using sites that offer pirated software/media or other suspect services (e.g., Torrenting, illegal streaming or downloading, etc.) since they are usually monetized via rogue advertising networks. It is important to take note of website URLs and be careful when entering them.
To avoid receiving unwanted browser notifications, do not permit dubious webpages to deliver them (i.e., do not click "Allow", "Allow Notifications", etc.). We recommend ignoring or denying notification delivery requests (i.e., pressing "Block", "Block Notifications", etc.).
And to avoid inadvertently permitting bundled/harmful software into the system, we advise researching software and downloading it only from official/verified channels. Furthermore, when installing, it is essential to read terms, study available options, use the "Custom/Advanced" settings, and opt-out of all supplementary apps, extensions, tools, etc.
If your device is already infected, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate all threats.
Appearance of the initial pop-up displayed the "Your Device Apple iPhone Has Been Hacked" scam:
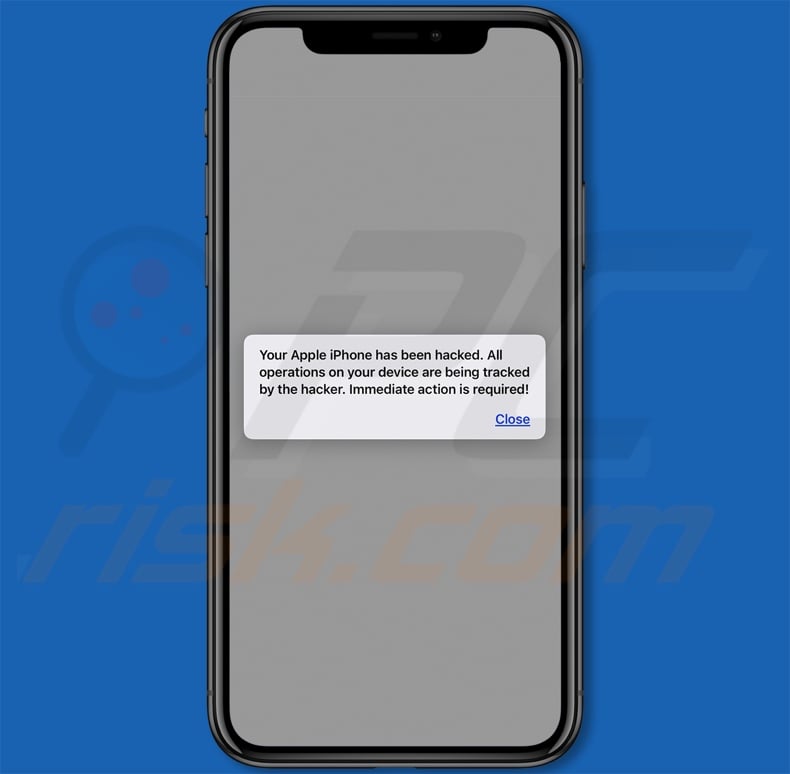
Text presented within the scam's pop-ups:
Initial pop-up:
Your Apple iPhone has been hacked. All operations on your device are being tracked by the hacker. Immediate action is required!
---------------
Second pop-up:
Your device Apple iPhone has been hacked
Your device needs to be repair immediately. Otherwise your Facebook, WhatsApp, Instagram data will be compromised
Appearance of the scam's background page:

Text presented on this page:
AppleCare Plus
Protection System
Name, Phone Numbers, Email
Password & Security
Payment & Shipping Mastercard
Subscriptions
iCloud Compromised
Media & Purchases Compromised
Find My Compromised
iPhone
This iPhone
Repair now
Appearance of the app promoted by the "Your Device Apple iPhone Has Been Hacked" scam:
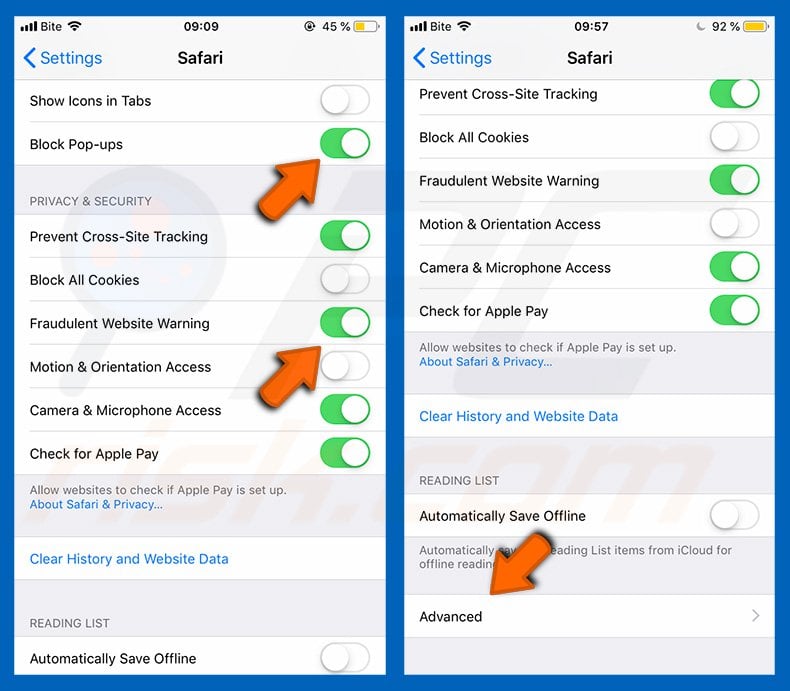
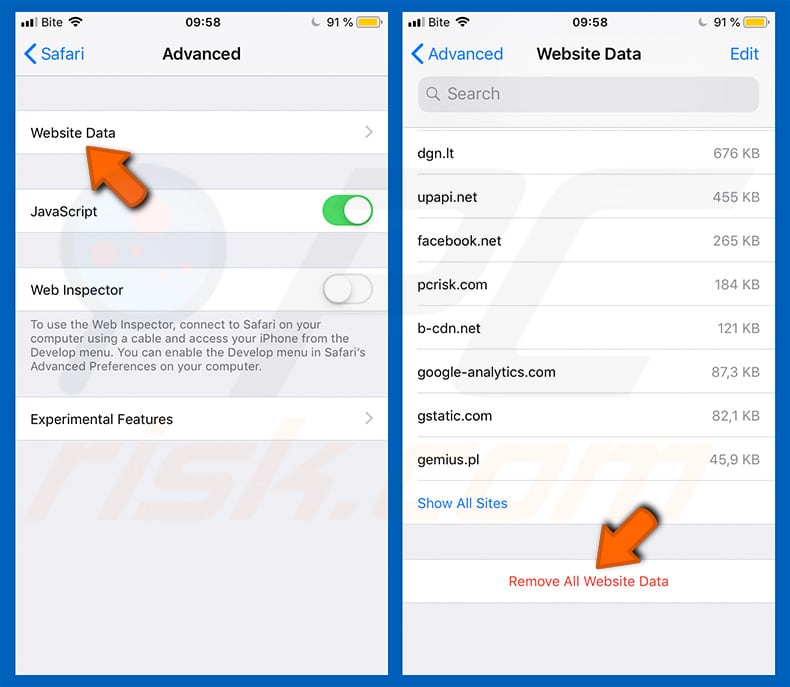
To enable pop-up blocking, fraudulent website warnings, and remove web browsing data in mobile Apple devices, follow these steps:
First, go to "Settings", and then scroll down to find and tap "Safari".

Check if the "Block Pop-ups" and "Fraudulent Website Warning" toggles are enabled. If not, enable them immediately. Then, scroll down and tap "Advanced".
Tap "Website Data" and then "Remove All Website Data".
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is "Your Device Apple iPhone Has Been Hacked"?
- STEP 1. Remove PUA related files and folders from OSX.
- STEP 2. Remove rogue extensions from Safari.
- STEP 3. Remove rogue add-ons from Google Chrome.
- STEP 4. Remove potentially unwanted plug-ins from Mozilla Firefox.
Video showing how to remove adware and browser hijackers from a Mac computer:
Potentially unwanted applications removal:
Remove potentially unwanted applications from your "Applications" folder:
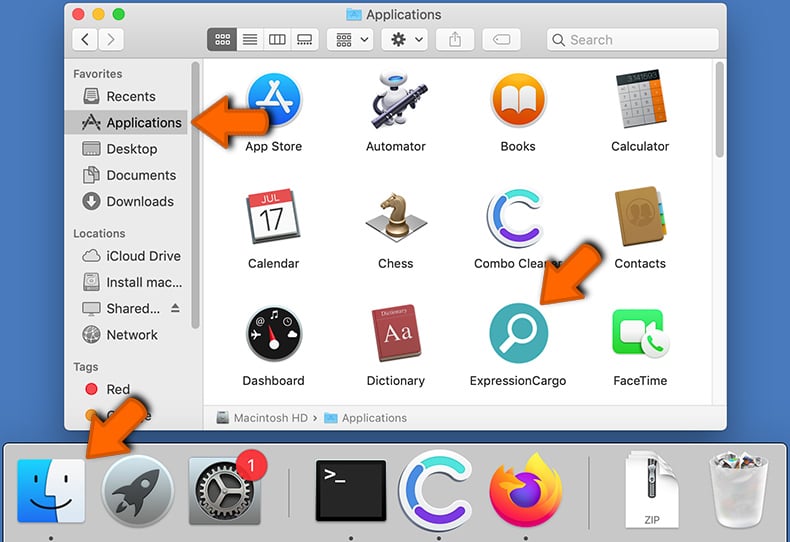
Click the Finder icon. In the Finder window, select "Applications". In the applications folder, look for "MPlayerX","NicePlayer", or other suspicious applications and drag them to the Trash. After removing the potentially unwanted application(s) that cause online ads, scan your Mac for any remaining unwanted components.
DOWNLOAD remover for malware infections
Combo Cleaner checks if your computer is infected with malware. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Remove adware-related files and folders
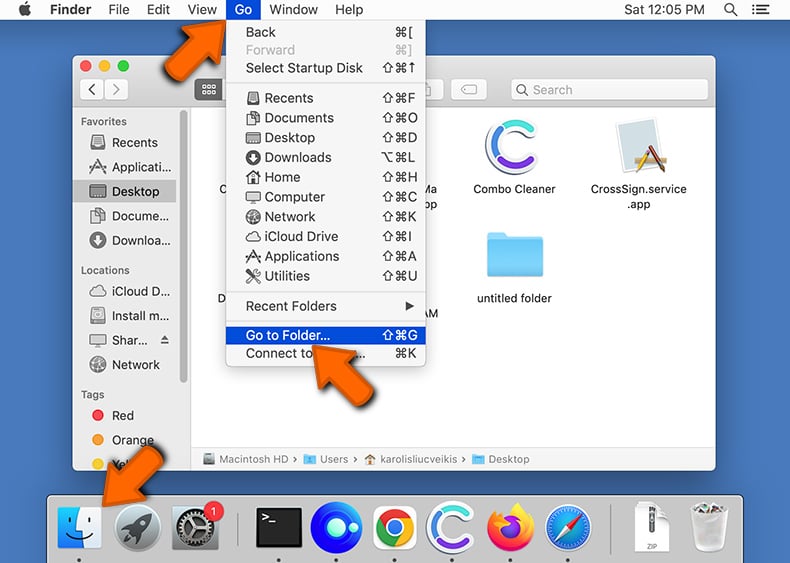
Click the Finder icon, from the menu bar. Choose Go, and click Go to Folder...
 Check for adware generated files in the /Library/LaunchAgents/ folder:
Check for adware generated files in the /Library/LaunchAgents/ folder:
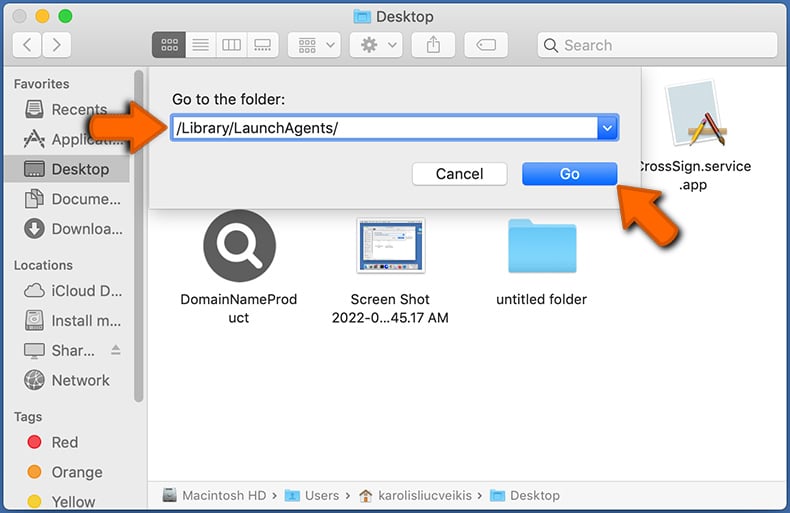
In the Go to Folder... bar, type: /Library/LaunchAgents/
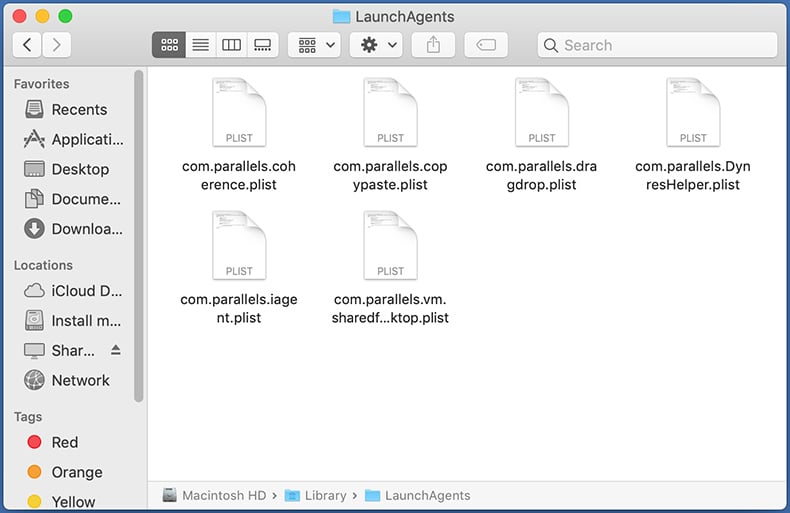
In the "LaunchAgents" folder, look for any recently-added suspicious files and move them to the Trash. Examples of files generated by adware - "installmac.AppRemoval.plist", "myppes.download.plist", "mykotlerino.ltvbit.plist", "kuklorest.update.plist", etc. Adware commonly installs several files with the exact same string.
 Check for adware generated files in the ~/Library/Application Support/ folder:
Check for adware generated files in the ~/Library/Application Support/ folder:
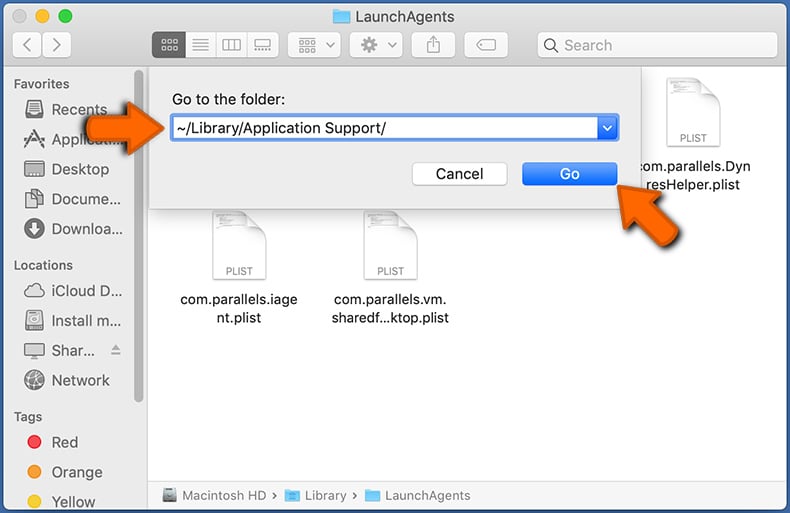
In the Go to Folder... bar, type: ~/Library/Application Support/
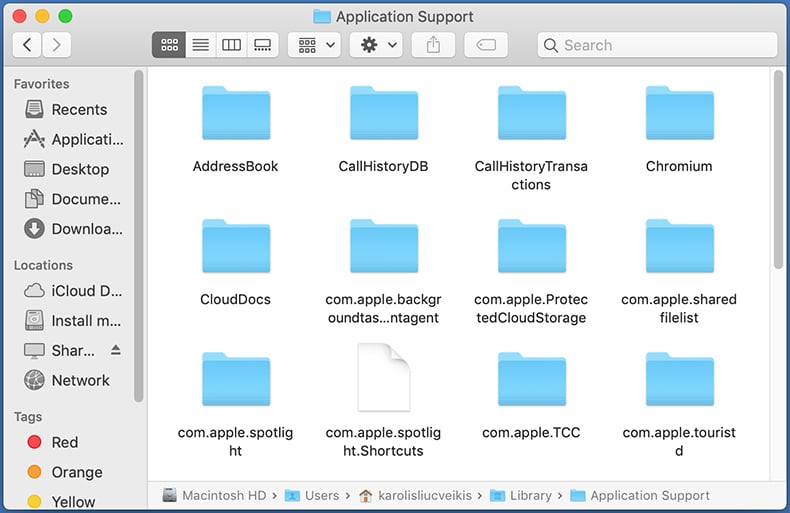
In the "Application Support" folder, look for any recently-added suspicious folders. For example, "MplayerX" or "NicePlayer", and move these folders to the Trash.
 Check for adware generated files in the ~/Library/LaunchAgents/ folder:
Check for adware generated files in the ~/Library/LaunchAgents/ folder:
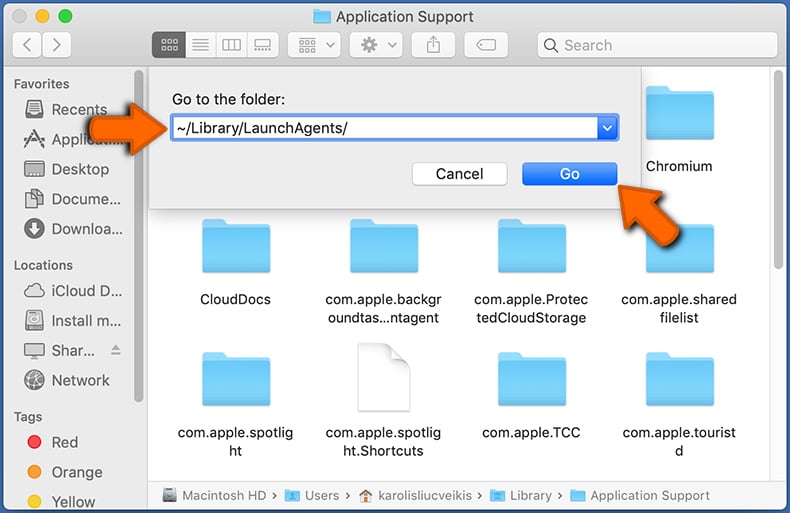
In the Go to Folder... bar, type: ~/Library/LaunchAgents/
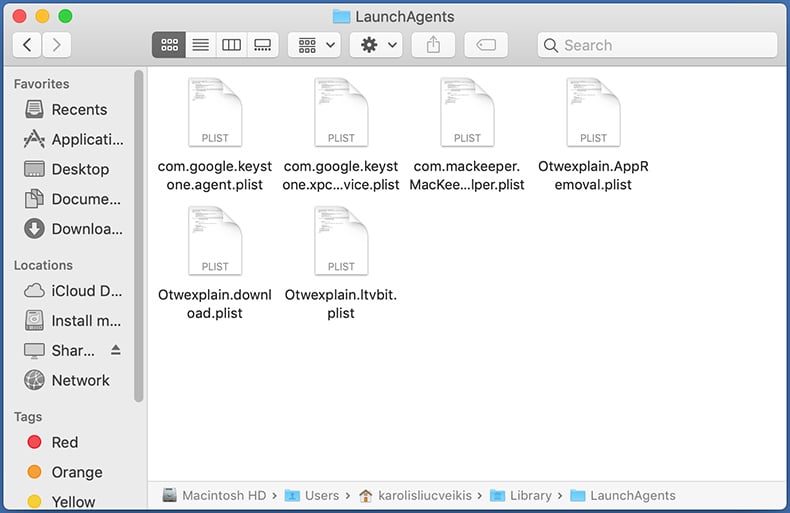
In the "LaunchAgents" folder, look for any recently-added suspicious files and move them to the Trash. Examples of files generated by adware - "installmac.AppRemoval.plist", "myppes.download.plist", "mykotlerino.ltvbit.plist", "kuklorest.update.plist", etc. Adware commonly installs several files with the exact same string.
 Check for adware generated files in the /Library/LaunchDaemons/ folder:
Check for adware generated files in the /Library/LaunchDaemons/ folder:
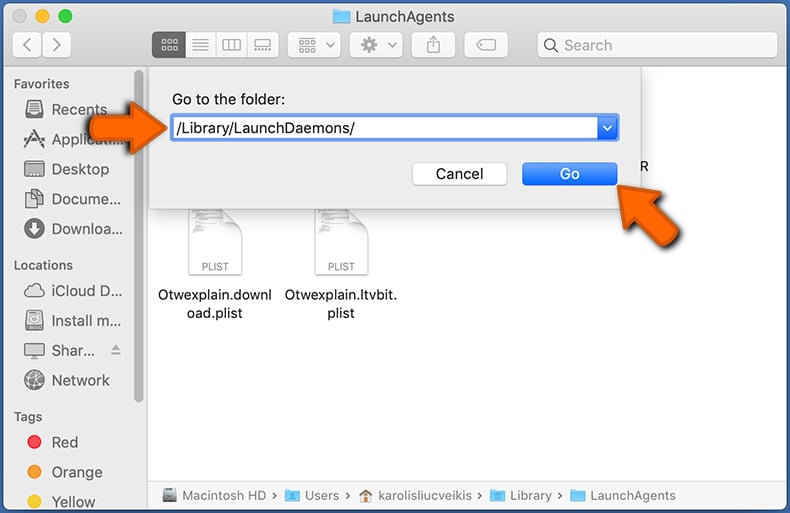
In the "Go to Folder..." bar, type: /Library/LaunchDaemons/
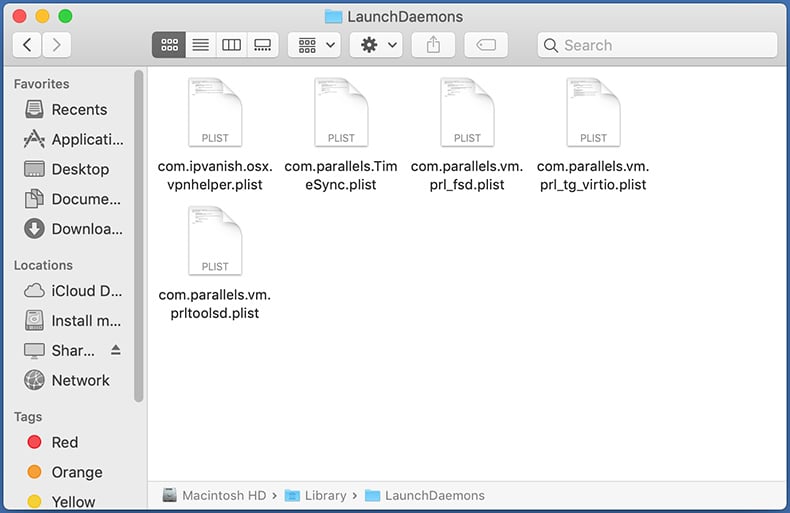
In the "LaunchDaemons" folder, look for recently-added suspicious files. For example "com.aoudad.net-preferences.plist", "com.myppes.net-preferences.plist", "com.kuklorest.net-preferences.plist", "com.avickUpd.plist", etc., and move them to the Trash.
 Scan your Mac with Combo Cleaner:
Scan your Mac with Combo Cleaner:
If you have followed all the steps correctly, your Mac should be clean of infections. To ensure your system is not infected, run a scan with Combo Cleaner Antivirus. Download it HERE. After downloading the file, double click combocleaner.dmg installer. In the opened window, drag and drop the Combo Cleaner icon on top of the Applications icon. Now open your launchpad and click on the Combo Cleaner icon. Wait until Combo Cleaner updates its virus definition database and click the "Start Combo Scan" button.
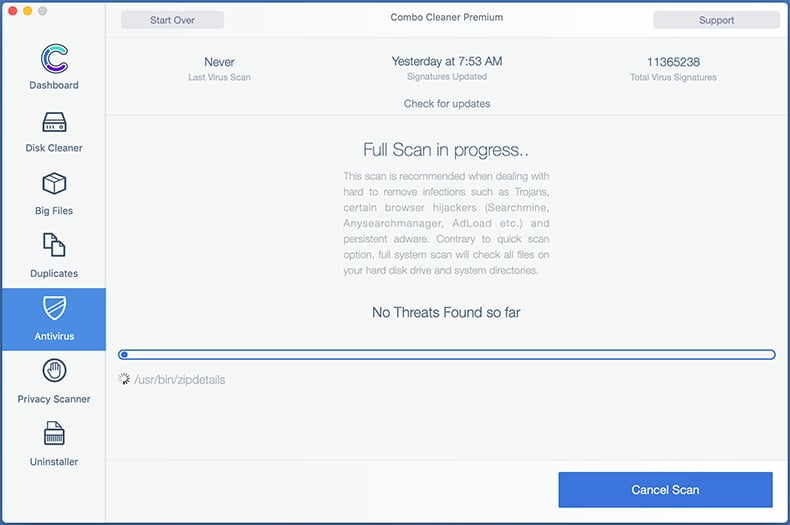
Combo Cleaner will scan your Mac for malware infections. If the antivirus scan displays "no threats found" - this means that you can continue with the removal guide; otherwise, it's recommended to remove any found infections before continuing.
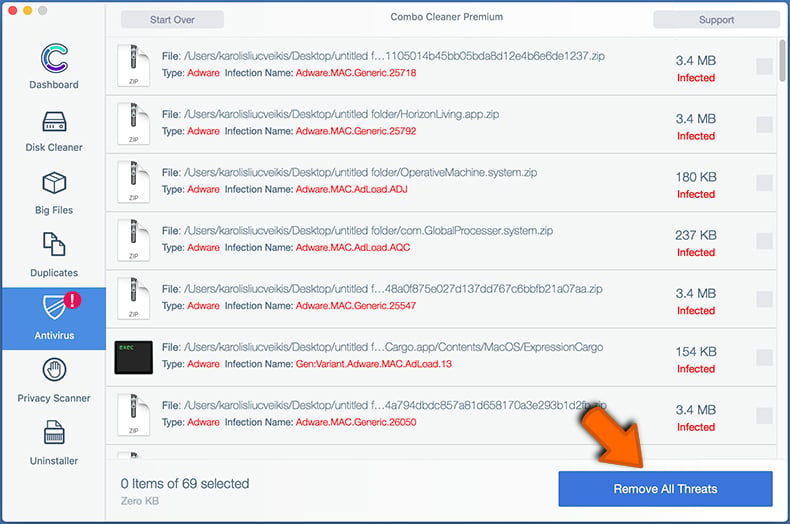
After removing files and folders generated by the adware, continue to remove rogue extensions from your Internet browsers.
Remove malicious extensions from Internet browsers
 Remove malicious Safari extensions:
Remove malicious Safari extensions:
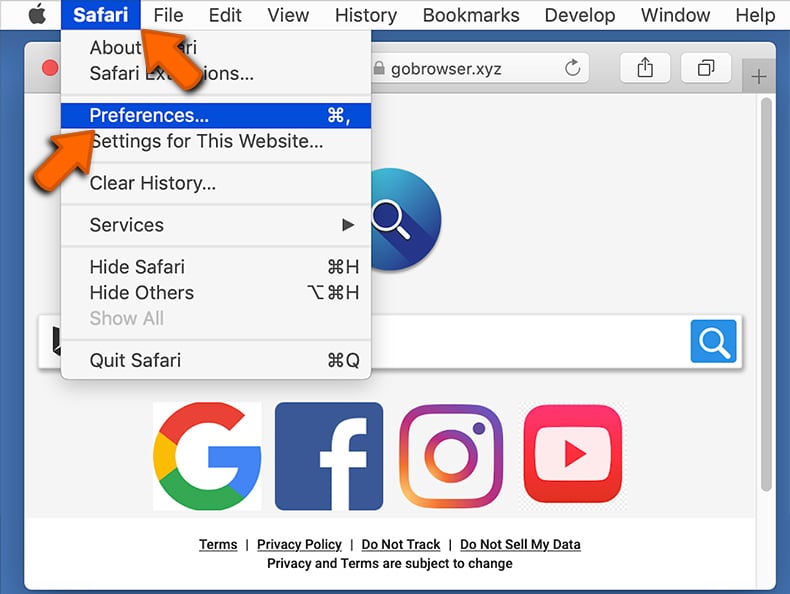
Open the Safari browser, from the menu bar, select "Safari" and click "Preferences...".
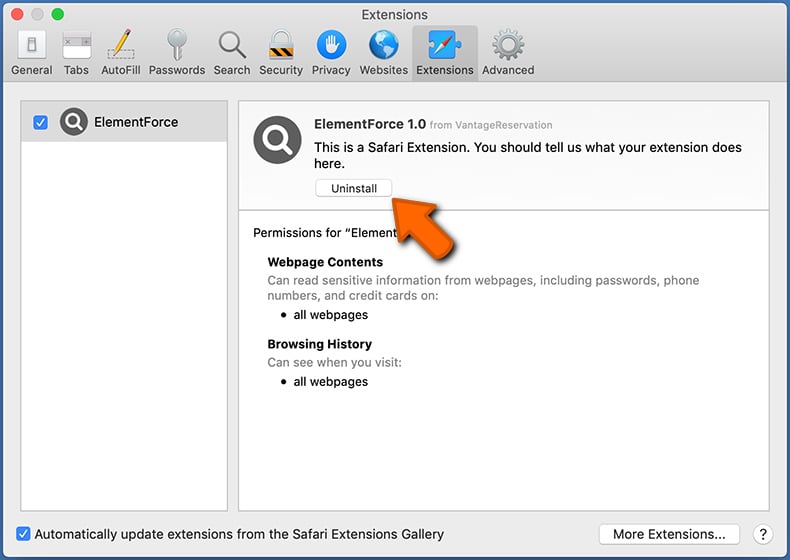
In the preferences window, select "Extensions" and look for any recently-installed suspicious extensions. When located, click the "Uninstall" button next to it/them. Note that you can safely uninstall all extensions from your Safari browser - none are crucial for regular browser operation.
- If you continue to have problems with browser redirects and unwanted advertisements - Reset Safari.
 Remove malicious extensions from Google Chrome:
Remove malicious extensions from Google Chrome:
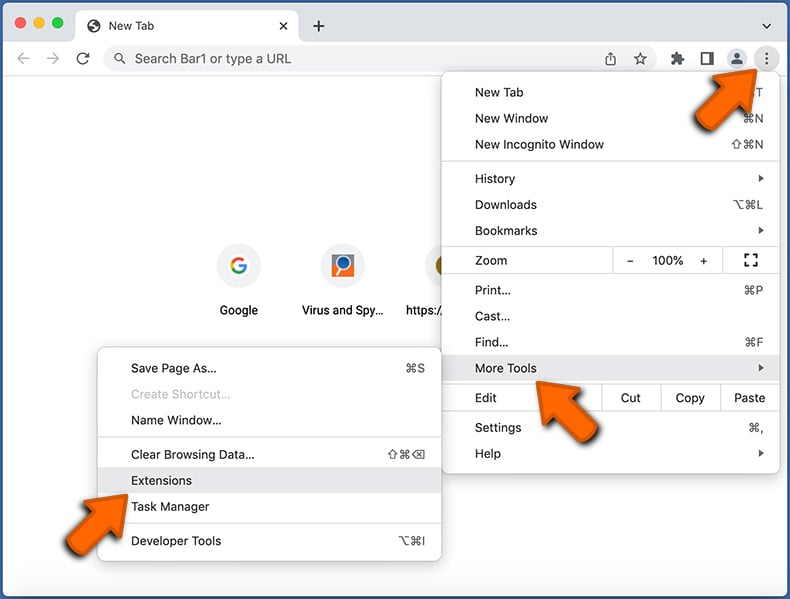
Click the Chrome menu icon ![]() (at the top right corner of Google Chrome), select "More Tools" and click "Extensions". Locate all recently-installed suspicious extensions, select these entries and click "Remove".
(at the top right corner of Google Chrome), select "More Tools" and click "Extensions". Locate all recently-installed suspicious extensions, select these entries and click "Remove".
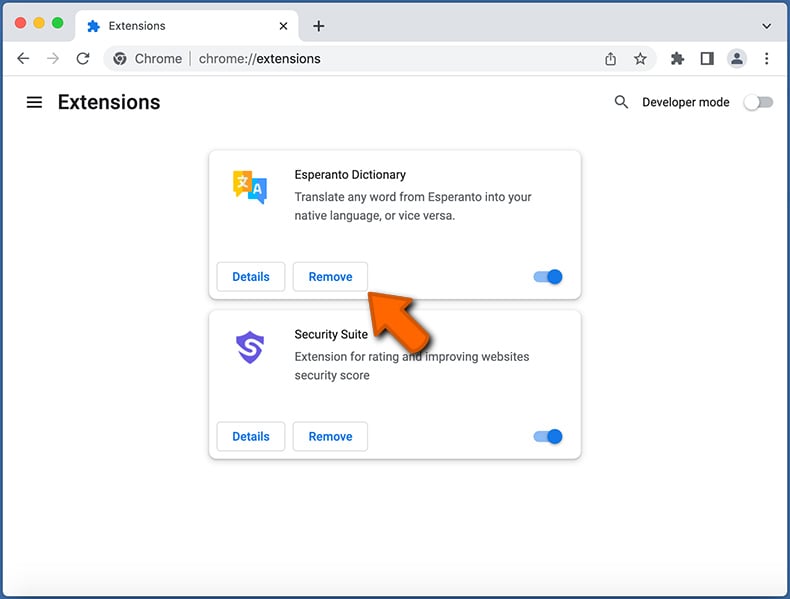
- If you continue to have problems with browser redirects and unwanted advertisements - Reset Google Chrome.
 Remove malicious extensions from Mozilla Firefox:
Remove malicious extensions from Mozilla Firefox:
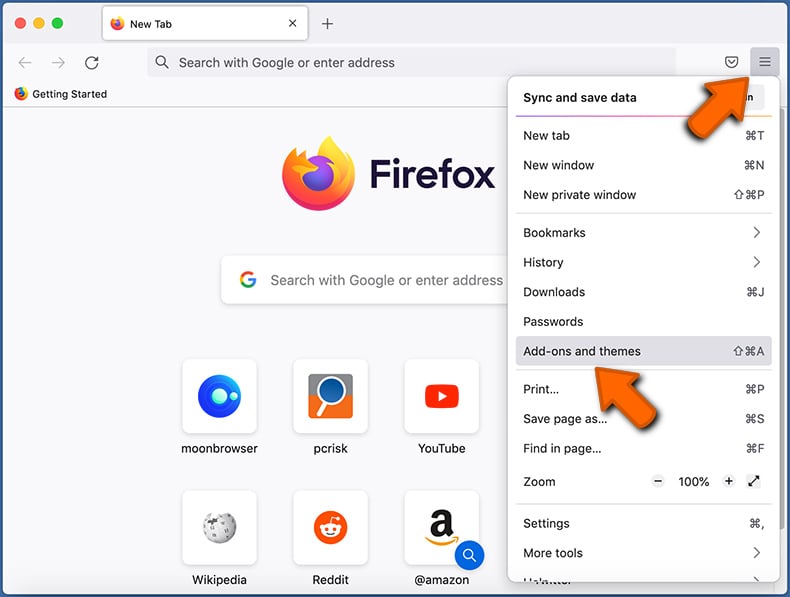
Click the Firefox menu ![]() (at the top right corner of the main window) and select "Add-ons and themes". Click "Extensions", in the opened window locate all recently-installed suspicious extensions, click on the three dots and then click "Remove".
(at the top right corner of the main window) and select "Add-ons and themes". Click "Extensions", in the opened window locate all recently-installed suspicious extensions, click on the three dots and then click "Remove".
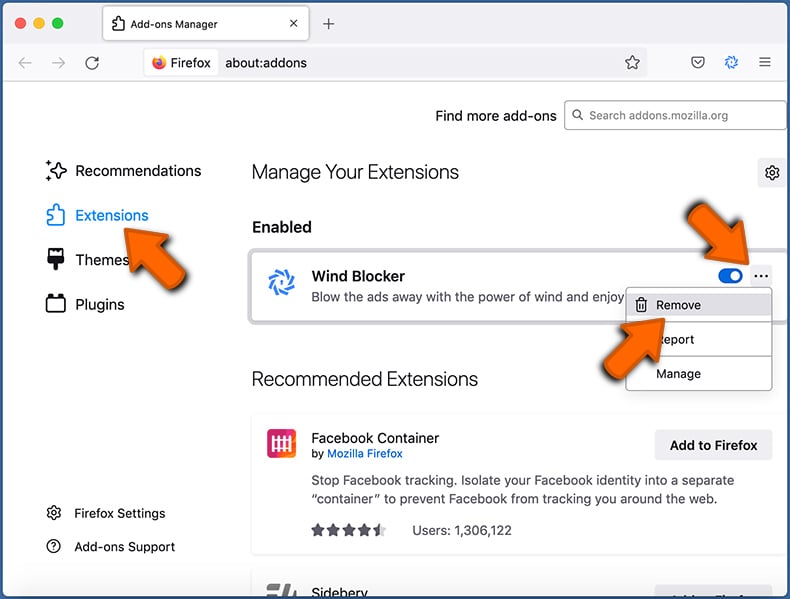
- If you continue to have problems with browser redirects and unwanted advertisements - Reset Mozilla Firefox.
Frequently Asked Questions (FAQ)
What is a pop-up scam?
Pop-up scams are deceptive messages designed to trick users into performing specific actions. For example, victims can be lured/scared into making monetary transactions, downloading/installing software, purchasing products/services, revealing vulnerable information, and so on.
What is the purpose of a pop-up scam?
The purpose of pop-up scams is to generate revenue. Scammers may profit by promoting software, obtaining funds through deception, abusing or selling private data, proliferating malware, and so forth.
I have provided my personal information when tricked by a scam, what should I do?
If you have disclosed account credentials - change the passwords of all potentially compromised accounts and inform their official support without delay. And if you have revealed other private data to scammers (e.g., ID card details, credit card numbers, etc.) - immediately contact the corresponding authorities.
Why do I encounter fake pop-ups?
Pop-up scams are promoted on rogue webpages. Users typically enter these pages through redirects caused by mistyped URLs, sites using rogue advertising networks, spam browser notifications, intrusive ads, or installed adware.
Will Combo Cleaner protect me from pop-up scams?
Combo Cleaner can scan visited websites and detect rogue/malicious ones (including those that promote scams). Hence, if you enter such a webpage - you will be warned immediately, and further access will be blocked.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion