Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is Security Defender?
Security Defender is a fake antivirus program, a scam released by cyber criminals, and should not be trusted. This fake antivirus software is designed to scare PC users into believing that their computers are infected with malware and viruses. To achieve this deceptive goal, Security Defender uses fake security scans, fake malware detection lists, and fake security warning messages.
The program usually installs on PCs without users' consent and then starts a security scan resulting in the detection of various 'high-risk spyware' threats. Furthermore, this rogue software modifies the registry entries of the infected operating system and blocks execution of installed software.
The creators of this scam intend to give the impression that the targeted PC is infected with high-risk malware and that Security Defender can offer a security software solution to fix these issues. In fact, none of the 'detected' viruses or malware exist on your computer - this bogus program is designed to make you believe otherwise in an attempt to sell its fake antivirus programs.
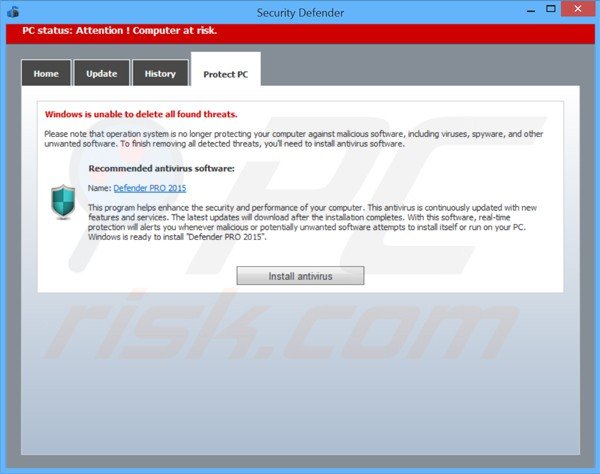
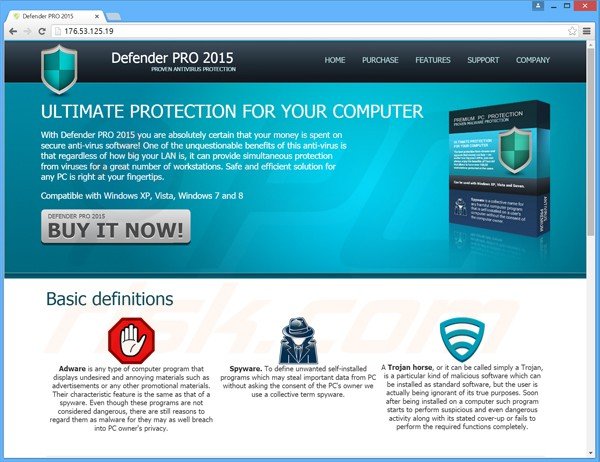
At time of testing, Security Defender encouraged computer users to purchase 'Defender PRO 2015'. Cyber criminals responsible for creating the Security Defender scam hope that PC users will believe the fake security scans performed by their rogue software and then purchase the programs offered.
None of the programs promoted by Security Defender are legitimate - computer users who pay for them will lose their money and their computers will remain infected.
The purpose of Security Defender distribution is to convince PC users into believing that their computers are at risk, and then to sell useless license keys. Paying for any program listed by Security Defender is equivalent to sending your money to cyber criminals - you will lose your money and divulge your banking information, potentially leading to further thefts from your account.
This fake antivirus program is usually distributed via fake online security scanners. These pop-ups are incorporated into malicious websites. Upon visiting these sites, PC users are presented with a message stating that their computers are infected and that they need to download and install antivirus software to remove the 'detected' infections.
Other deceptive methods of proliferating Security Defender include using fake software updates, fake video codecs, Trojans, and drive-by downloads. If you observe this program scanning your PC for security infections, ignore it and eliminate this scam from your PC.
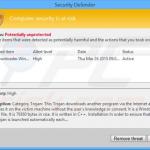
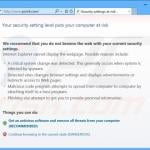
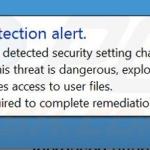
Security Defender generating fake security warning messages:
Your security setting level puts your computer at risk. We recommend that you do not browse the web with your current security settings. Internet Explorer cannot display the webpage. Possible reasons include: A critical system change was detected. This generally occurs when system is infected by spyware. Detected virus changes browser settings and displays advertisements or redirects access to Web pages. Malicious code program attempts to spread from computer to computer by attaching itself to a host program. Phishing site attempt to get you to provide personal information. Things you can do: Get an antivirus software and remove all threats from your computer (RECOMMENDED) Continue browsing in the current state (DANGEROUS).
Virus detection alert. System has detected security settings changes due to malware. This threat is dangerous, exploits the computer, and provides access to user files. A scan required to complete remediation.
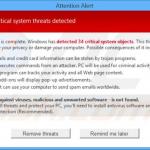
Critical system threats detected. System scan is complete. Windows has detected 34 critical system objects. These threats may compromise your privacy or damage your computer. Possible consequences of it include: Bank details and credit card information can be stolen by trojan programs. System executes commands from an attacker. PC will be used for criminal activity. Spyware program can track your activity and all Web page content. Browser add-ons will display pop-up advertisements. Spam-bot can use your computer to send spam emails worldwide. Protection against viruses, malicious and unwanted software - is not found. To remove all treats and protect your PC, you’ll need to install antivirus software and enable real-time protection.
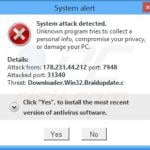
System attack detected. Unknown program tries to collect personal info, compromise your privacy, or damage your PC.
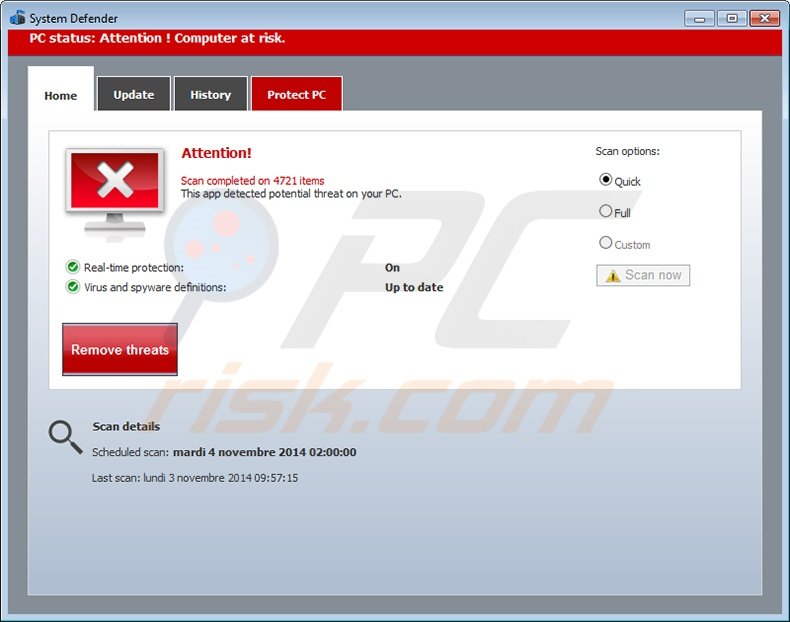
Security Defender rogue antivirus performing a fake computer security scan:
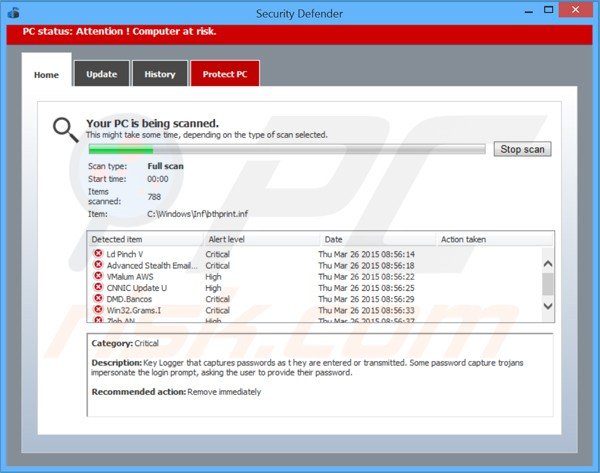
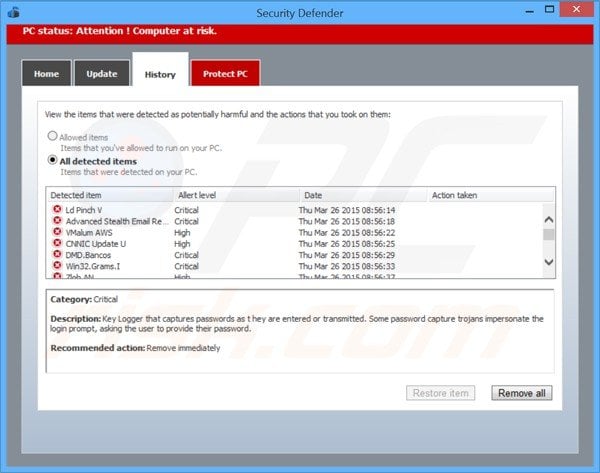
Security Defender generating lists of non-existent security infections to scare computer users into believing that their computers are infected with high-risk malware:
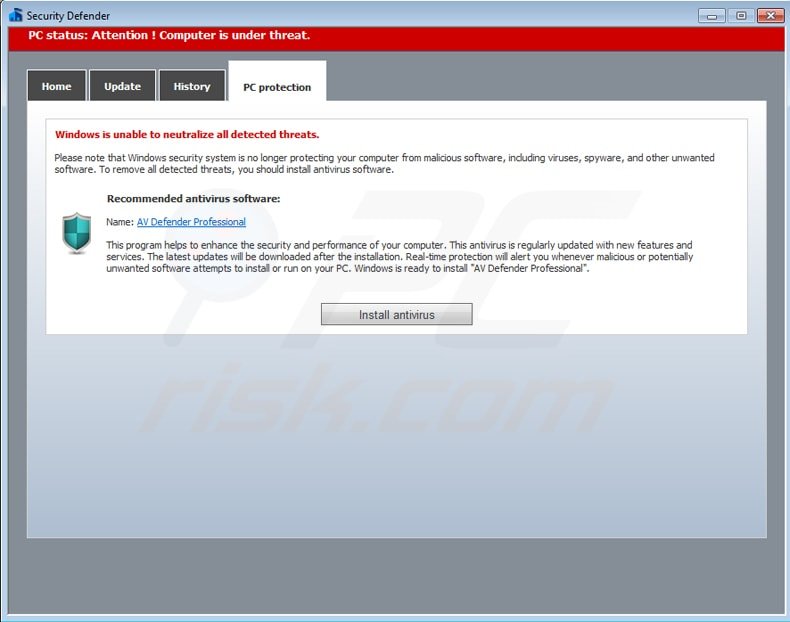
Security Defender encouraging computer users into purchasing an antivirus program ('Defender PRO 2015') to remove previously 'detected' malware (not actually present on users' computers):
Update 9 September 2015 - Security Defender fake security scanner started promoting a non-existent antivirus program called 'AV Defender Professional':
A screenshot of a website used to promote Defender PRO 2015 (a fake antivirus program promoted by Security Defender):
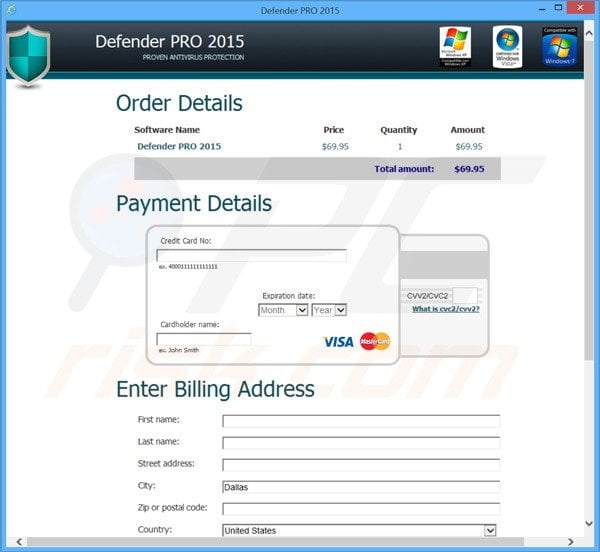
A payment page used for selling the Defender PRO 2015 non-existent antivirus program (at time of testing, the cost of this fake antivirus was $69.95 - PC users who have already paid for this scam should contact their credit card company and dispute the charges, explaining that they have been tricked into buying a fake antivirus program):
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is Security Defender?
- STEP 1. Remove Security Defender using Safe Mode with Networking.
- STEP 2. Optional Security Defender removal method.
- STEP 3. Manual Security Defender removal.
Security Defender removal using Safe Mode with Networking:
Windows 7 users:
Start your computer in Safe Mode. Click Start, click Shut Down, click Restart, click OK. During your computer start process press the F8 key on your keyboard multiple times until you see the Windows Advanced Option menu, then select Safe Mode with Networking from the list.
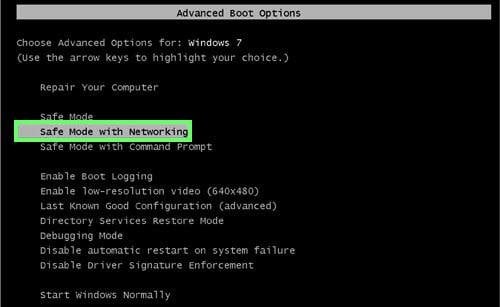
Video showing how to start Windows 7 in "Safe Mode with Networking":
Windows 8 users:
Windows 8 users: Go to the Windows 8 Start Screen, type Advanced, in the search results select Settings. Click on Advanced Startup options, in the opened "General PC Settings" window select Advanced Startup. Click on the "Restart now" button. Your computer will now restart into "Advanced Startup options menu".
Click on the "Troubleshoot" button, then click on "Advanced options" button. In the advanced option screen click on "Startup settings". Click on the "Restart" button. Your PC will restart into the Startup Settings screen. Press "5" to boot in Safe Mode with Networking.
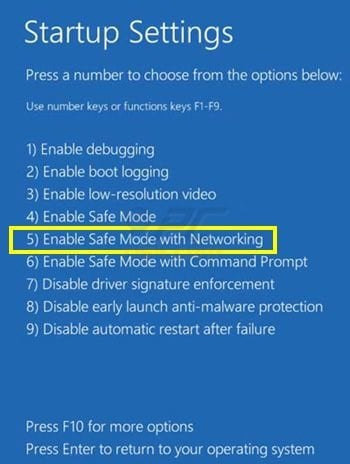
Video showing how to start Windows 8 in "Safe Mode with Networking":
After booting your computer in Safe Mode with Networking, try downloading and running the recommended antimalware software. If the download is blocked, follow the instructions presented below.
DOWNLOAD remover for malware infections
Combo Cleaner checks if your computer is infected with malware. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
NOTE: If you cannot run the remover, right-click on it and select "Run as administrator". If the installation of the malware remover fails, or you cannot open the .exe files, try one of the alternative download locations below:
- Location 1 (the file is renamed to "iexplore.exe", since most spyware does not block this file)
- Location 2
If, after or before, removal of this fake antivirus program you are unable to run any of your installed software, Security Defender has modified your operating system's .exe file associations. To fix this, download the registry fix (link below). Save it to your computer, double click it, click "Yes", and then "OK". After rebooting your PC, file associations should function normally.
Security Defender removal - optional method:
The Security Defender rogue blocks execution of all installed software - this makes its removal complicated. The best way to eliminate this rogue is to log in to an unaffected user account and run a security scan from it. If available, log in to 'Guest' account and follow the removal steps provided below. If your 'Guest' user account is not activated, follow these steps:
Windows 7 users:
Click on the Windows logo (Start), select Control Panel.
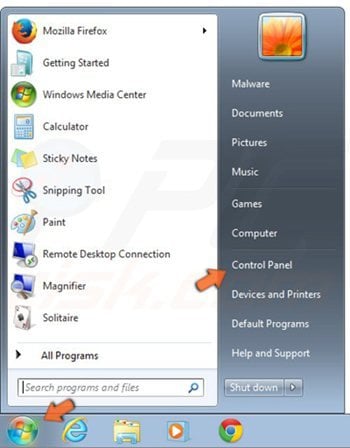
In the opened window, select "User Accounts and Family Safety".
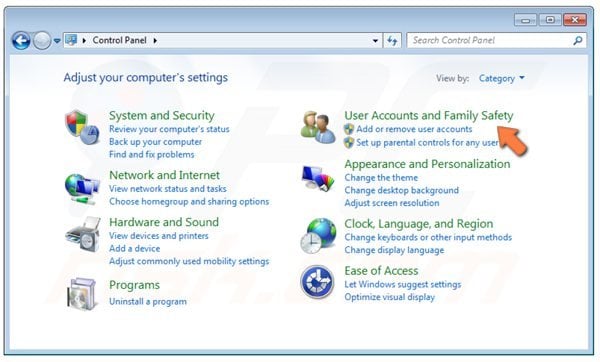
In the opened window, click the "Add or Remove User Accounts" link.
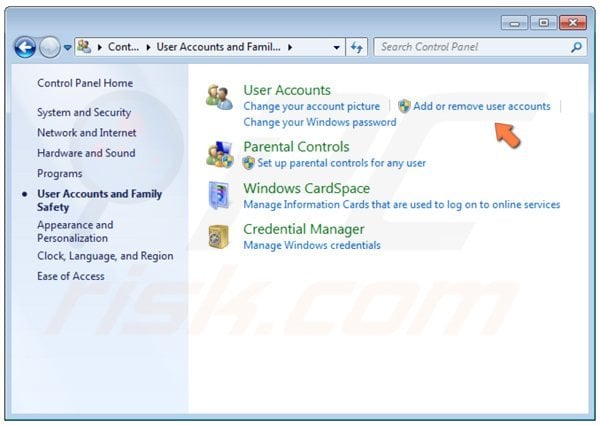
In the opened window, click "Guest Account".
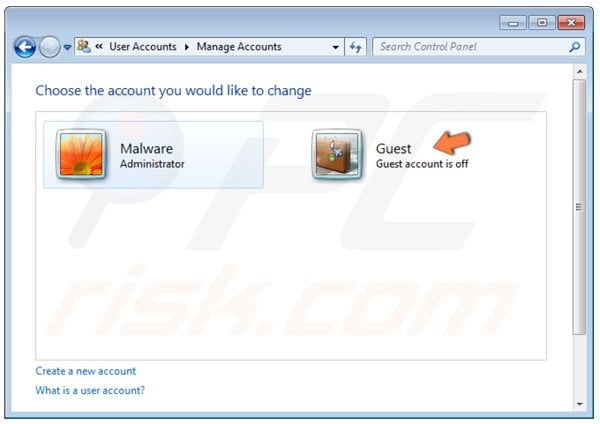
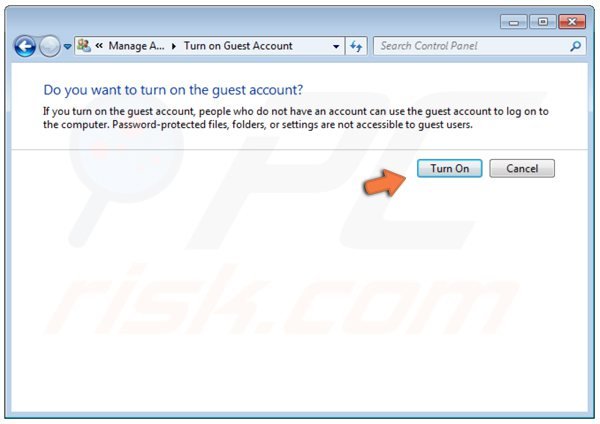
In the next window, click the "Turn On" button.
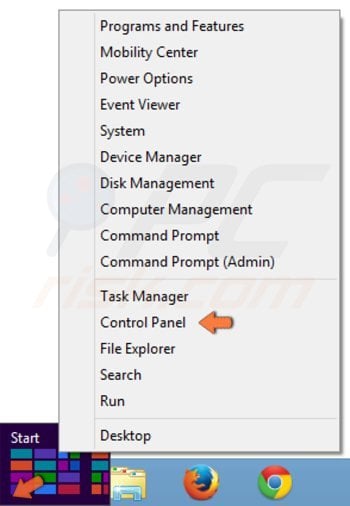
Windows 8 users:
Right-click in the lower left corner of the screen. In the Quick Access Menu, select Control Panel.
In the opened window, click "Change account type" (under "User Accounts and Family Safety").
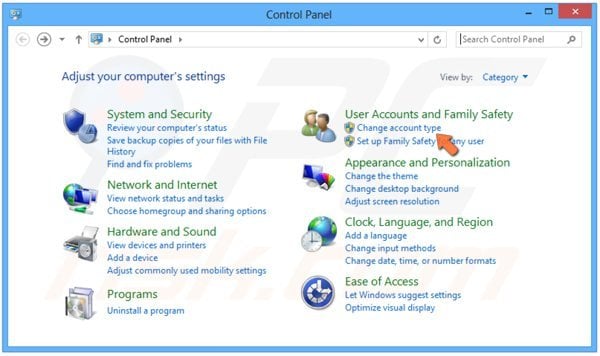
In the opened window, click "Guest".
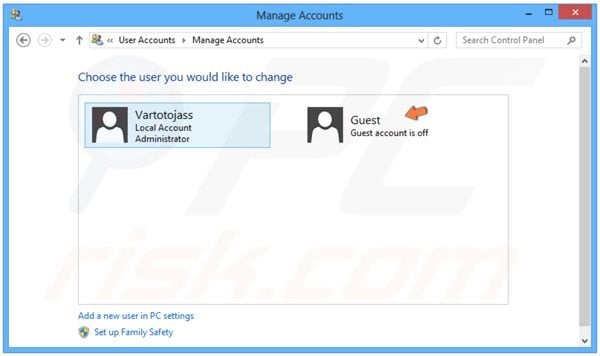
In the next window, click the "Turn On" button.
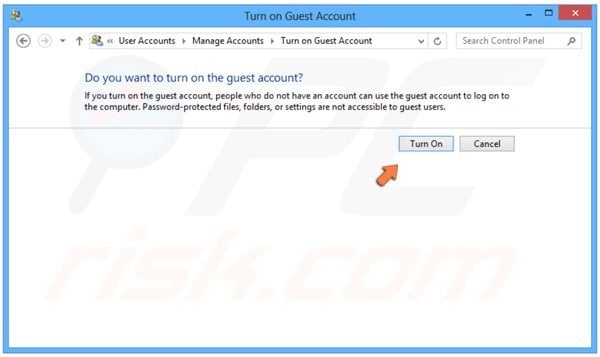
Restart your PC, when the Windows logon screen appears, select "Guest" user, then continue with the removal steps provided below.
After logging in your Guest account, download recommended malware removal software and run a full system scan to completely eliminate this fake antivirus software from your PC.
DOWNLOAD remover for malware infections
Combo Cleaner checks if your computer is infected with malware. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Manual Security Defender removal instructions
Some spyware can block the downloading of spyware removers. If you cannot download it using the default location, try one of the alternative download locations below:
- Location 1 (the file is renamed to "iexplore.exe", since most spyware does not block this file)
- Location 2
If installation of the remover fails, try downloading the customized installer, which was built by our technicians to bypass spyware infections. Download customized installer
If you still cannot download or run the spyware-removing software, perform these steps:
Step 1
Some variants of this spyware modify the system proxy settings so that you are unable to access the Internet (or website addresses are redirected to malicious or phishing websites). To reset the proxy settings to default, download and run this tool:
Step 2
Security Defender modifies the system Hosts file. The Hosts file is used to resolve canonical names of websites to IP addresses. When it is changed, the user may be redirected to malicious sites, despite seeing legitimate URLs in address bar. It is difficult to determine which sites are genuine when the Hosts file is modified.
To fix this, download the Microsoft Fix It tool, which restores your Hosts file to the Windows default. Run this tool when downloaded and follow the on-screen instructions. Download link below:
Step 3
That's It! You can now try to download the Malware remover or install and run it if already downloaded.
Summary:
The fake antivirus programs (also known as "rogue antivirus programs" or "scareware") are applications that tries to lure computer users into paying for their non-existent full versions to remove the supposedly detected security infections (although the computer is actually clean). These bogus programs are created by cyber criminals who design them to look as legitimate antivirus software. Most commonly rogue antivirus programs infiltrate user's computer using poop-up windows or alerts which appear when users surf the Internet. These deceptive messages trick users into downloading a rogue antivirus program on their computers. Other known tactics used to spread scareware include exploit kits, infected email messages, online ad networks, drive-by downloads, or even direct calls to user's offering free support.
A computer that is infected with a fake antivirus program might also have other malware installed on it as rogue antivirus programs often are bundled with Trojans and exploit kits. Noteworthy that additional malware that infiltrates user's operating system remains on victim's computer regardless of whether a payment for a non-existent full version of a fake antivirus program is made. Here are some examples of fake security warning messages that are used in fake antivirus distribution:
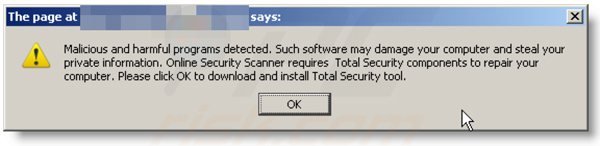
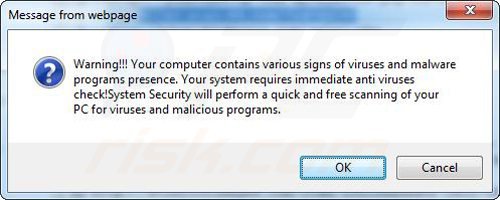
Computer users who are dealing with a rogue security software shouldn't buy it's full version. By paying for a license key of a fake antivirus program users would send their money and banking information to cyber criminals. Users who have already entered their credit card number (or other sensitive information) when asked by such bogus software should inform their credit card company that they have been tricked into buying a rogue security software. Screenshot of a web page used to lure computer users into paying for a non-existent full version of security defender scam and other rogue antivirus programs:
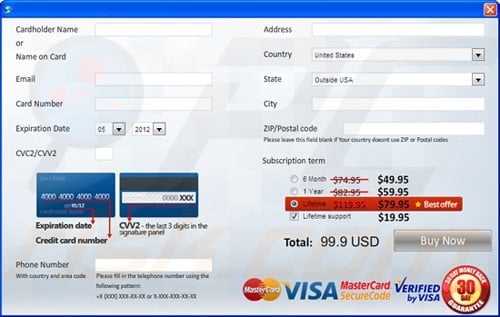
To protect your computer from security defender scam and other rogue antivirus programs users should:
- Keep their operating system and all of the installed programs up-to-date.
- Use legitimate antivirus and anti-spyware programs.
- Use caution when clicking on links in social networking websites and email messages.
- Don't trust online pop-up messages which state that your computer is infected and offers you to download security software.
Symptoms indicating that your operating system is infected with a fake antivirus program:
- Intrusive security warning pop-up messages.
- Alerts asking to upgrade to a paid version of a program to remove the supposedly detected malware.
- Slow computer performance.
- Disabled Windows updates.
- Blocked Task Manager.
- Blocked Internet browsers or inability to visit legitimate antivirus vendor websites.
If you have additional information on security defender scam or it's removal please share your knowledge in the comments section below.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion