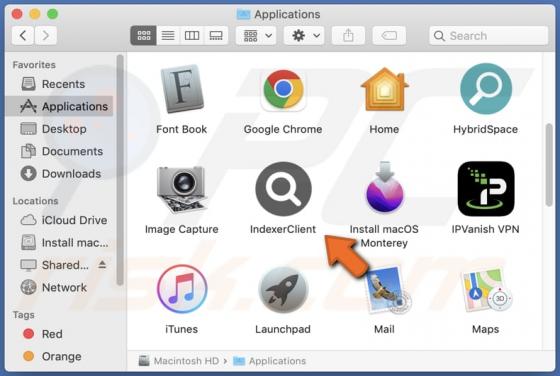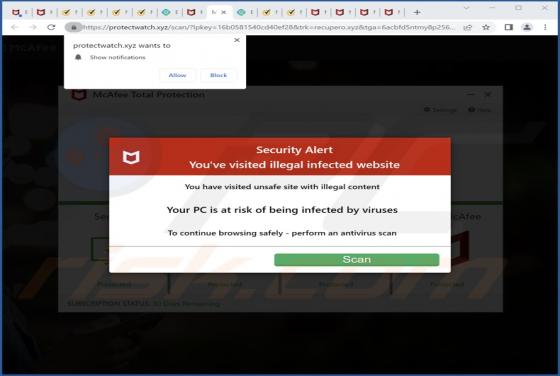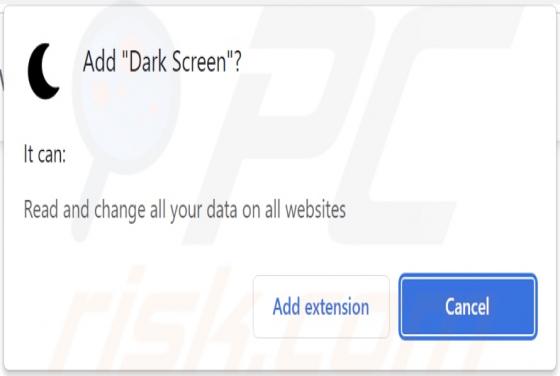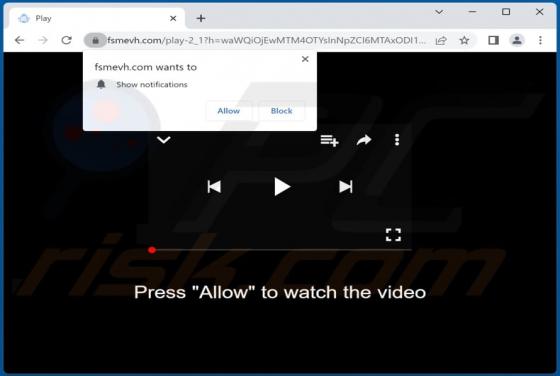
Windows Calculator Malware
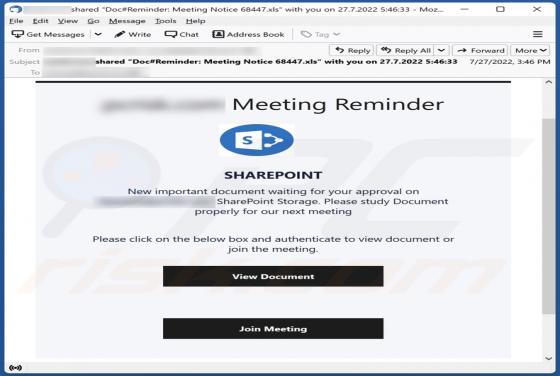
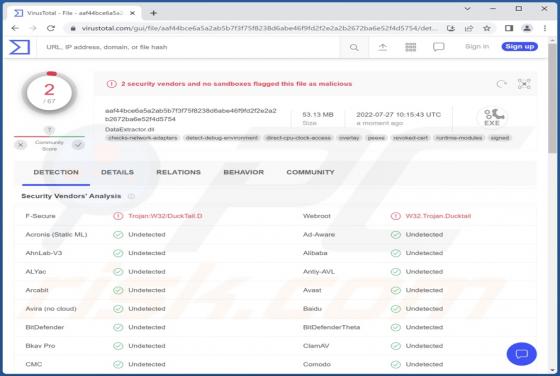
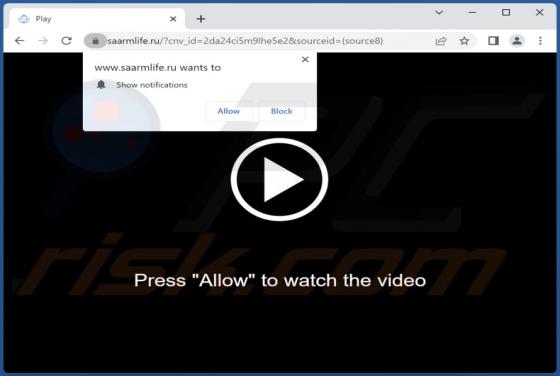
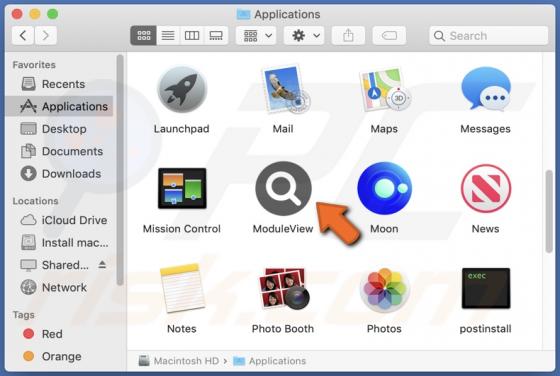
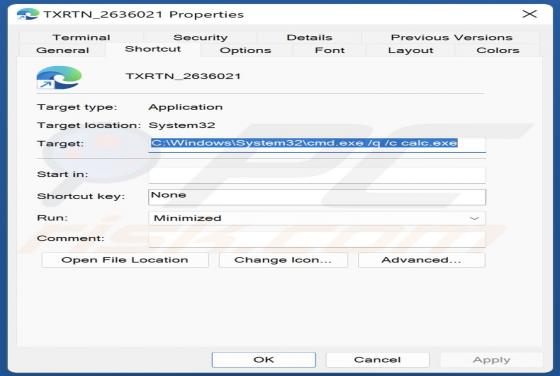
While analyzing an email containing a malicious attachment, we discovered that the threat actors behind Qakbot (also known as QBot) use a DLL hijacking method to distribute malware. They are abusing the Windows 7 Calculator application in their attacks. Currently, Qakbot is known to be used as a d