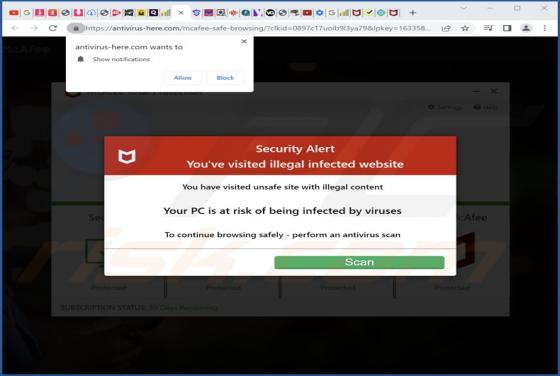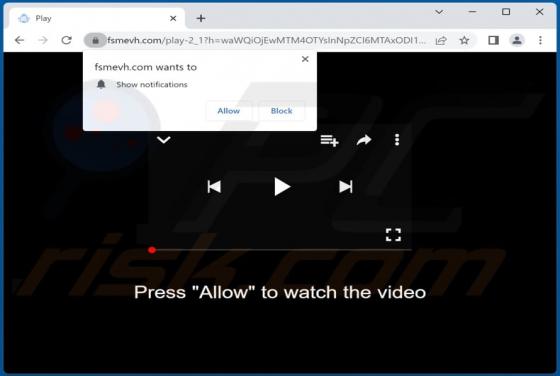
Fsmevh.com Ads
Fsmevh[.]com uses a clickbait technique to trick visitors into agreeing to receive notifications. Also, this page can redirect visitors to a similar website. We discovered fsmevh[.]com while examining other sites that use rogue advertising networks. It is uncommon for pages like fsmevh[.]com to be