ApolloRAT Malware
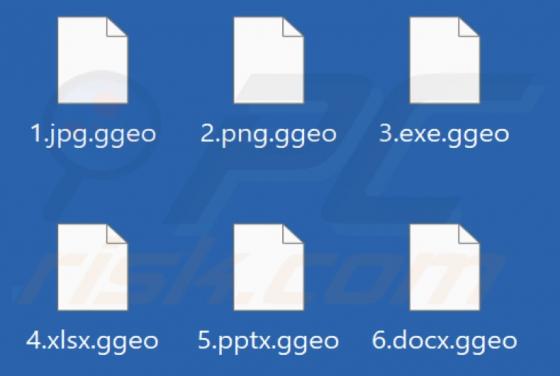
ApolloRAT is a piece of malicious software categorized as a RAT (Remote Access Trojan). Malware of this kind enables remote access and control over infected devices. ApolloRAT is written in Python. Programming languages like Python typically rely on compilers. The developers of this RAT used the