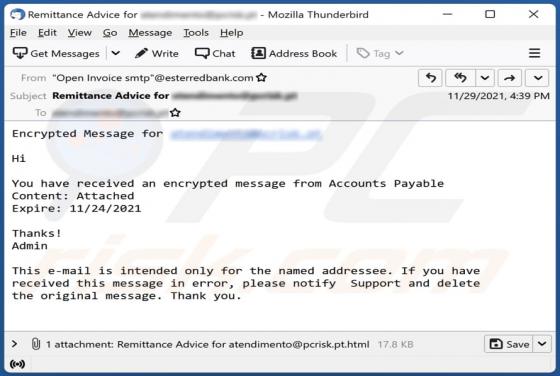
You Have Received An Encrypted Message Email Scam
It is a phishing email claiming that recipients have received an encrypted message and can open it via the attached file. The purpose of this email is to trick recipients into opening an HTML file designed to open a fake Microsoft page and entering their account login credentials on it. Th