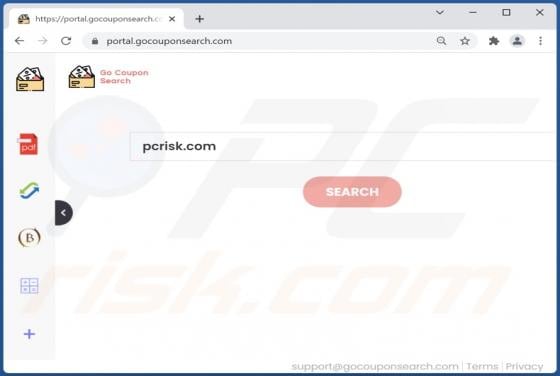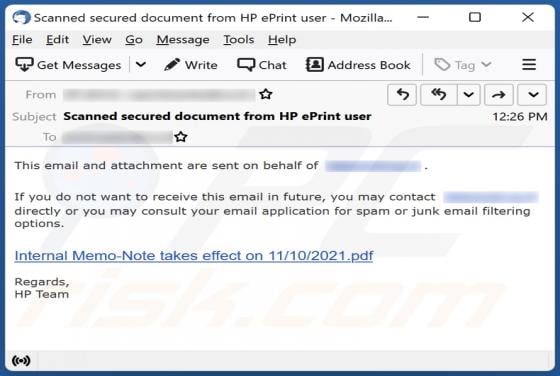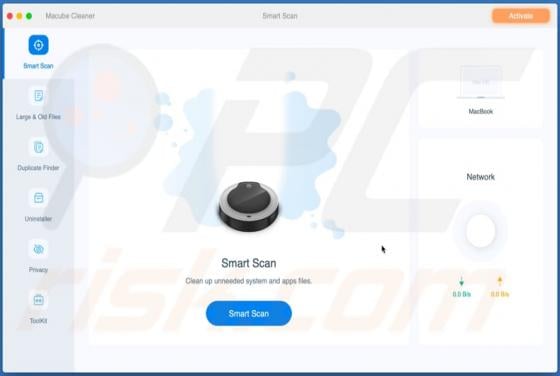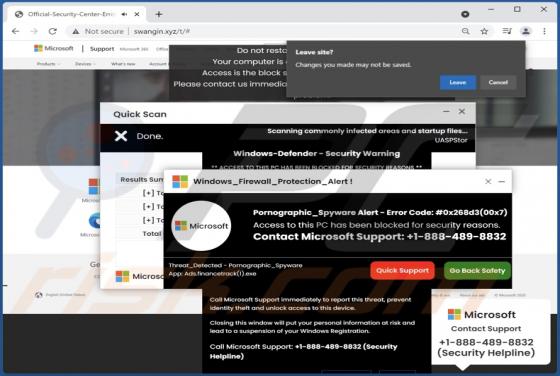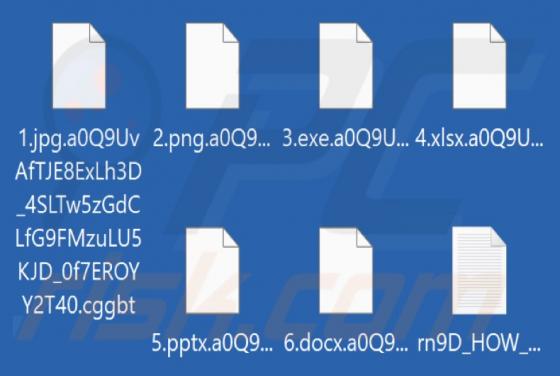
Cggbt Ransomware
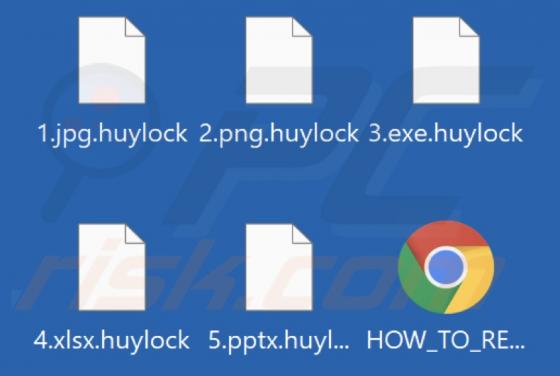
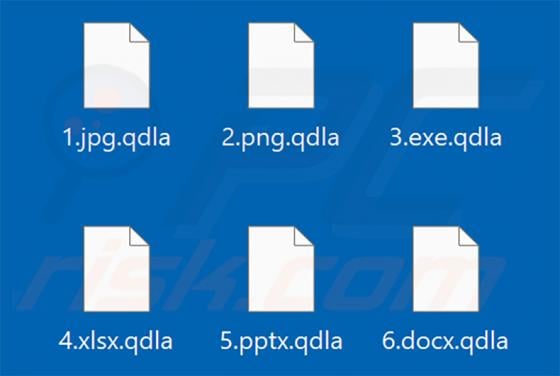
Cggbt is a ransomware-type programs. It operates by encrypting data (rendering files inaccessible) and demanding payment for the decryption. Files are appended with a random character string and a ".cggbt" extension. For example, a file like "1.jpg" would appear similar to "1.jpg.a0Q9UvAfTJE8ExLh