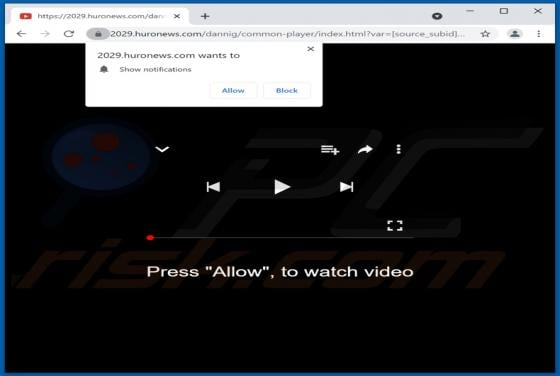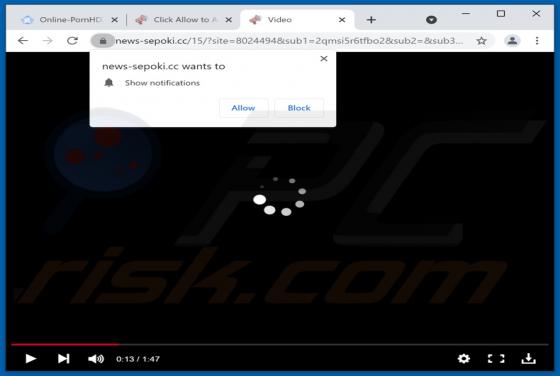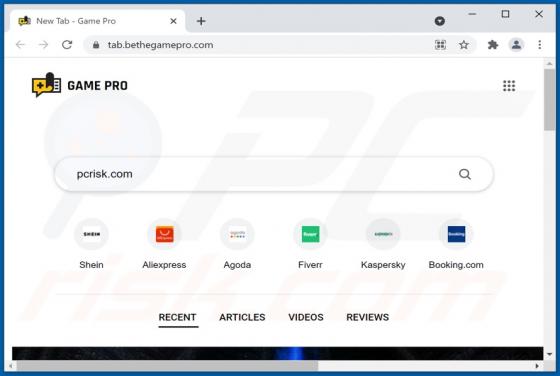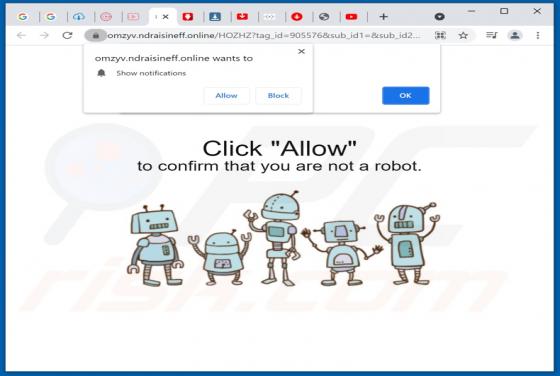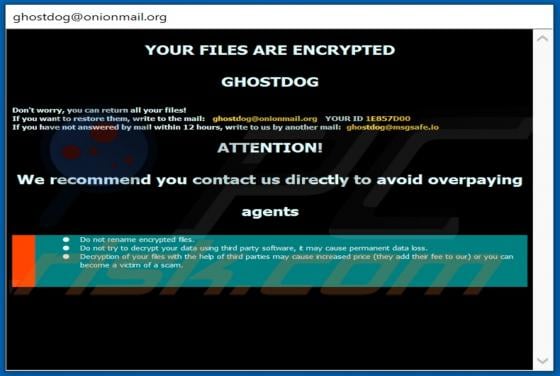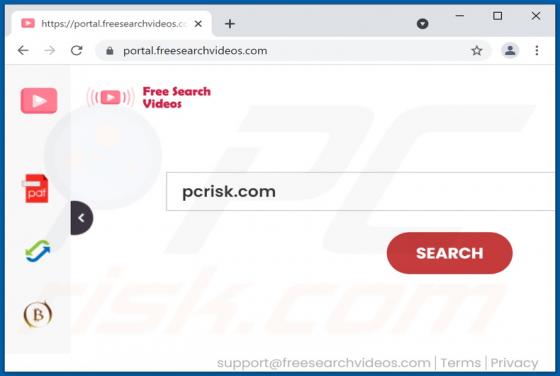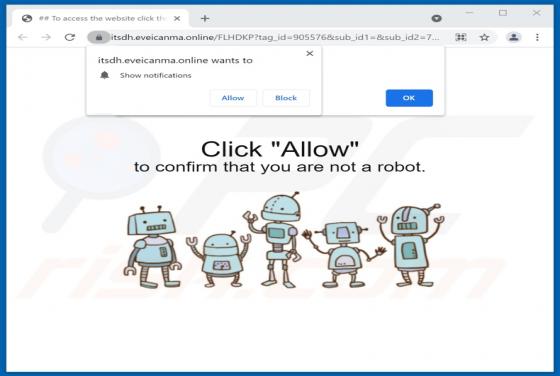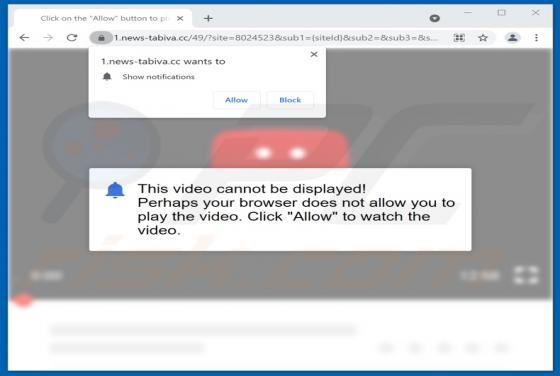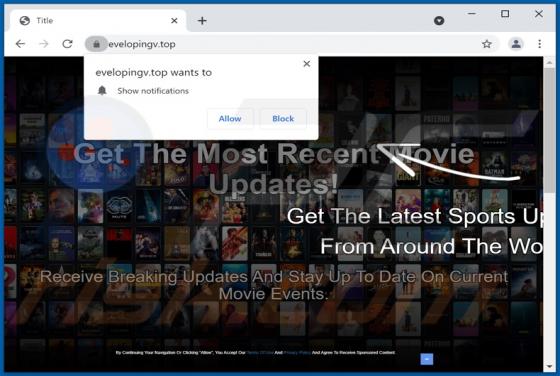
Evelopingv.top Ads
Evelopingv[.]top is a rogue website sharing many similarities with huronews.com, news-sepoki.cc, tik-ttok.net, eveicanma.online, and thousands of others. It is designed to present visitors with questionable content and/or redirect them to various (likely unreliable or malicious) webpages. This ki