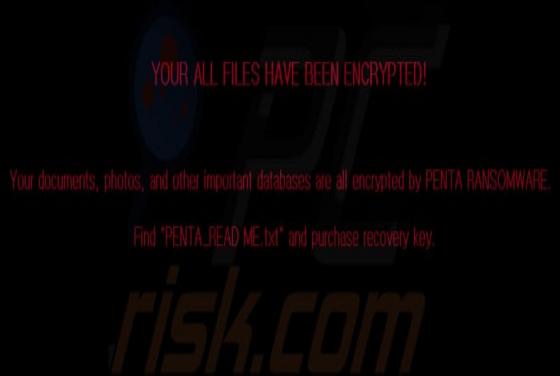
PENTA Ransomware
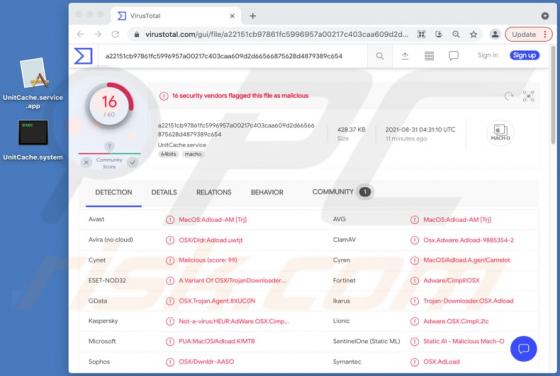
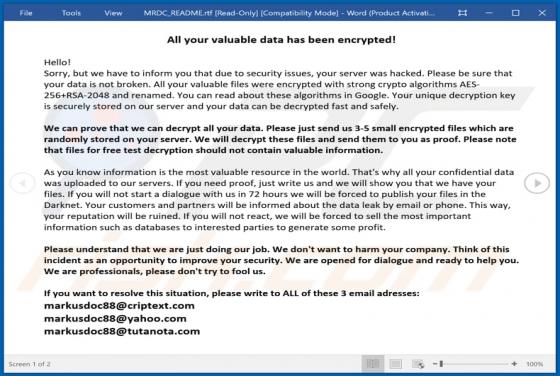
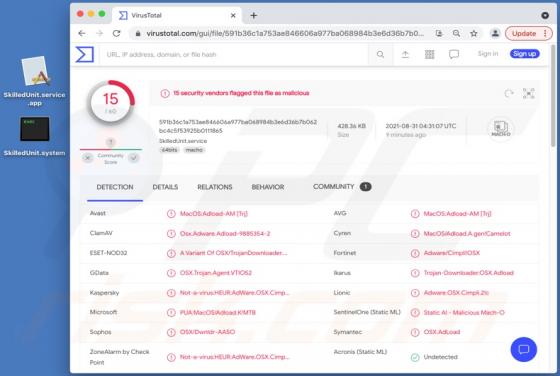
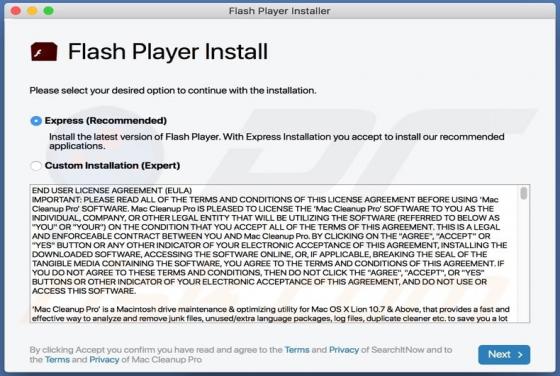
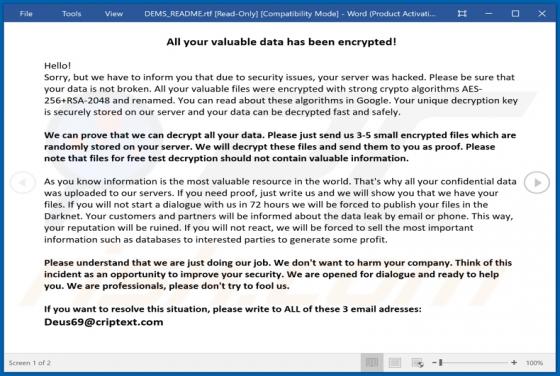
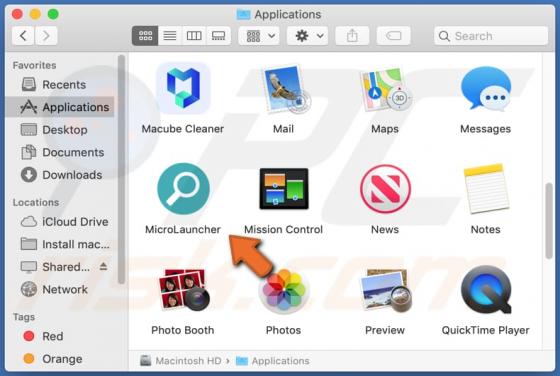
PENTA is a type of malicious software that encrypts files so that victims could not access them without a decryption tool purchased from the attackers. Also, it appends the ".PENTA" extension to their filenames (for example, it renames "1.jpg" to "1.jpg.PENTA", "2.jpg" to "2.jpg.PENTA"). Also, PE