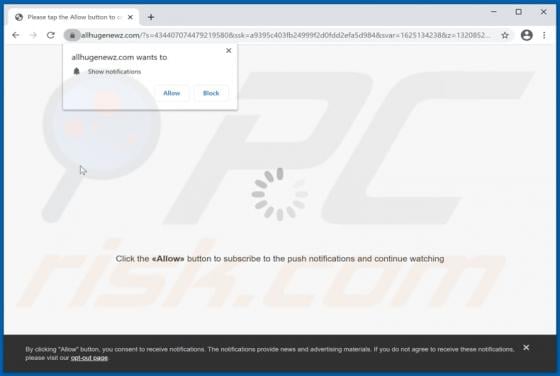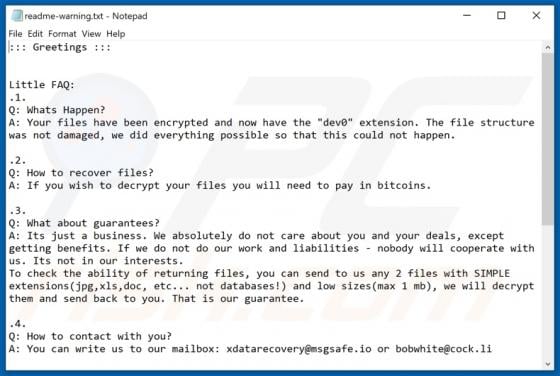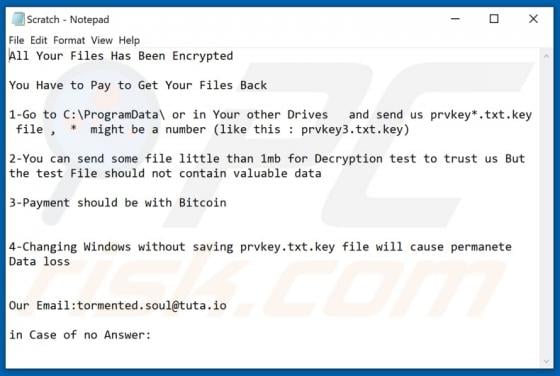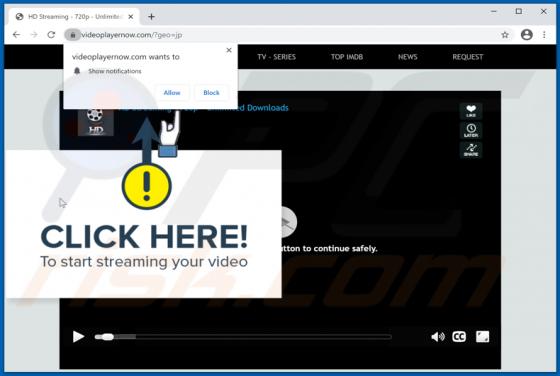
ATLAS AL SHARQ TRADING Email Virus
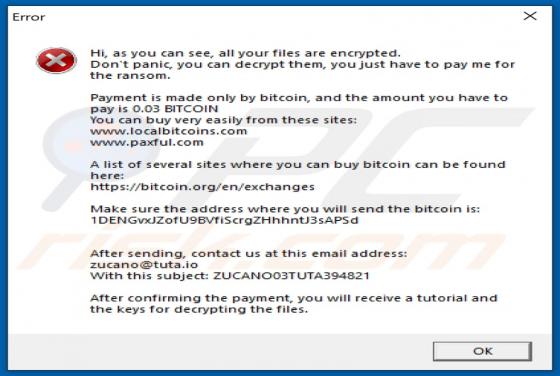
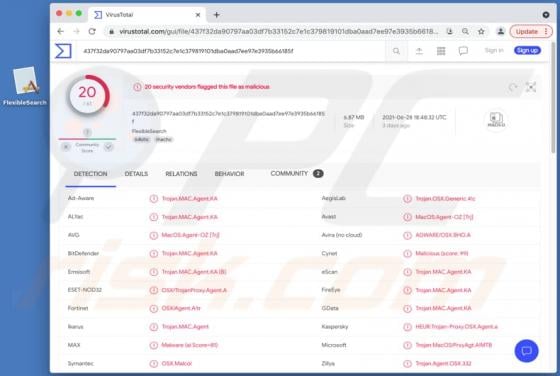
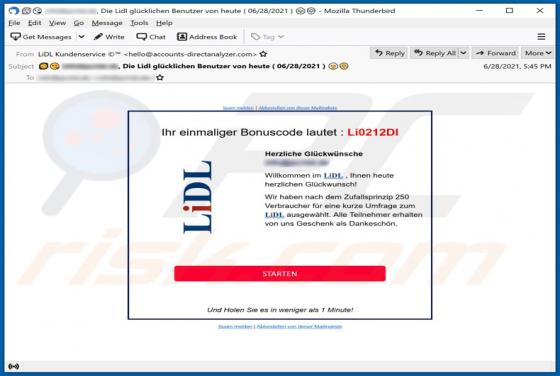
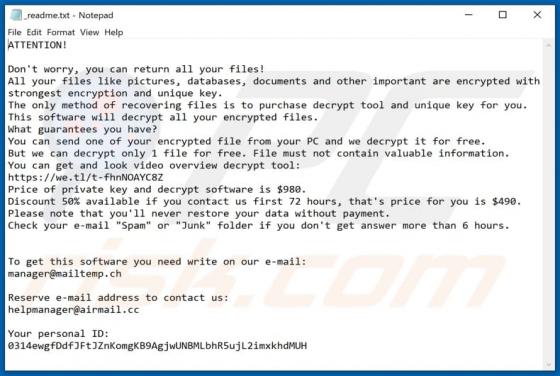
"ATLAS AL SHARQ TRADING email virus" refers to a malware-spreading spam campaign. The term "spam campaign" defines a mass-scale operation during which thousands of deceptive/scam emails are sent. The letters distributed through this campaign are disguised as mail from Atlas Al Sharq Trading Estab