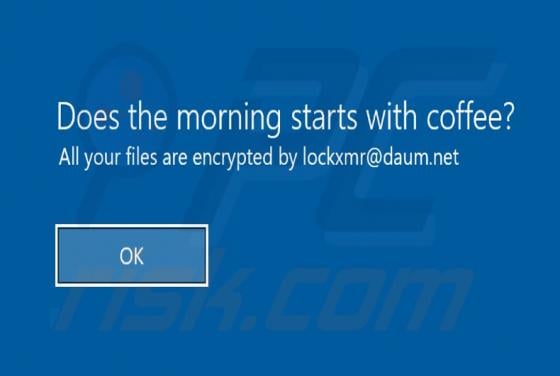
XMRLocker Ransomware
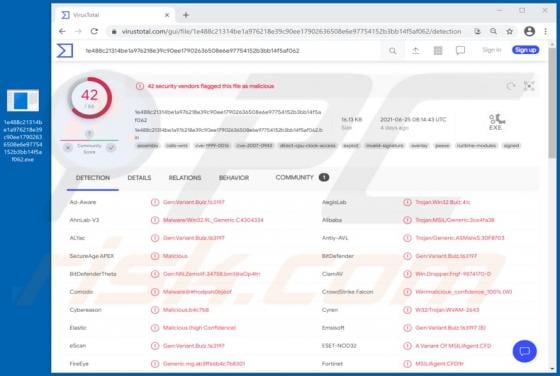
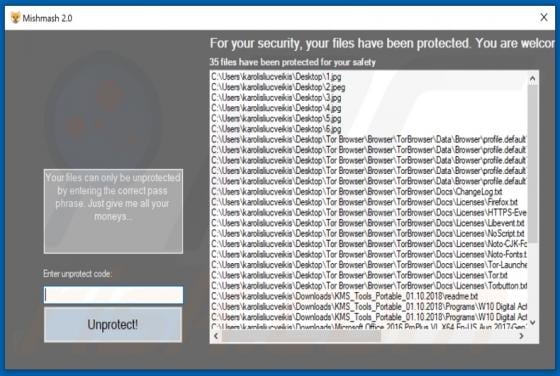
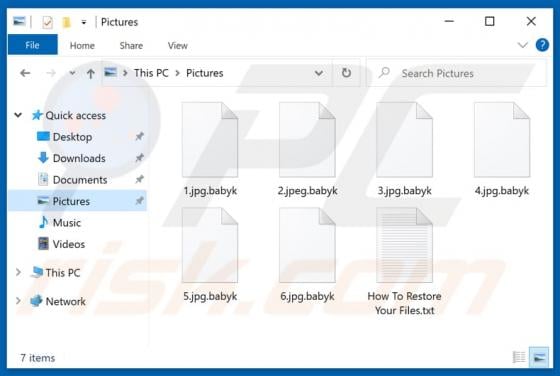
Ransomware is a type of malware that cybercriminals monetize by getting paid for decryption tools. XMRLocker ransomware encrypts files, renames them by appending the ".[XMRLocker]" extension (for example, it renames a file named "1.jpg" to "1.jpg.[XMRLocker]", "2.jpg" to "2.jpg.[XMRLocker]") and c