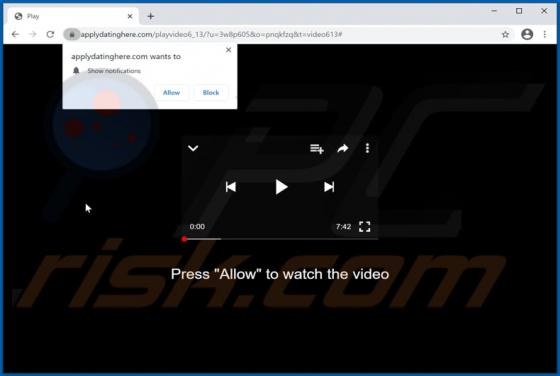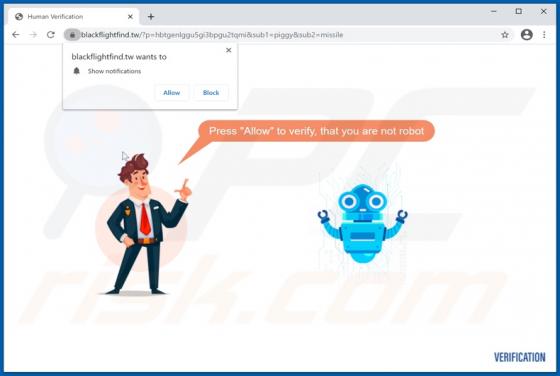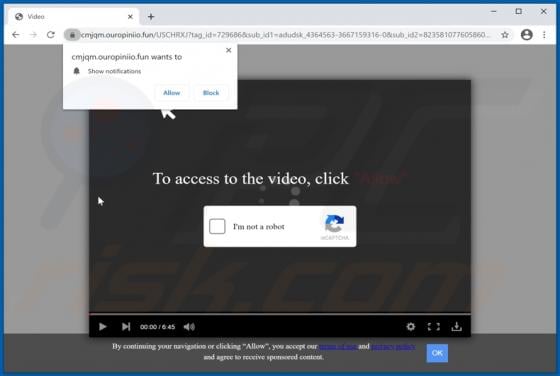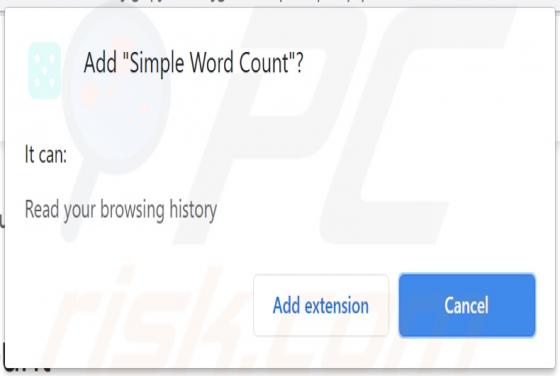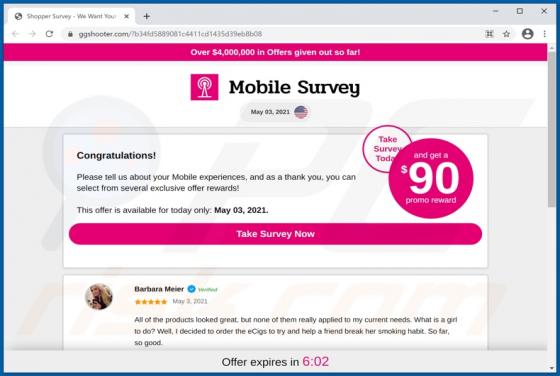
Mobile Survey Reward Scam
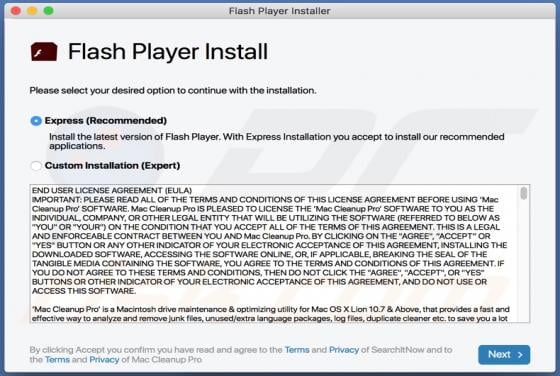
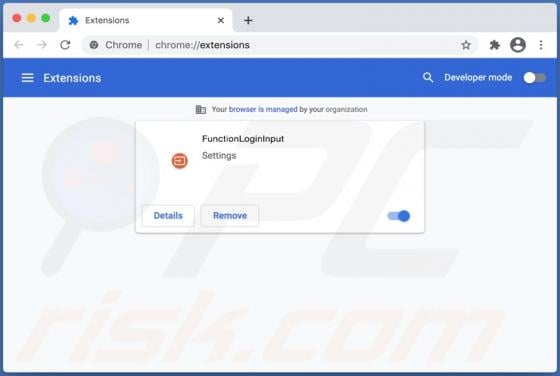
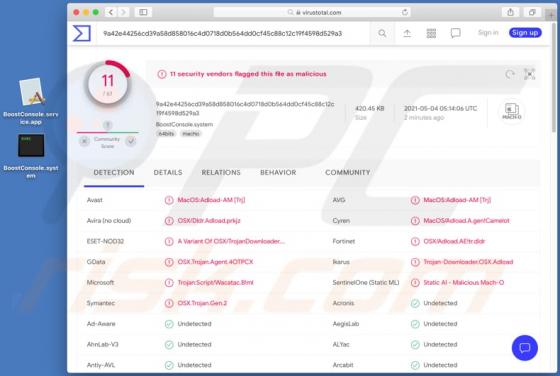
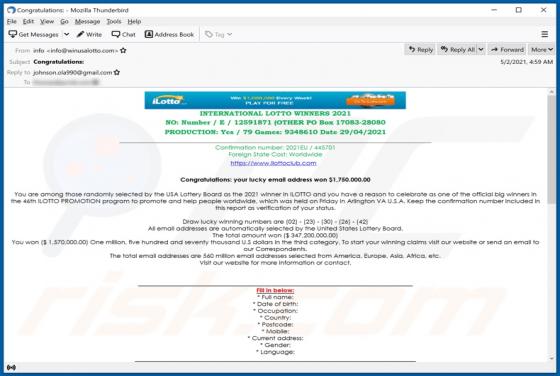
"Mobile Survey Reward" is the name of a scam run on various untrustworthy webpages. This scheme states that for completing a short questionnaire - users will receive a prize. It must be emphasized that all of the claims made by the scam are false, and users will not receive any rewards. The "Mobi