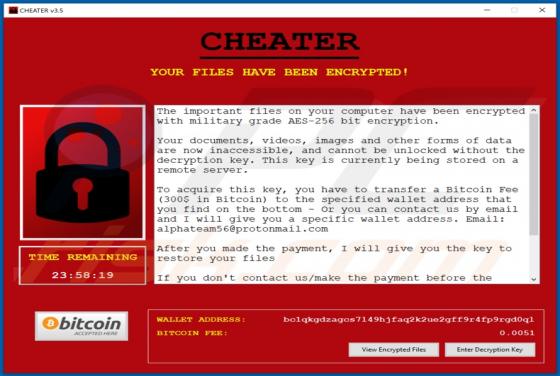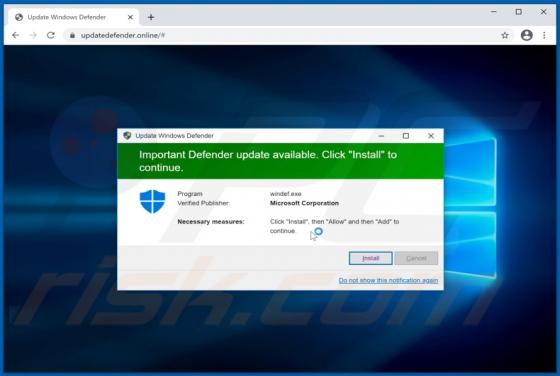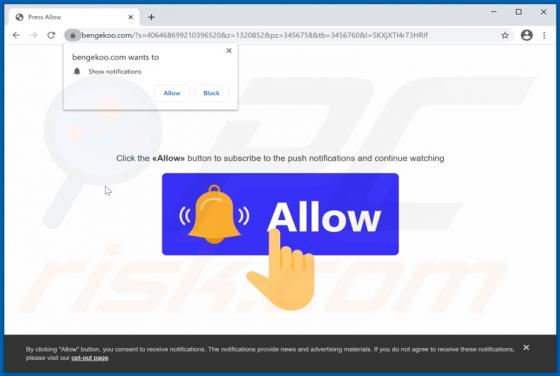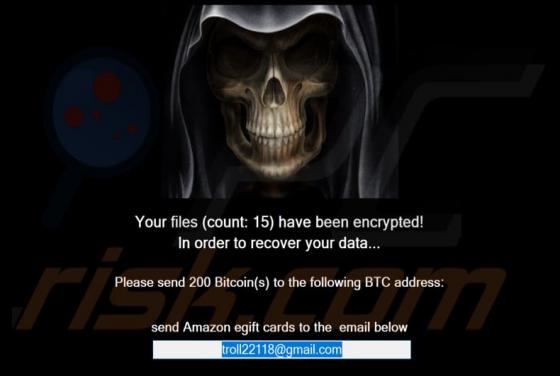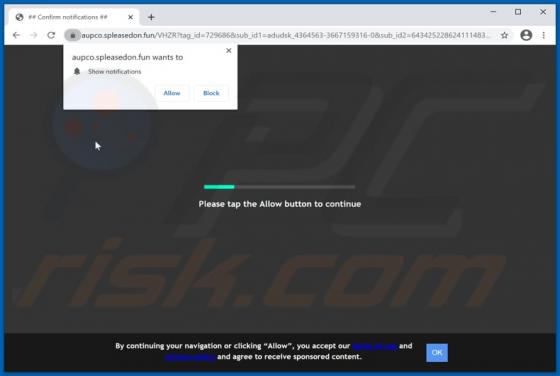
QuicklookPI Adware (Mac)
QuicklookPI is a rogue application classified as adware. This app has been observed being distributed alongside other adware and browser hijackers, notably, SearchUp. Adware operates by running intrusive advertisement campaigns, i.e., delivering various ads. Browser hijackers promote (by causin