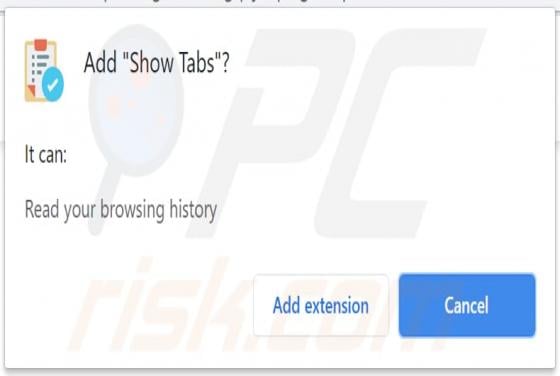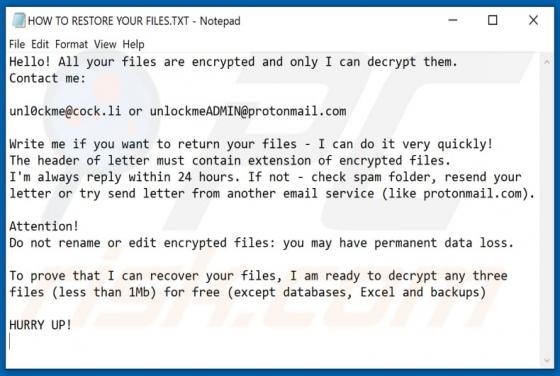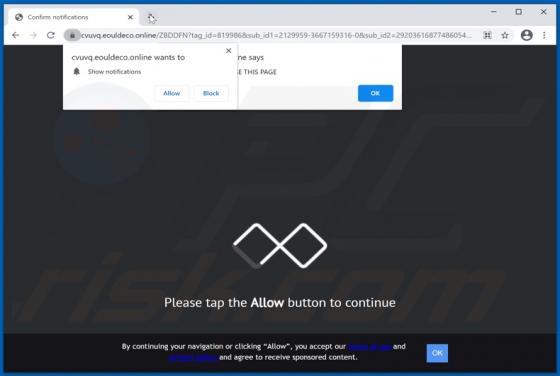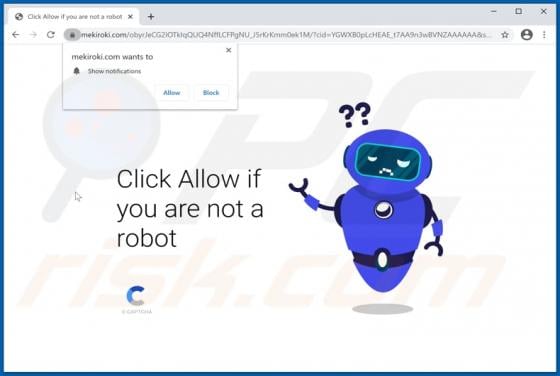
Kamira99 Ransomware
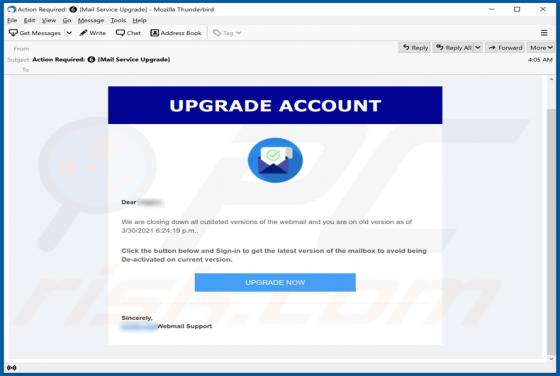
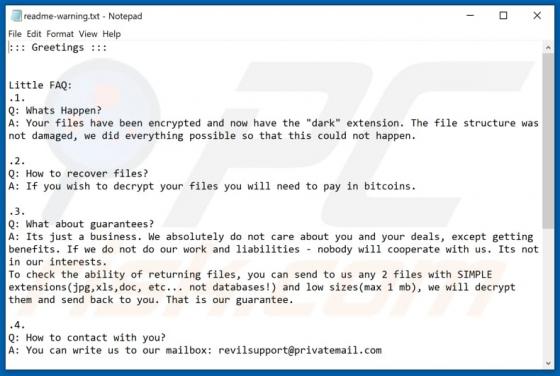
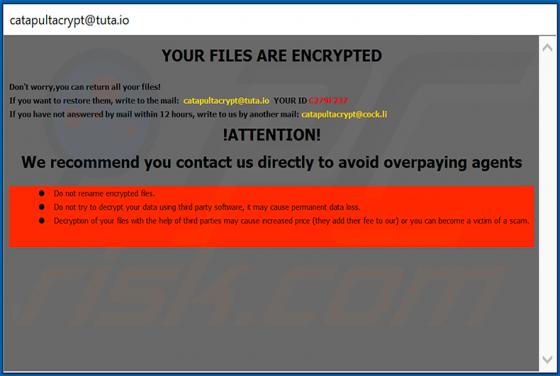
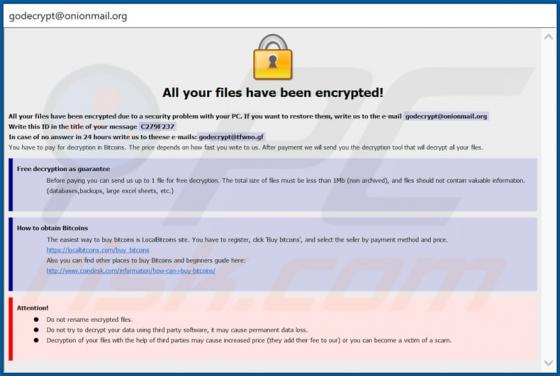
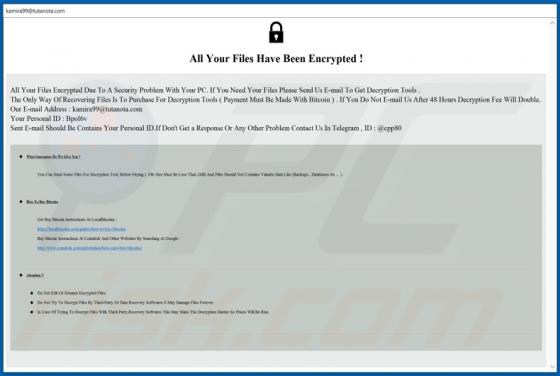
Virtually identical to FilesRecoverEN, Kamira99 is a ransomware-type program. This malware encrypts and renames files and creates ransom messages, which demand payment for decryption. I.e., files affected by Kamira99 become inaccessible/unusable and victims are asked to pay to restore their data.