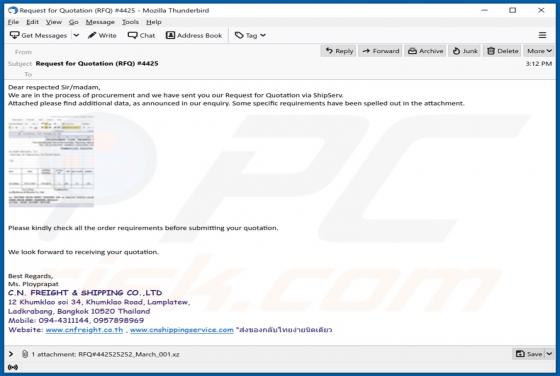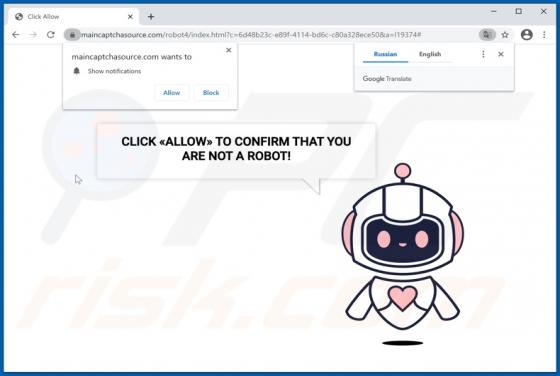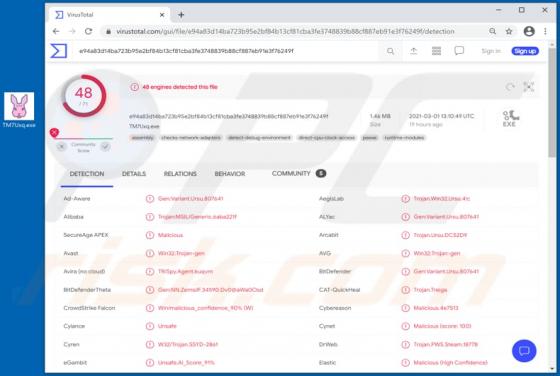
Ades Stealer
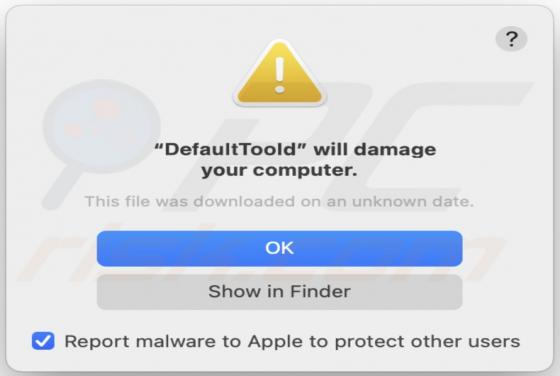
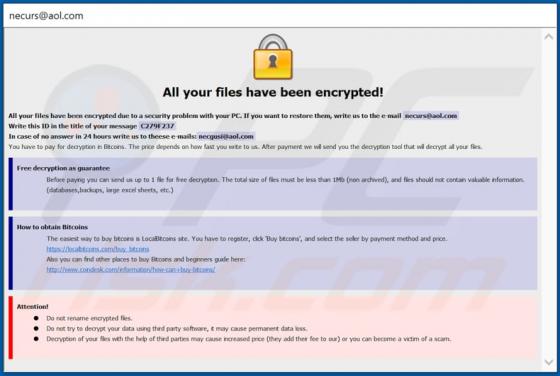
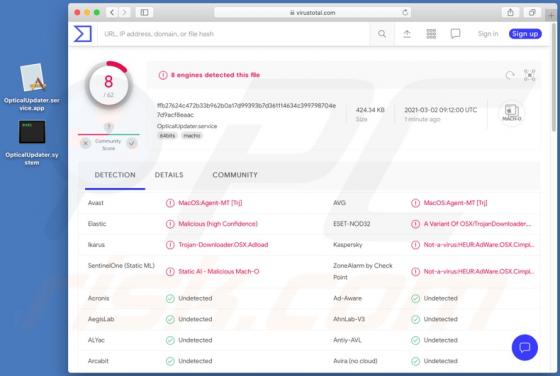
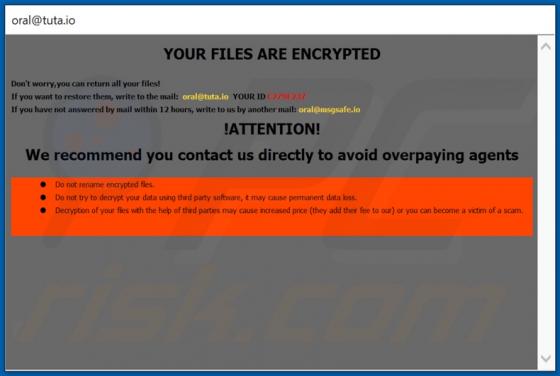
Information stealers are malware programs that can be designed to record keystrokes, take screenshots, and gather other data in order to send it to the attackers. Malware of this type can run stealthily in the background so that victims do not suspect infection. Ades is a stealer written in the C