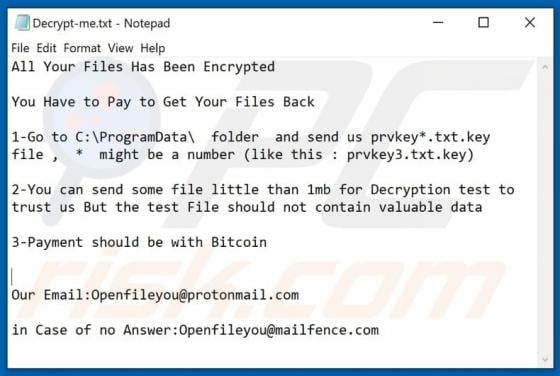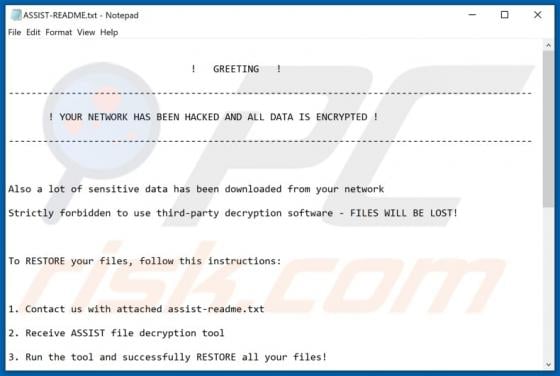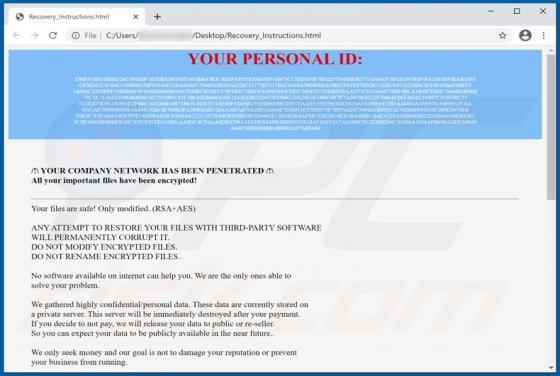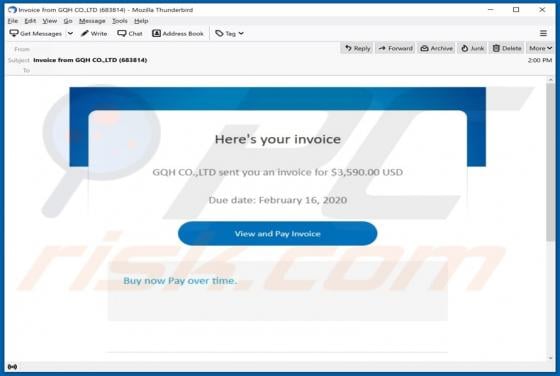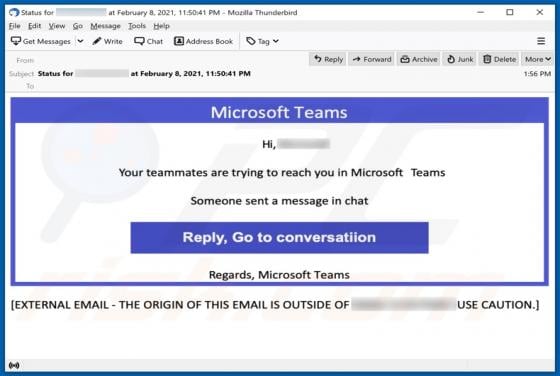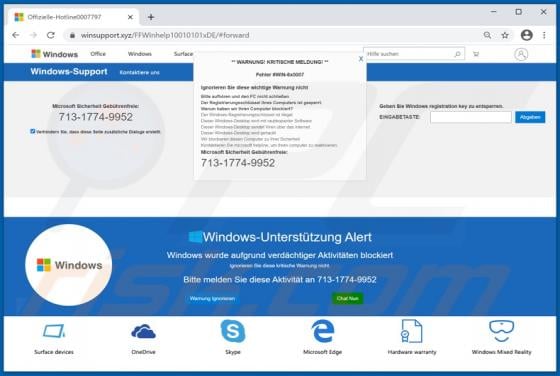
WIN-8x0007 Error POP-UP Scam
"WIN-8x0007 Error" is the name of a technical support scam run on deceptive websites. Schemes of this type inform users of nonexistent threats on their systems and urge them to contact fake tech support. The "WIN-8x0007 Error" scam targets German users. It also downloads an audio file that contain