Do not trust the "Your iPhone is now online and located" scam SMS
Mac VirusAlso Known As: "Your iPhone is now online and located" smishing scam
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What are the fake "Your iPhone is now online and located" text messages?
"Your iPhone is now online and located" is a smishing scam. The term "smishing" is closely related to "phishing". This type of scheme is promoted via text (SMS) messages and typically attempts to extract personal information from potential victims - often, under the guise of legitimate company representatives.
In the case of the "Your iPhone is now online and located" scam, the deceptive SMS messages are disguised as security alerts from "Apple Support". The messages sent by this scam state that recipients' mobile devices have been located and are currently online.
This scheme is in no way associated with Apple Inc., and all of the information provided by it is false. The goal of "Your iPhone is now online and located" is to abuse users' trust for profit.
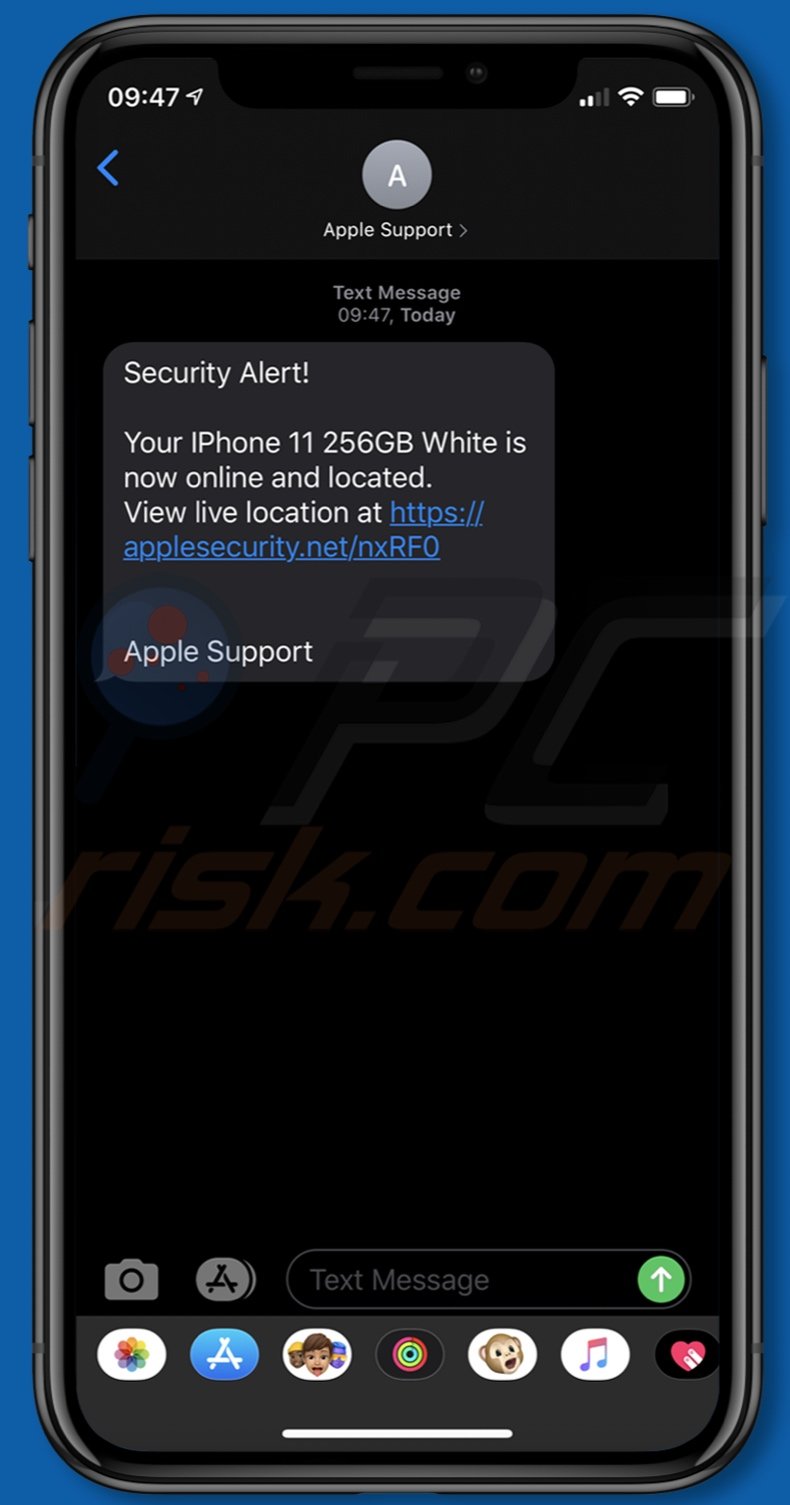
Through the "Your iPhone is now online and located" scam, two practically identical text message variants are distributed. They are disguised as security updates or notifications from "Apple Support". They claim that recipients' mobile devices have been located - the device is specified as "IPhone 11 256GB White" or "iPhone 11 Pro 256GB Gray".
Additionally, it is stated that the (nonexistent) telephones are currently online or were so for a brief period of time. Both variants of the SMS texts contain URLs of deceptive and possibly malicious websites.
This type of scam is usually employed to gather personal/sensitive information from victims such as names, surnames, addresses, emails, banking account and/or credit card details, etc. Scammers may also demand remote access to users' devices and/or offer nonoperational, untrusted or malicious software products.
Furthermore, the "services" of scammers (e.g. fake technical support) are expensive and users may be asked to pay exorbitant amounts. To summarize, trusting the "Your iPhone is now online and located" scam can lead to system infections, financial loss, serious privacy issues and even identity theft.
Text message scams or, more precisely, telephone scams in general, have much in common with online scams (in some cases, they may even be directly connected).
Scammers use various tactics to contact potential victims such as SMS messages, telephone calls, emails, deceptive websites and software, etc.
Popular scam models include (but are not limited to) warnings that the system is infected or at risk (promoted via web pages and messages displayed by fake anti-virus tools), alerts that a piece of essential software is outdated or missing (primarily, via websites), offers of refunds and other "unbelievable" deals (mainly, via telephone calls), prize giveaways and raffles (websites, emails, SMS messages, telephone calls), and so on.
Many types of scams boil down to the scammers requesting remote access to users' devices - this is not exclusive to tech support scams.
After gaining access to them, scammers can infect the system with malware (e.g. RATs to ensure indefinite stealthy access to the machine, Trojans, ransomware and other malicious programs), install non-free products (typically nonfunctional, even after purchase/activation), steal stored content, account log-in credentials (i.e. IDs, usernames and passwords) and other sensitive information (e.g. credit card details), delete system/personal data, lock the device (e.g. through malware or by setting a new password), and so on.
As mentioned, scammers usually ask to be paid for their "services". Deceptive websites are rarely accessed intentionally. Most users enter them through misspelled URLs, are redirected to the sites by intrusive advertisements or PUAs (Potentially Unwanted Applications) already installed on their systems.
These apps can have varied dubious functionality, and in different combinations as well. Some PUAs force-open dubious, deceptive and malicious pages. Adware-types delivers pop-ups, banners, coupons and other intrusive advertisements. Browser hijackers modify browser settings to promote fake search engines.
Most PUAs (regardless of type) have data-tracking capabilities, which are used to monitor browsing activity. Information of interest includes visited URLs, viewed webpages, searched queries, IP addresses, geolocations and even personally identifiable information.
The collected data is then shared with and/or sold to third parties (potentially, to scammers and/or cyber criminals). To ensure device integrity and user safety, all suspicious applications and browser extensions/plug-ins must be removed without delay.
| Name | "Your iPhone is now online and located" smishing scam |
| Threat Type | Phishing, Scam, Mac malware, Mac virus. |
| Fake Claim | Scam SMSes claims recipients' iPhones have been located. |
| Symptoms | Your Mac becomes slower than normal, you see unwanted pop-up ads, you are redirected to dubious websites. |
| Distribution methods | Deceptive pop-up ads, free software installers (bundling), fake Flash Player installers, torrent file downloads. |
| Damage | Internet browser tracking (potential privacy issues), display of unwanted ads, redirects to dubious websites, loss of private information. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
"Cash-App-Transfer is pending your confirmation" is an example of a scam promoted via text messages, and similar to "Your iPhone is now online and located".
The Web is full of these scams. Some examples of popular models include: tech support - "IOS /MAC Defender Alert", "Warning: Your macOS has expired", "ZEUS VIRUS DETECTED !!!", etc.; software update - "Latest version of Adobe Flash Player", "Update to the latest version of HD Video Player", "Flash Player Update Download New Version", etc.; prize giveaway/raffle "Winners of the new iPhone 11 Pro", "Apple Rewards Program", "Congratulations! Netflix User!", etc.
Regardless of what these scams claim, promise, offer, request or demand, their purpose is identical: to generate revenue for the scammers/cyber criminals behind them. Therefore, exercise caution with dubious SMS messages, calls, emails, applications and websites.
How did potentially unwanted applications install on my computer?
Some PUAs have "official" download web pages, which are often promoted by deceptive/scam websites. These applications can also be downloaded/installed together with other products. This deceptive marketing method of packing regular software with unwanted or malicious additions is called "bundling".
Rushing download/installation processes (e.g. ignoring terms, skipping steps, etc.) increases the risk of unintentionally allowing bundled content into the system. Once clicked, intrusive ads can execute scripts to download/install PUAs without users' permission.
How to avoid installation of potentially unwanted applications
You are advised to research all products before download/installation and/or purchase. All downloads must be done from official and verified sources. Untrusted channels such as unofficial and free file-hosting sites, Peer-to-Peer sharing networks and other third party downloaders commonly offer bundled content.
When downloading/installing, it is important to read the terms, explore all available options, use the "Custom/Advanced" settings and opt-out of additional apps, tools, features, etc. Intrusive advertisements usually seem normal and harmless, however, they can redirect to dubious and harmful web pages (e.g. gambling, pornography, adult-dating, and so on).
If you encounter ads and/or redirects of this kind, inspect the system and remove all suspect applications and browser extensions/plug-ins immediately. If your computer is already infected with PUAs, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate them.
Text presented in the "Your iPhone is now online and located" scam:
Security Alert!
Your IPhone 11 256GB White is now online and located.
View live location at -
Apple Support
Appearance of another text message variant of the "Your iPhone is now online and located" scam:
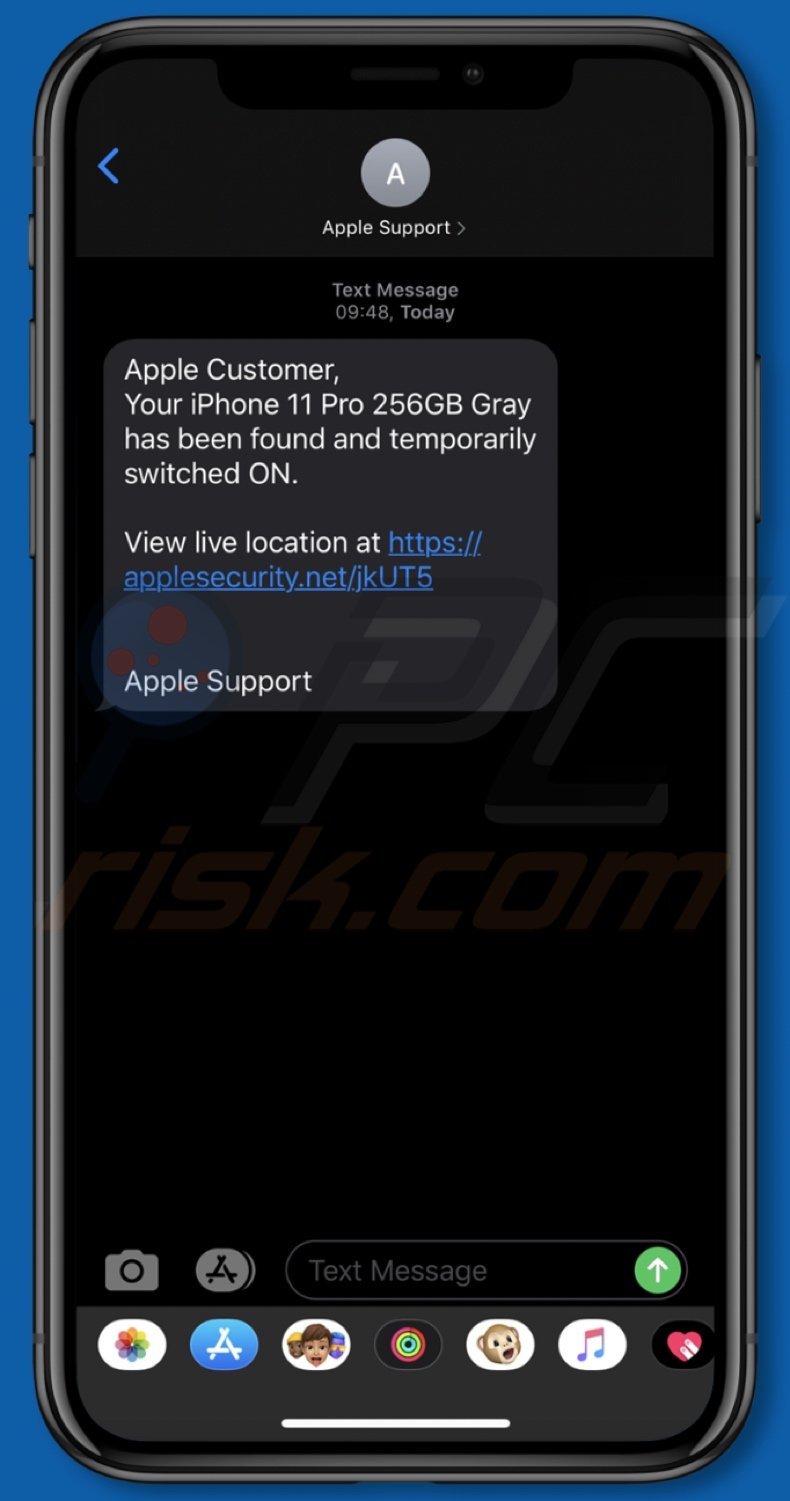
Text presented in this variant:
Apple Customer,
Your iPhone 11 Pro 256GB Gray has been found and temporarily switched ON.View live location at -
Apple Support
Another similar smishing scam variant used targeting iPhone users:
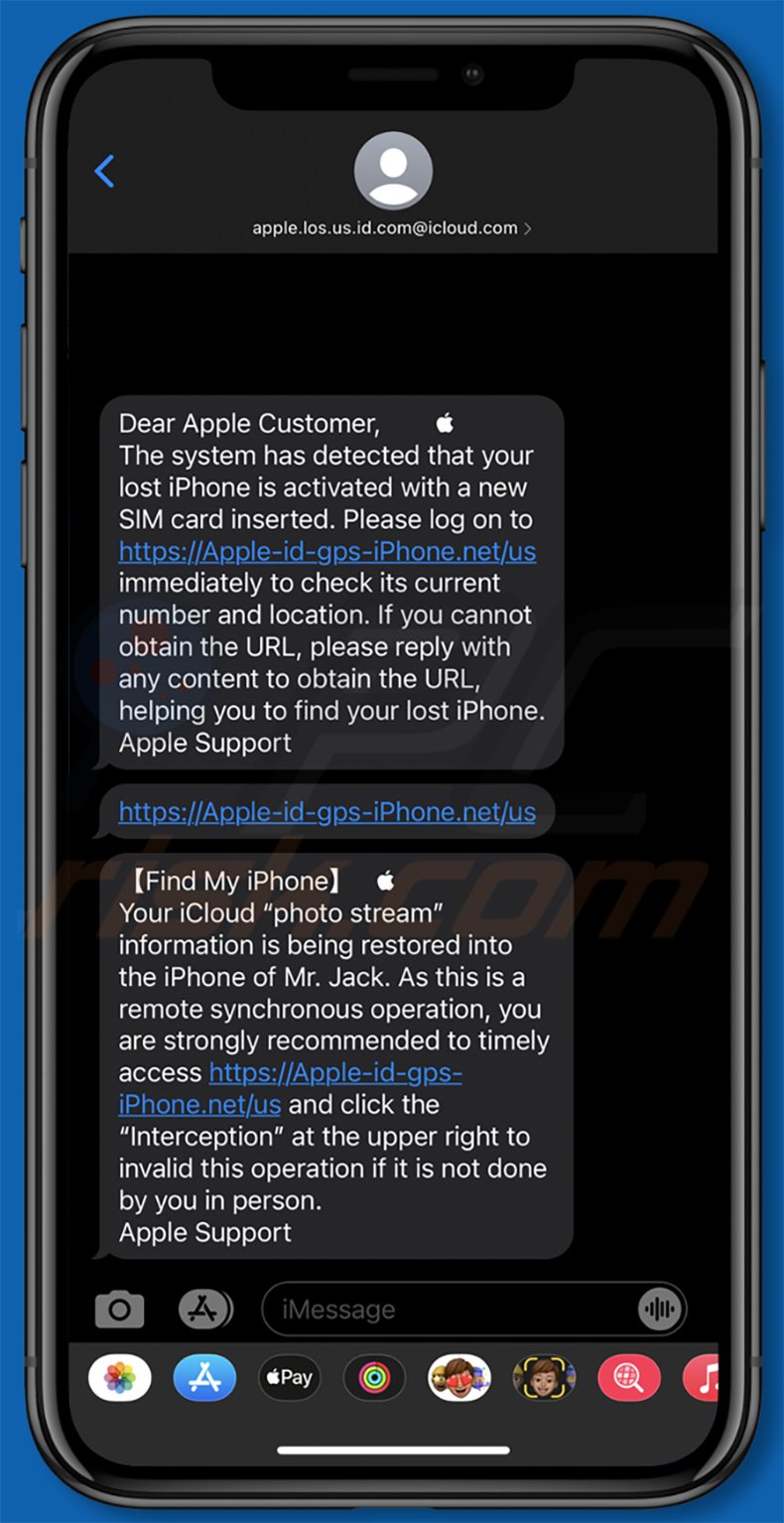
Text within these messages:
Dear Apple Customer,
The system has detected that your lost iPhone is activated with a new SIM card inserted. Please log on to hxxps://Apple-id-gps-iPhone.net/us immediately to check its current number and location. If you cannot obtain the URL, please reply with any content to obtain the URL, helping you to find your lost iPhone.
Apple Support
[Find My iPhone]
Your iCloud "photo stream" information is being restored into the iPhone of Mr. Jack. As this is a remote synchronous operation, you are strongly recommended to timely access hxxps://Apple-id-gps-iPhone.net/us and click the "Interception" at the upper right to invalid this operation if it is not done by you in person.
Apple Support
Example of an order shipping-themed smishing scam:
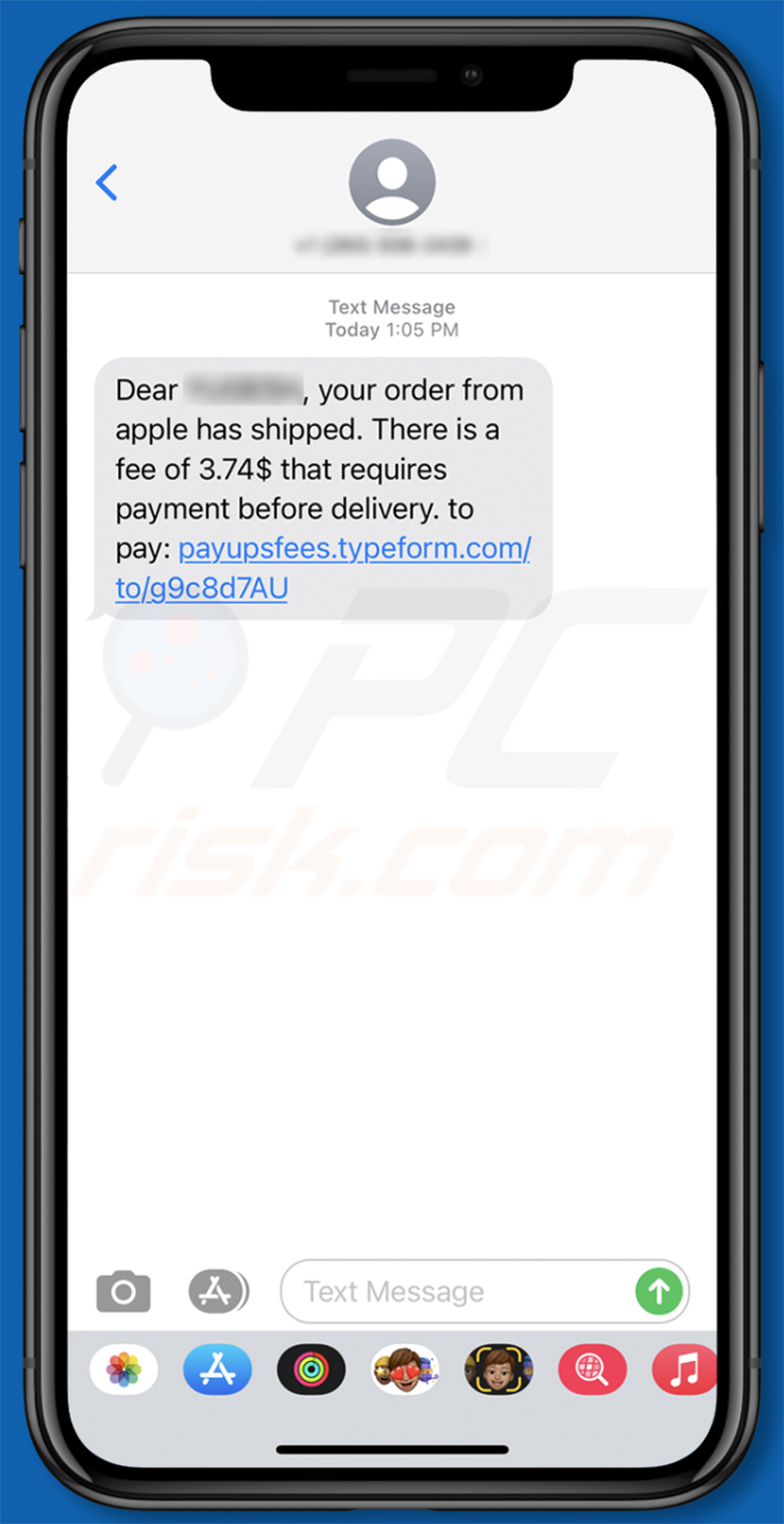
Text presented within:
Dear ********, your order from apple has shipped. There is a fee of 3.74$ that requires payment before delivery. to pay: payupsfees.typeform.com/to/g8c8d7AU
Yet another example of iPhone usage-themed smishing scam:
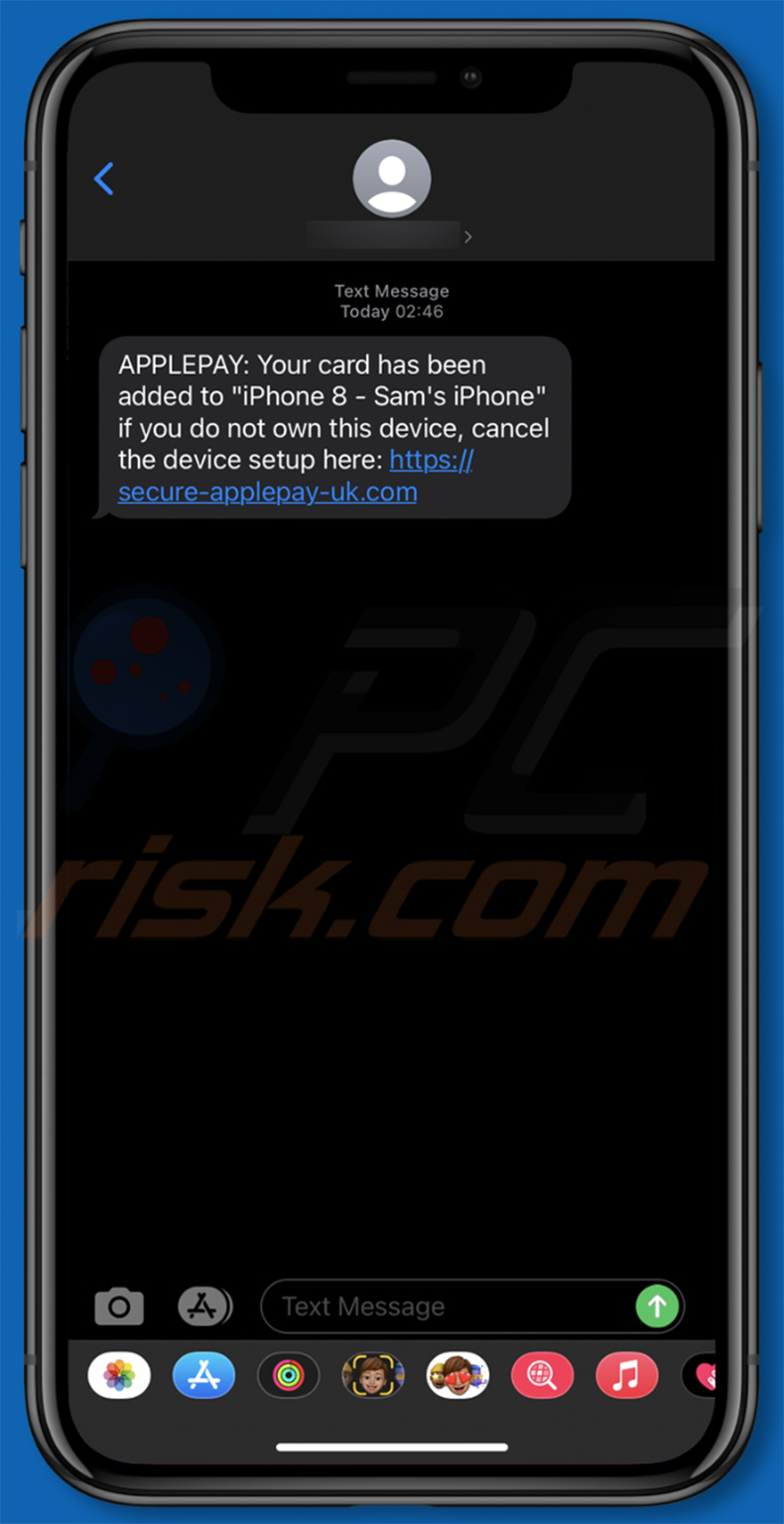
Text presented within:
APPLEPAY: Your card has been added to "iPhone 8 - Sam's iPhone" if you do not own this device, cancel the device setup here: hxxps://secure-applepay-uk.com
Another example of smishing messages, this time relating to Apple account security:
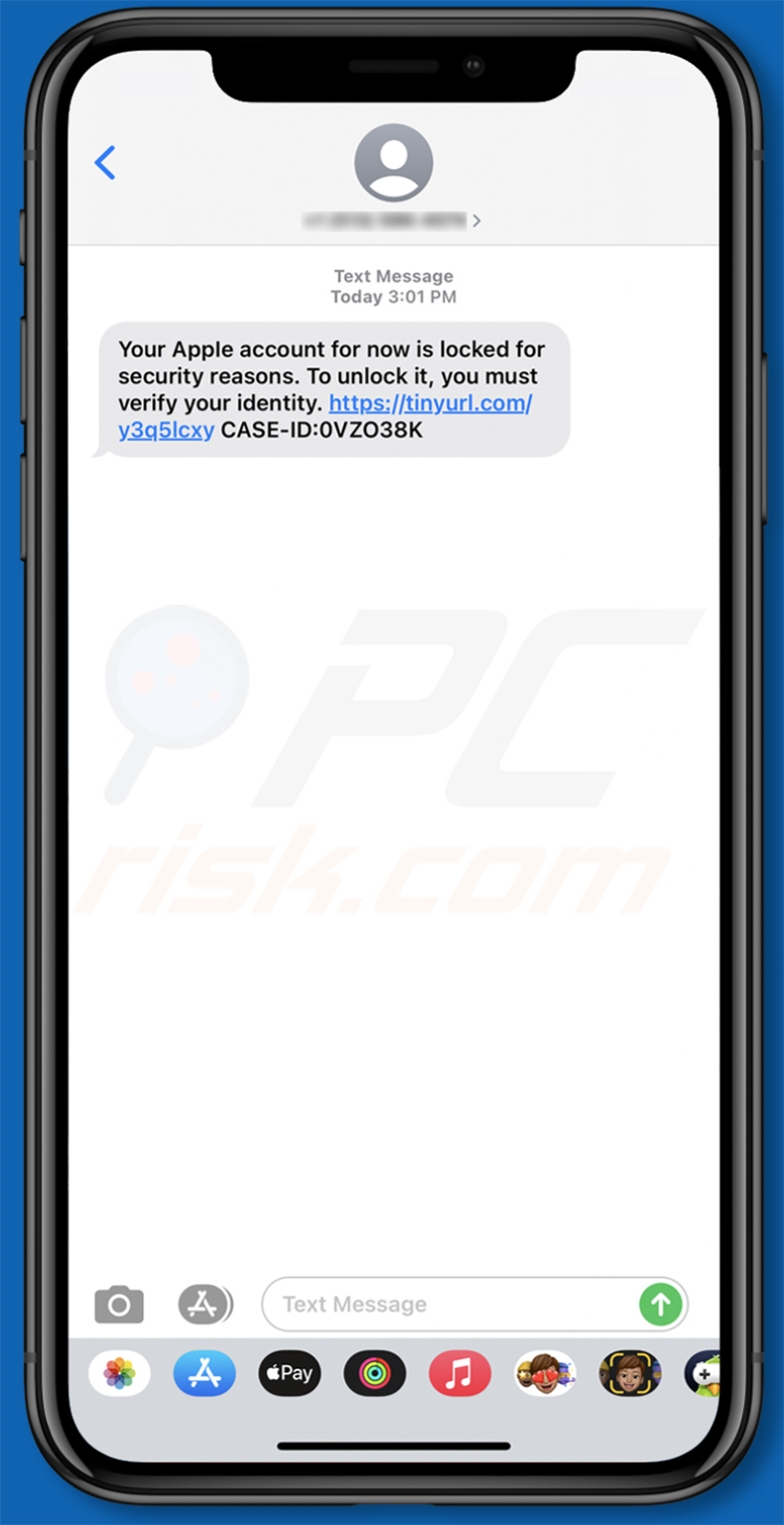
Text presented within:
Your Apple account is now locked for security reasons. To unlock it, you must verify your identity. hxxps://tinyurl.com/******** CASE-ID:-
Yet another example of an Apple ID-themed smishing message:
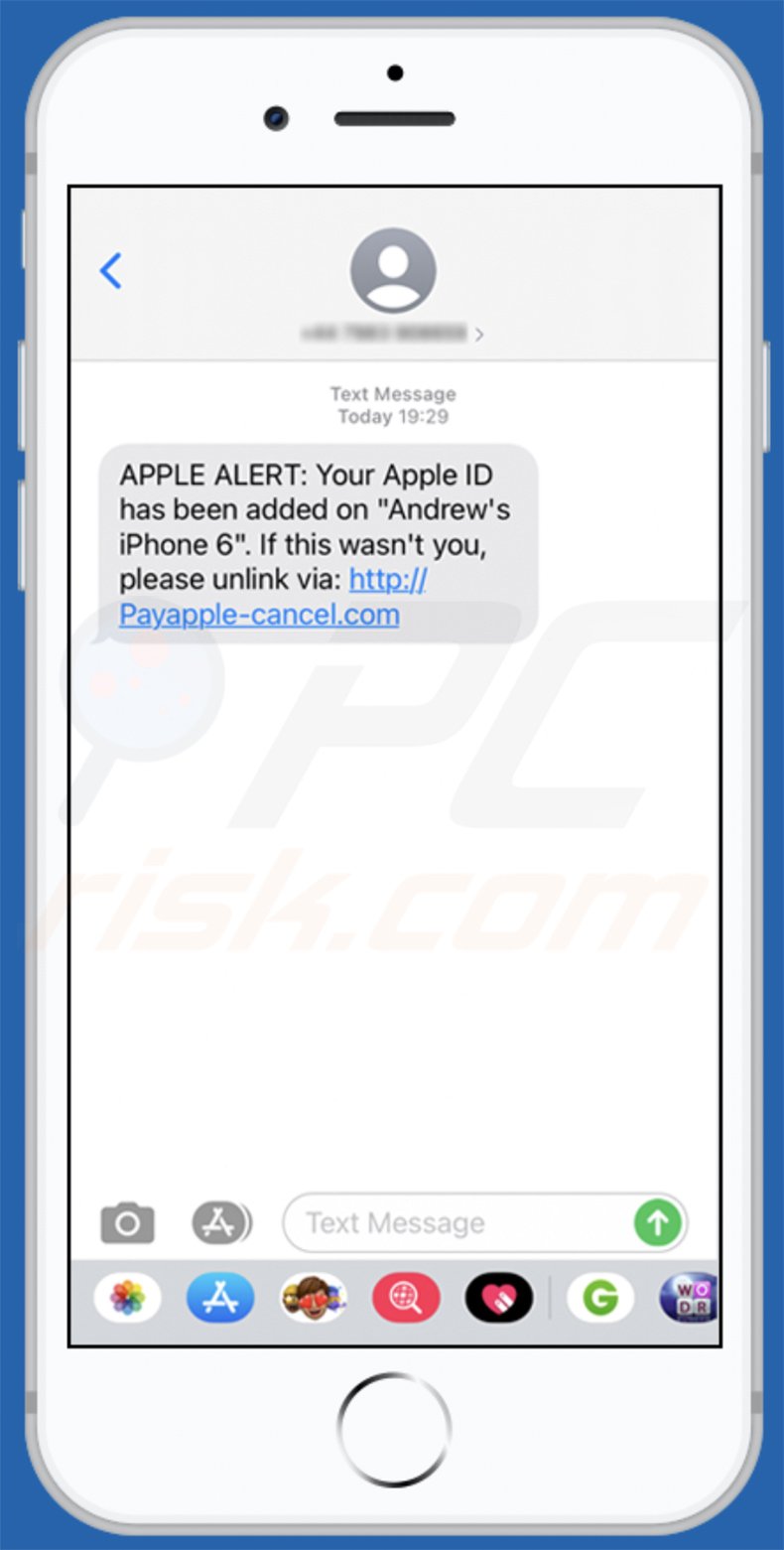
Text presented within:
APPLE ALERT: Your Apple ID has been added on "Andrew's iPhone 6". If this wasn't you, please unlink via: hxxp://Payapple-cancel[.]com
Yet another example of iPhone-themed smishing message:
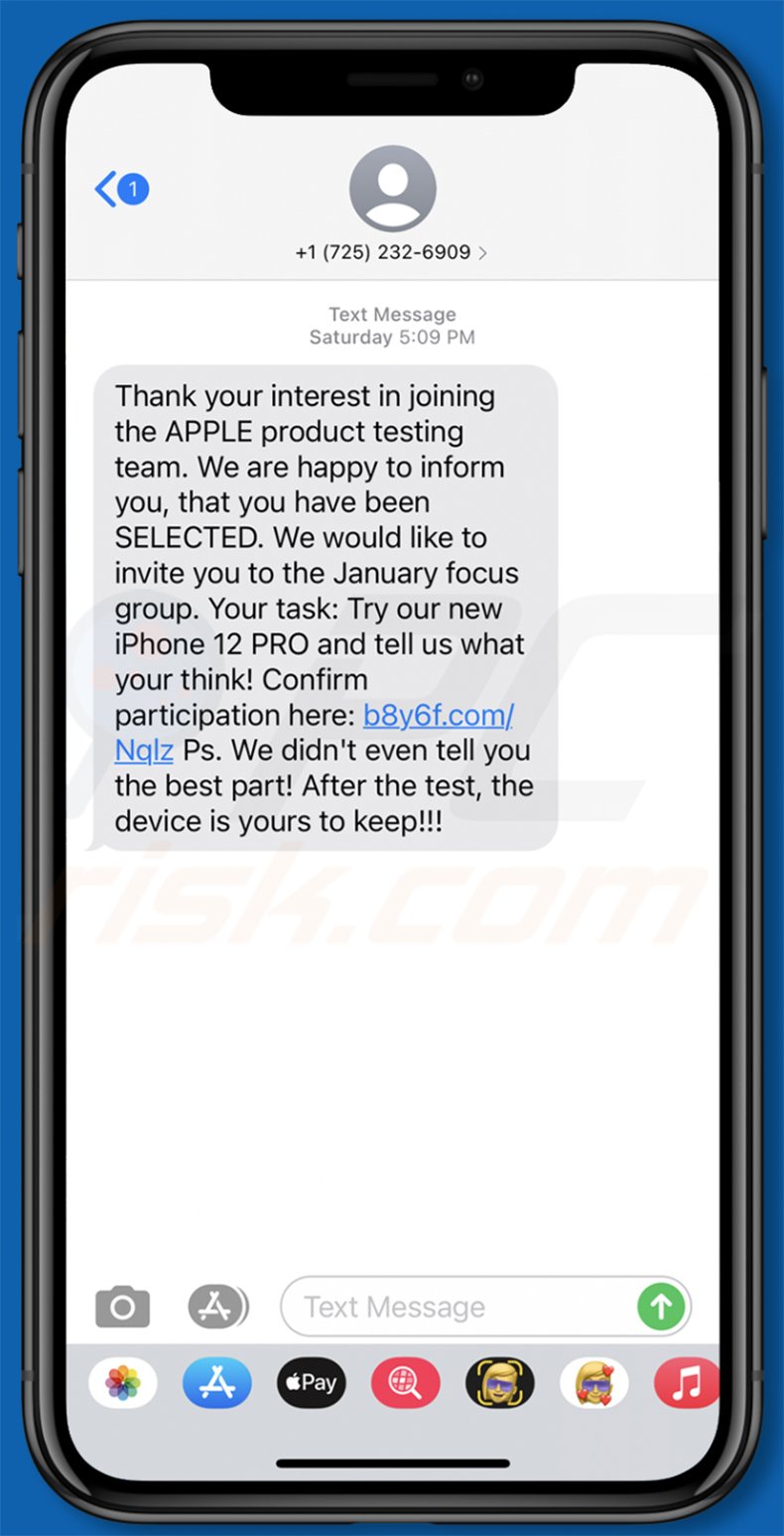
Text presented within:
Thank your interest in joining the APPLE product testing team. We are happy to inform you, that you have been SELECTED. We would like to invite you to the January focus group. Your task: Try our new iPhone 12 PRO and tell us what your think! Confirm your participation here: b8y6f.com/Nqlz Ps. We didn't even tell you the best part! After the test, the device is yours to keep!!!
Another example of an Apple account-themed smishing message:
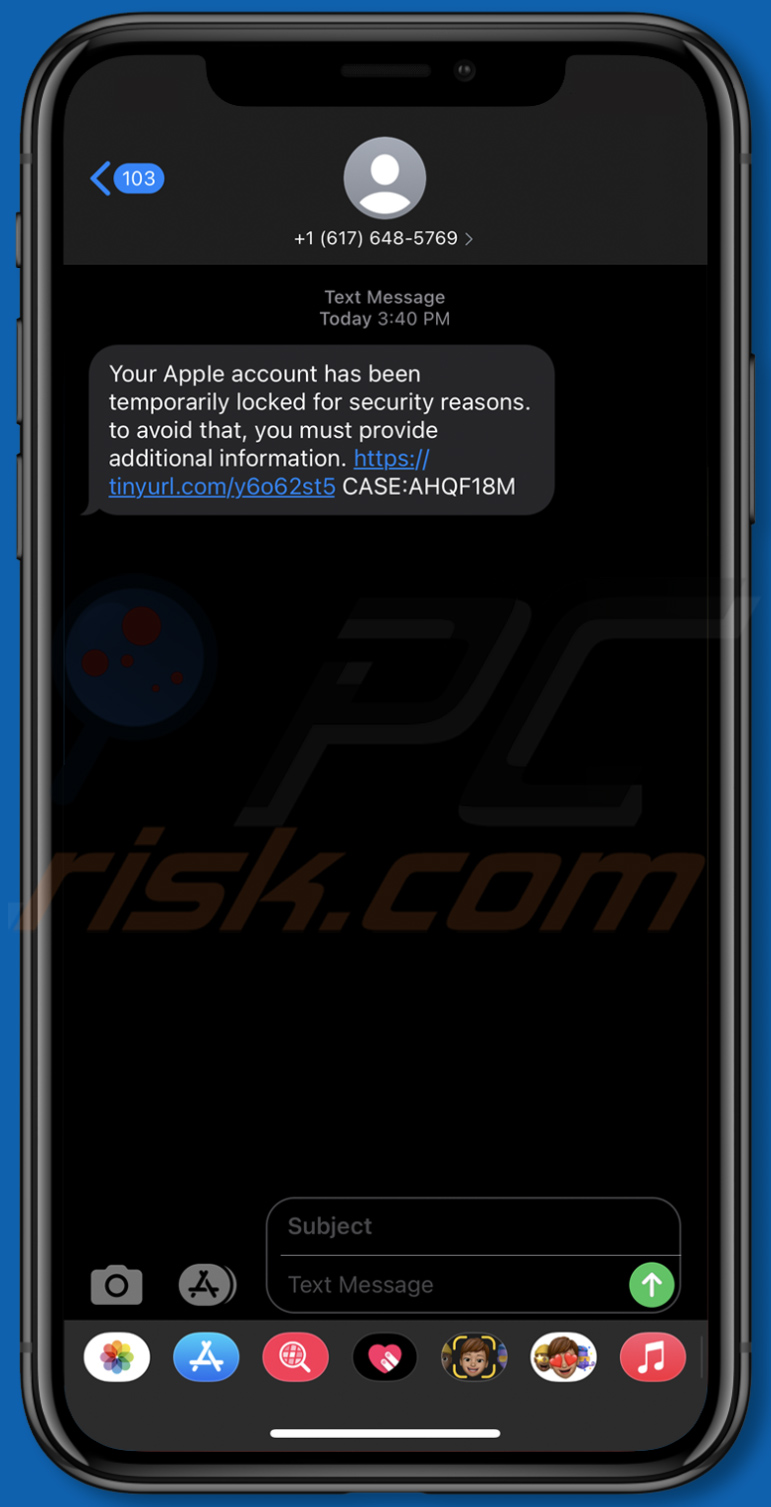
Text presented within:
Your Apple account has been temporarily locked for security reasons. to avoid that, you must provide additional information. hxxps://tinyurl[.]/****** CASE:AHQF18M
To enable pop-up blocking, fraudulent website warnings, and remove web browsing data in mobile Apple devices, follow these steps:
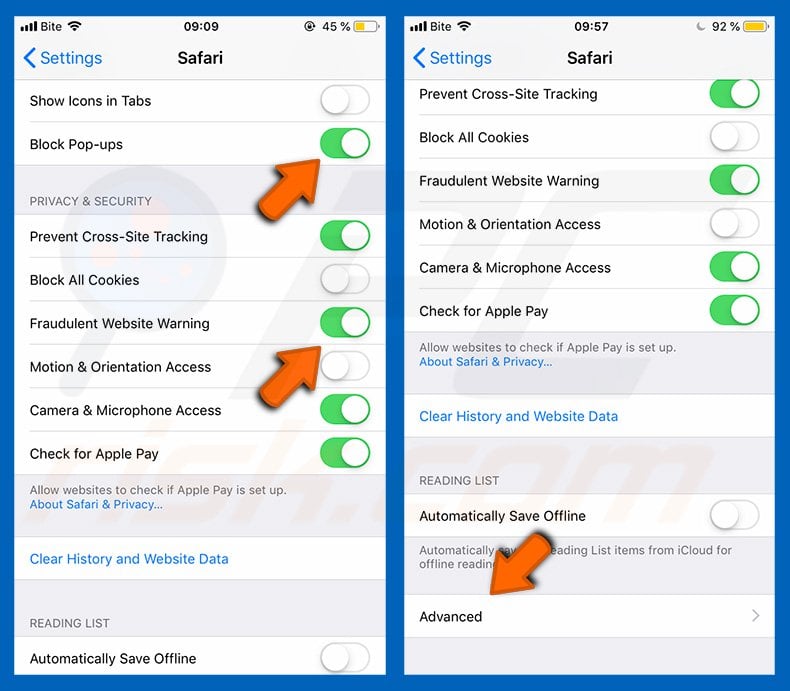
First, go to "Settings", and then scroll down to find and tap "Safari".

Check if the "Block Pop-ups" and "Fraudulent Website Warning" toggles are enabled. If not, enable them immediately. Then, scroll down and tap "Advanced".
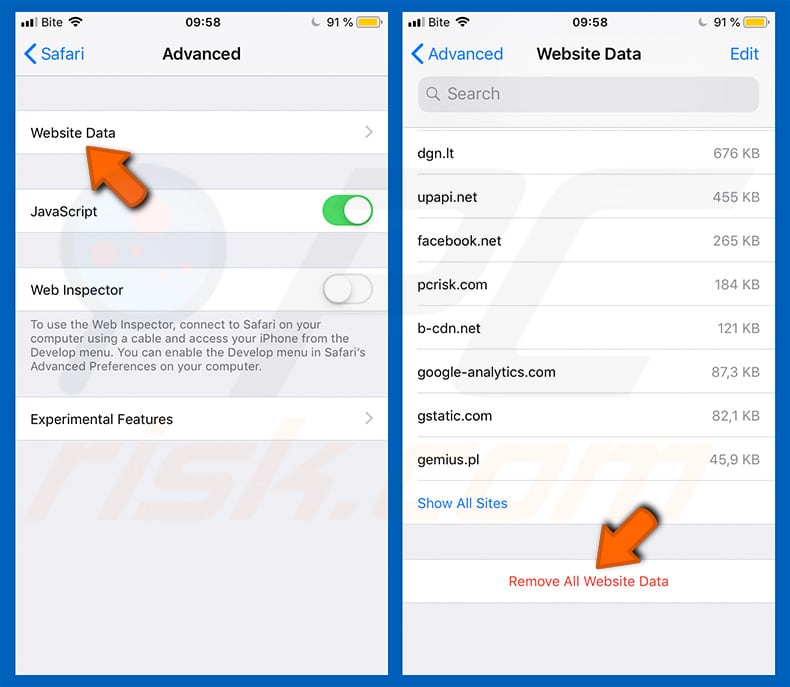
Tap "Website Data" and then "Remove All Website Data".
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is "Your iPhone is now online and located"?
- STEP 1. Remove PUA related files and folders from OSX.
- STEP 2. Remove rogue extensions from Safari.
- STEP 3. Remove rogue add-ons from Google Chrome.
- STEP 4. Remove potentially unwanted plug-ins from Mozilla Firefox.
Video showing how to remove adware and browser hijackers from a Mac computer:
Potentially unwanted applications removal:
Remove potentially unwanted applications from your "Applications" folder:
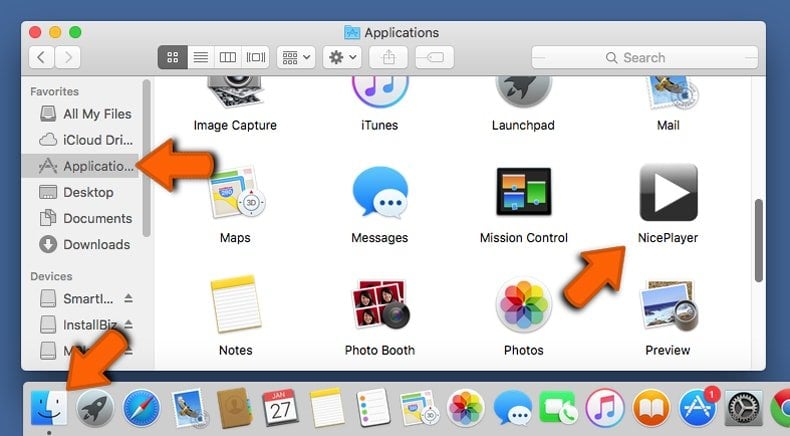
Click the Finder icon. In the Finder window, select "Applications". In the applications folder, look for "MPlayerX","NicePlayer", or other suspicious applications and drag them to the Trash. After removing the potentially unwanted application(s) that cause online ads, scan your Mac for any remaining unwanted components.
DOWNLOAD remover for malware infections
Combo Cleaner checks if your computer is infected with malware. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Remove adware-related files and folders
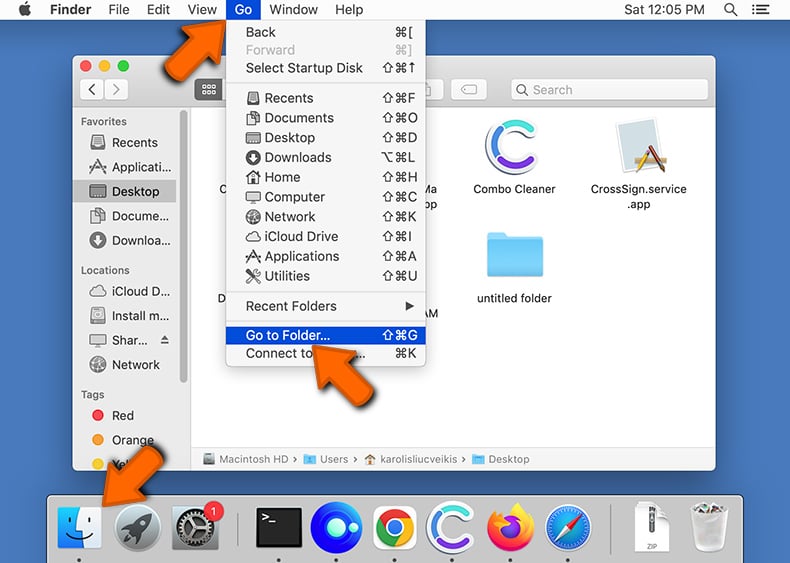
Click the Finder icon, from the menu bar. Choose Go, and click Go to Folder...
 Check for adware generated files in the /Library/LaunchAgents/ folder:
Check for adware generated files in the /Library/LaunchAgents/ folder:
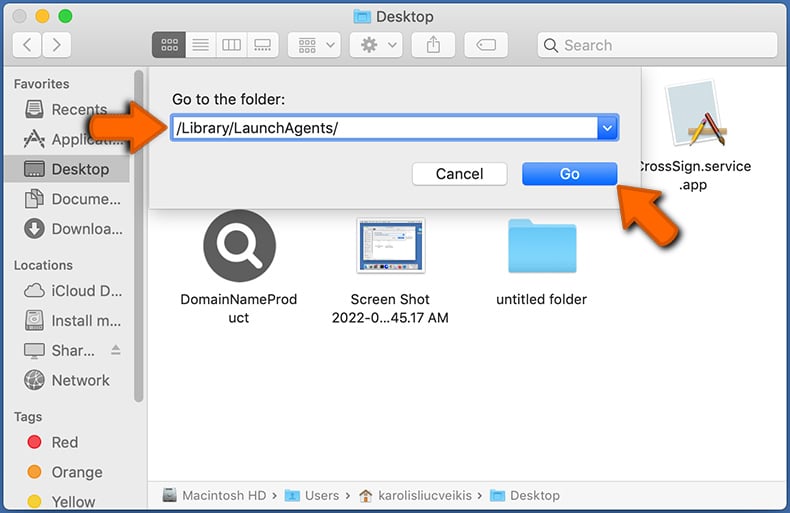
In the Go to Folder... bar, type: /Library/LaunchAgents/
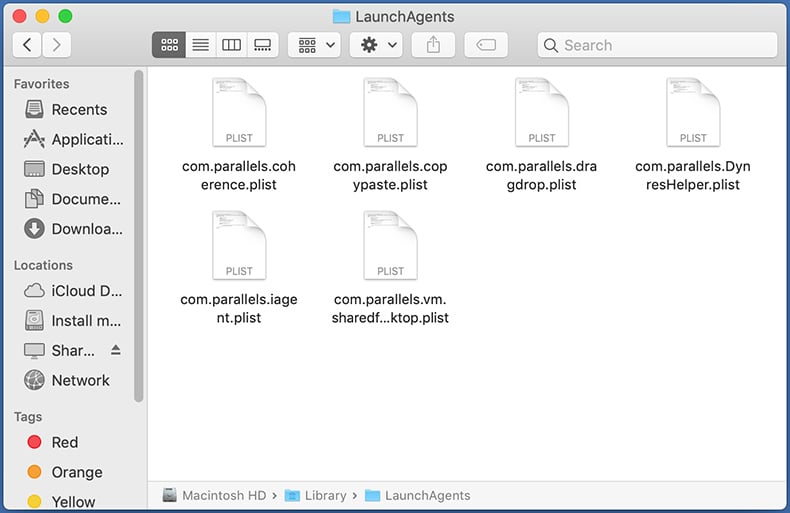
In the "LaunchAgents" folder, look for any recently-added suspicious files and move them to the Trash. Examples of files generated by adware - "installmac.AppRemoval.plist", "myppes.download.plist", "mykotlerino.ltvbit.plist", "kuklorest.update.plist", etc. Adware commonly installs several files with the exact same string.
 Check for adware generated files in the ~/Library/Application Support/ folder:
Check for adware generated files in the ~/Library/Application Support/ folder:
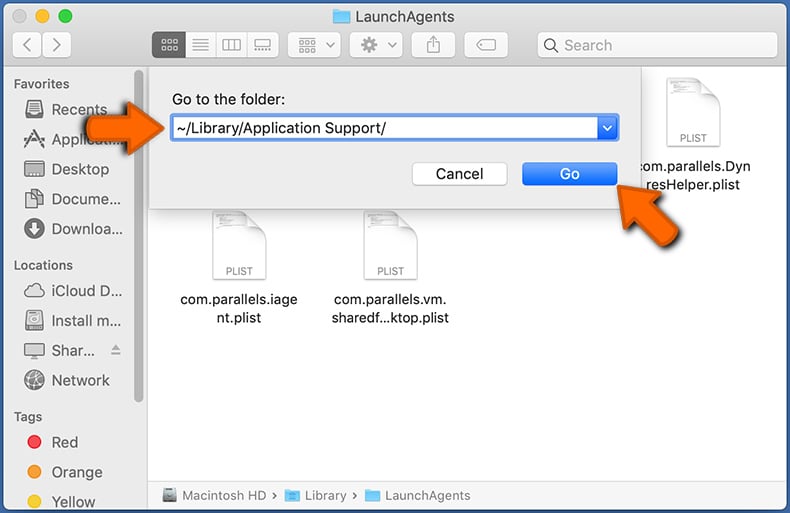
In the Go to Folder... bar, type: ~/Library/Application Support/
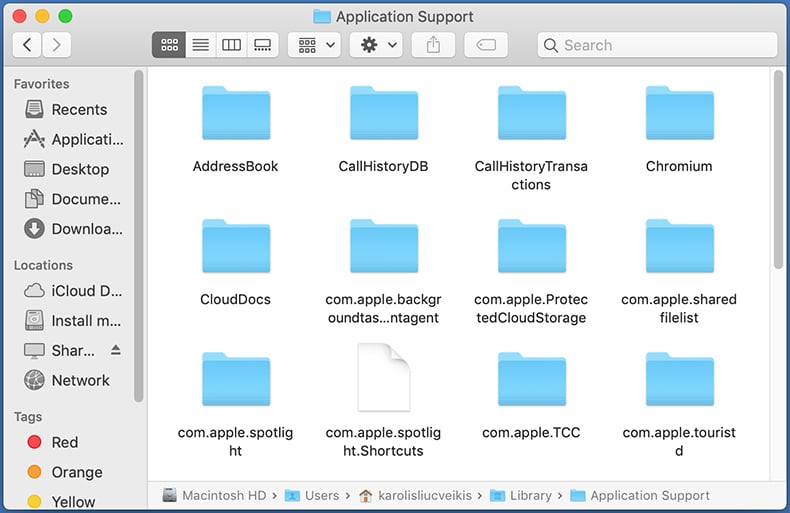
In the "Application Support" folder, look for any recently-added suspicious folders. For example, "MplayerX" or "NicePlayer", and move these folders to the Trash.
 Check for adware generated files in the ~/Library/LaunchAgents/ folder:
Check for adware generated files in the ~/Library/LaunchAgents/ folder:
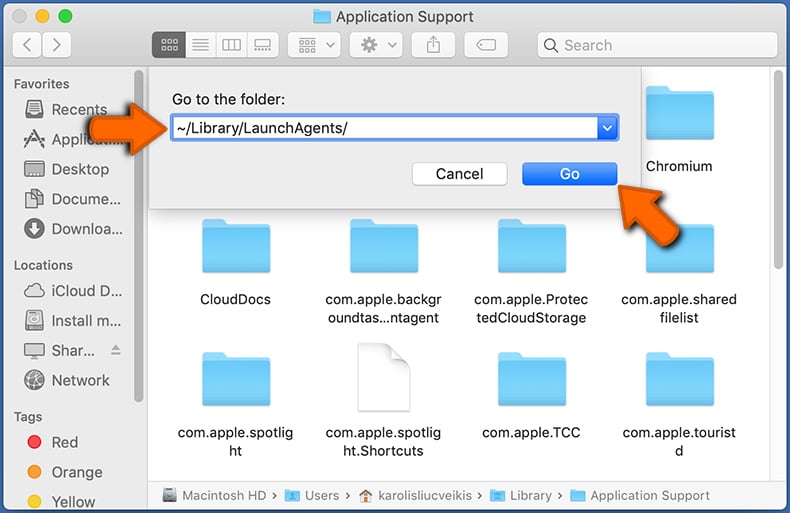
In the Go to Folder... bar, type: ~/Library/LaunchAgents/
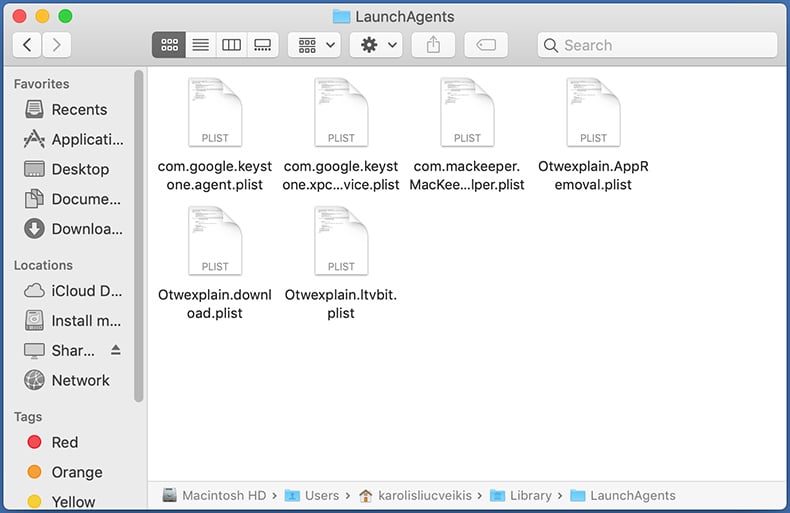
In the "LaunchAgents" folder, look for any recently-added suspicious files and move them to the Trash. Examples of files generated by adware - "installmac.AppRemoval.plist", "myppes.download.plist", "mykotlerino.ltvbit.plist", "kuklorest.update.plist", etc. Adware commonly installs several files with the exact same string.
 Check for adware generated files in the /Library/LaunchDaemons/ folder:
Check for adware generated files in the /Library/LaunchDaemons/ folder:
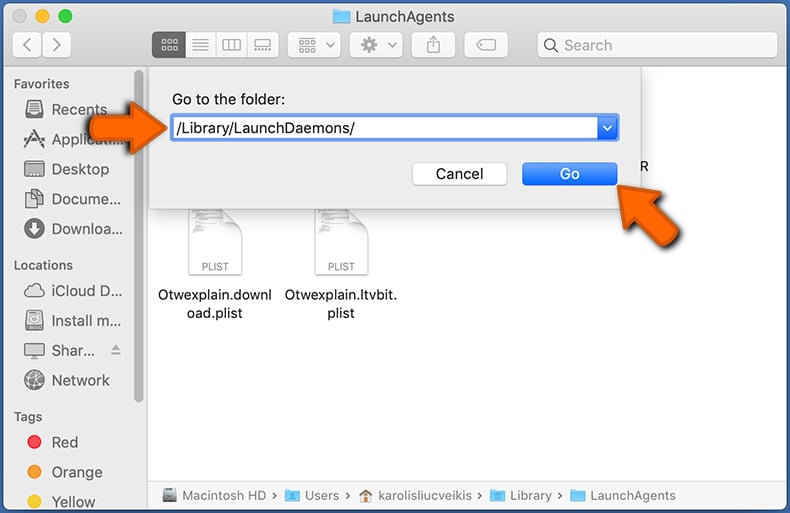
In the "Go to Folder..." bar, type: /Library/LaunchDaemons/
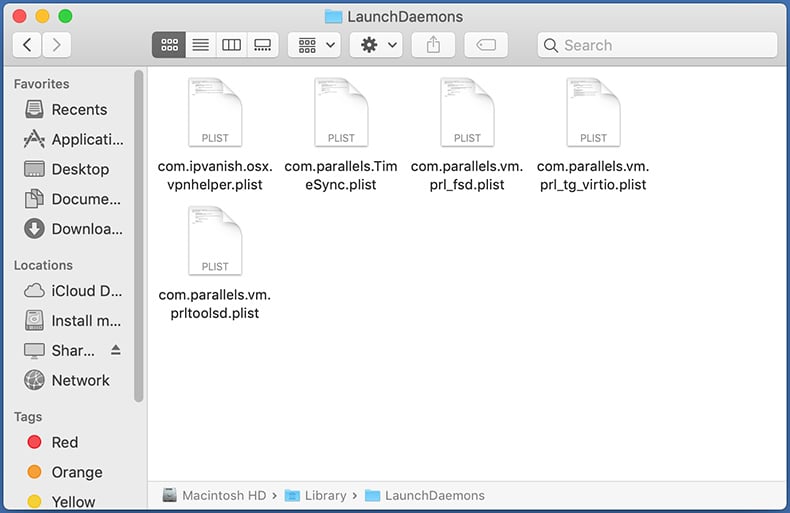
In the "LaunchDaemons" folder, look for recently-added suspicious files. For example "com.aoudad.net-preferences.plist", "com.myppes.net-preferences.plist", "com.kuklorest.net-preferences.plist", "com.avickUpd.plist", etc., and move them to the Trash.
 Scan your Mac with Combo Cleaner:
Scan your Mac with Combo Cleaner:
If you have followed all the steps correctly, your Mac should be clean of infections. To ensure your system is not infected, run a scan with Combo Cleaner Antivirus. Download it HERE. After downloading the file, double click combocleaner.dmg installer. In the opened window, drag and drop the Combo Cleaner icon on top of the Applications icon. Now open your launchpad and click on the Combo Cleaner icon. Wait until Combo Cleaner updates its virus definition database and click the "Start Combo Scan" button.
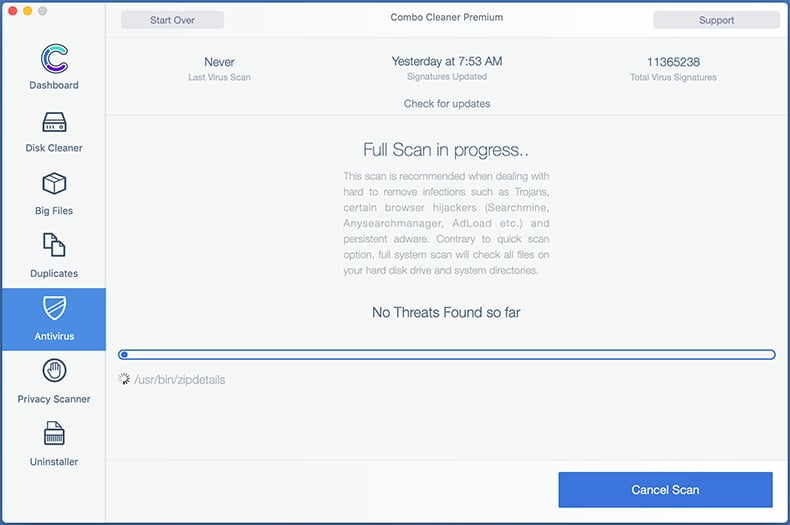
Combo Cleaner will scan your Mac for malware infections. If the antivirus scan displays "no threats found" - this means that you can continue with the removal guide; otherwise, it's recommended to remove any found infections before continuing.
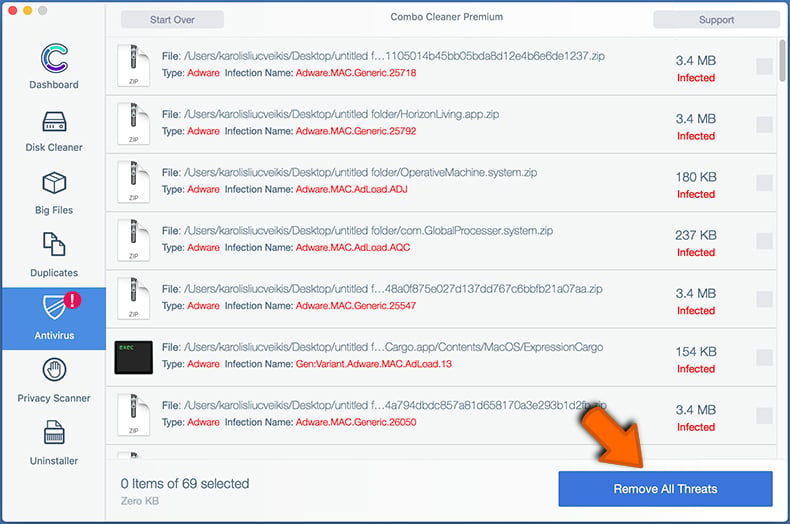
After removing files and folders generated by the adware, continue to remove rogue extensions from your Internet browsers.
Remove malicious extensions from Internet browsers
 Remove malicious Safari extensions:
Remove malicious Safari extensions:
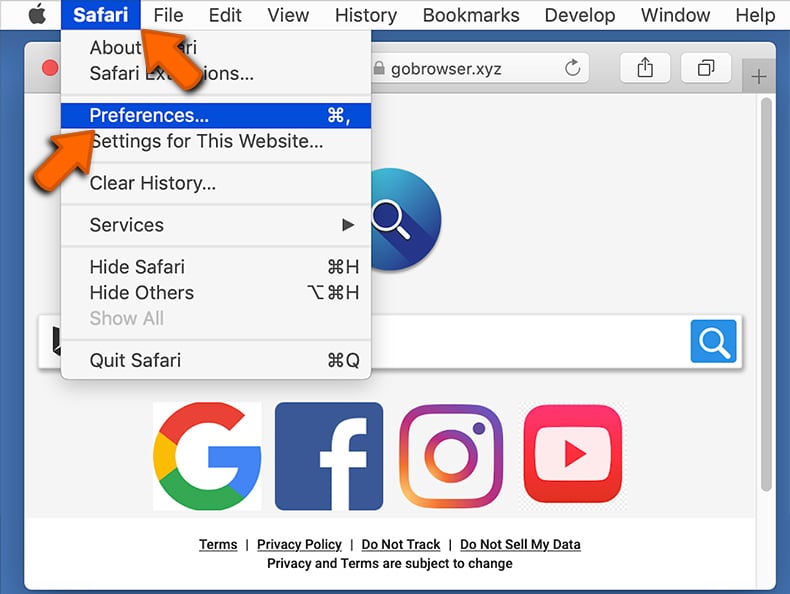
Open the Safari browser, from the menu bar, select "Safari" and click "Preferences...".
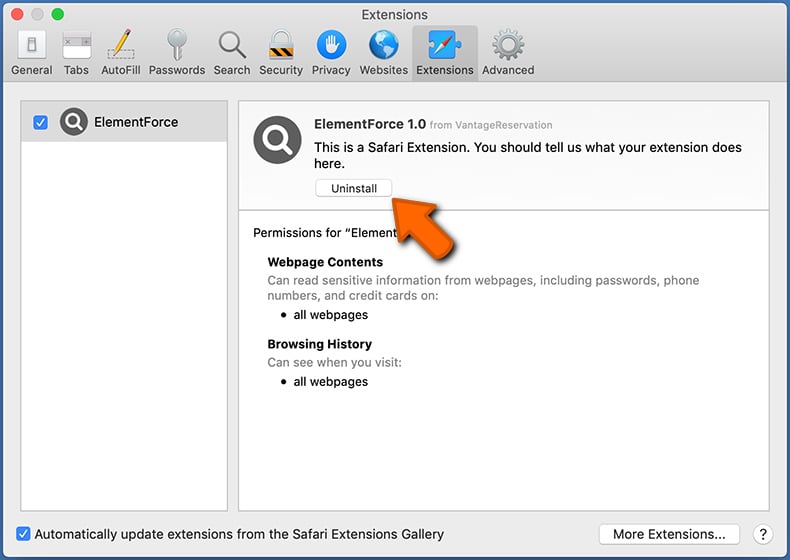
In the preferences window, select "Extensions" and look for any recently-installed suspicious extensions. When located, click the "Uninstall" button next to it/them. Note that you can safely uninstall all extensions from your Safari browser - none are crucial for regular browser operation.
- If you continue to have problems with browser redirects and unwanted advertisements - Reset Safari.
 Remove malicious extensions from Google Chrome:
Remove malicious extensions from Google Chrome:
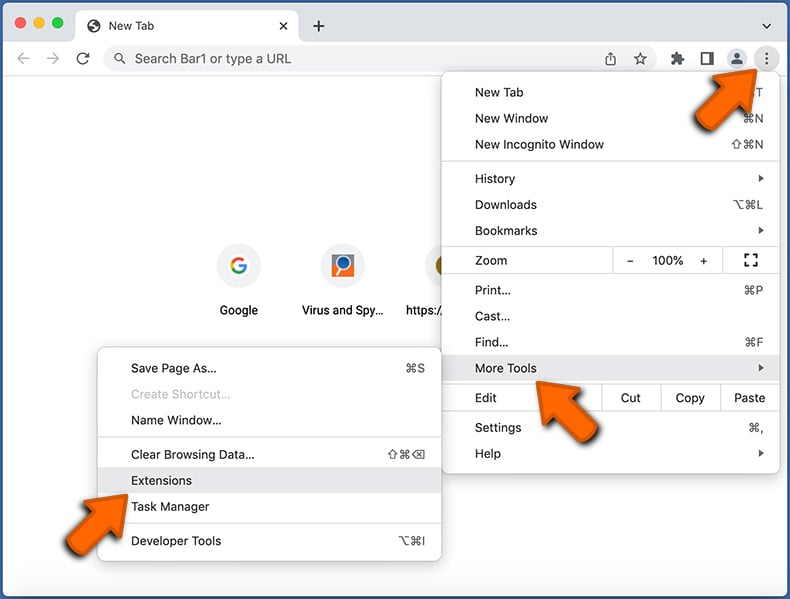
Click the Chrome menu icon ![]() (at the top right corner of Google Chrome), select "More Tools" and click "Extensions". Locate all recently-installed suspicious extensions, select these entries and click "Remove".
(at the top right corner of Google Chrome), select "More Tools" and click "Extensions". Locate all recently-installed suspicious extensions, select these entries and click "Remove".
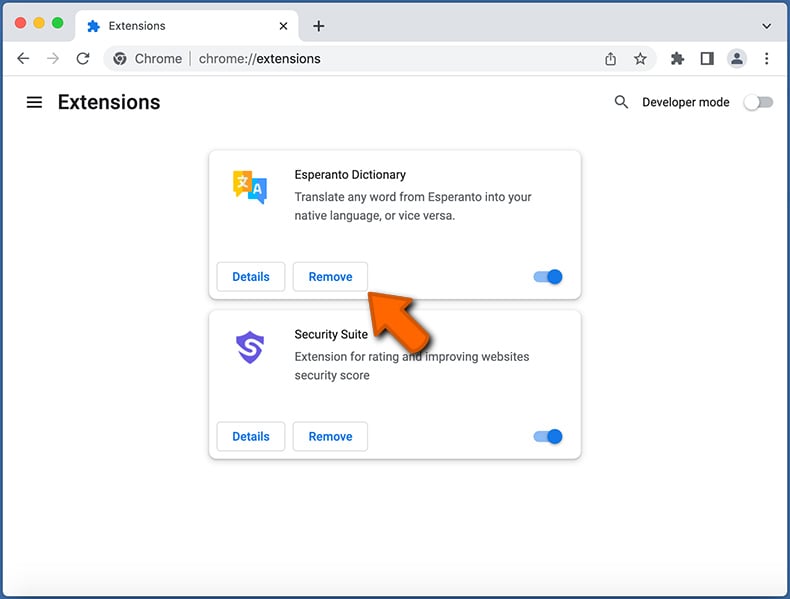
- If you continue to have problems with browser redirects and unwanted advertisements - Reset Google Chrome.
 Remove malicious extensions from Mozilla Firefox:
Remove malicious extensions from Mozilla Firefox:
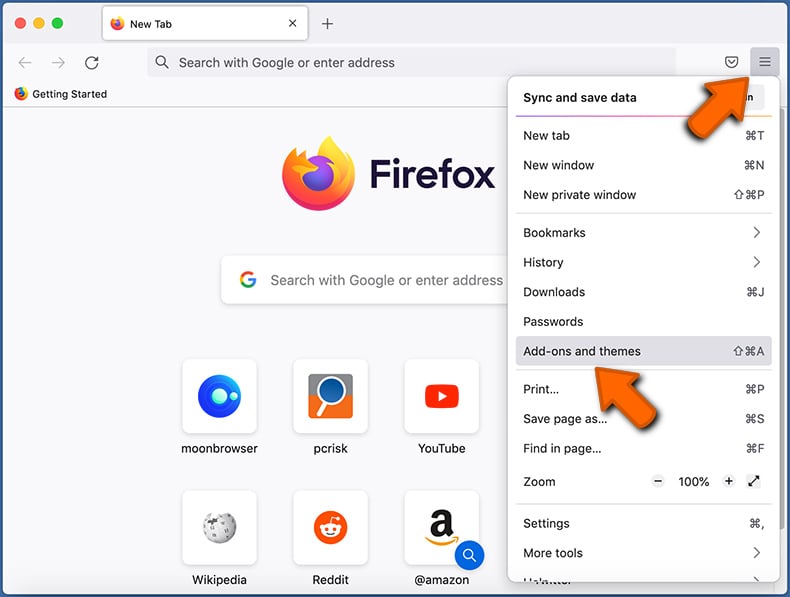
Click the Firefox menu ![]() (at the top right corner of the main window) and select "Add-ons and themes". Click "Extensions", in the opened window locate all recently-installed suspicious extensions, click on the three dots and then click "Remove".
(at the top right corner of the main window) and select "Add-ons and themes". Click "Extensions", in the opened window locate all recently-installed suspicious extensions, click on the three dots and then click "Remove".
- If you continue to have problems with browser redirects and unwanted advertisements - Reset Mozilla Firefox.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion