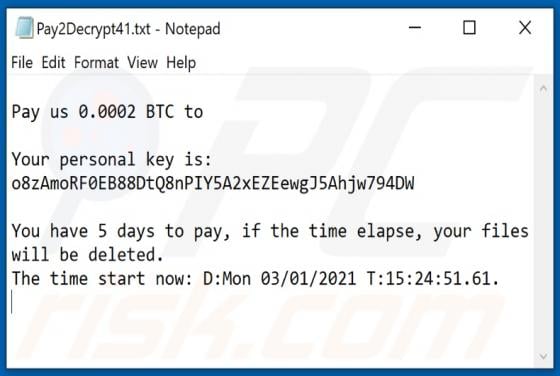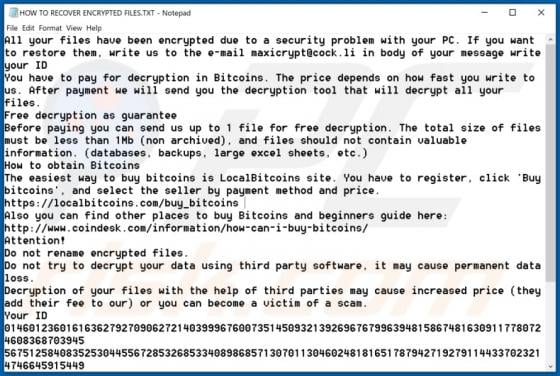
Maxi Ransomware
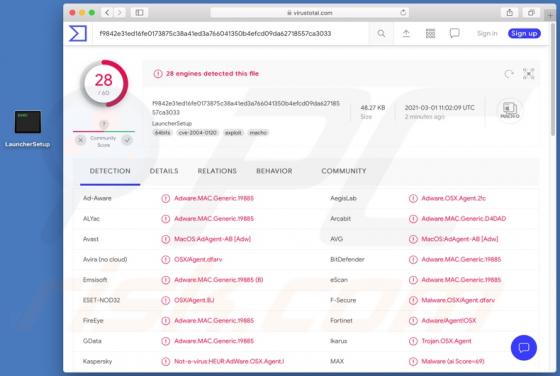
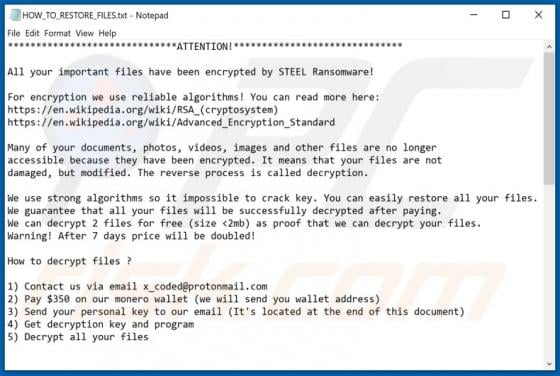
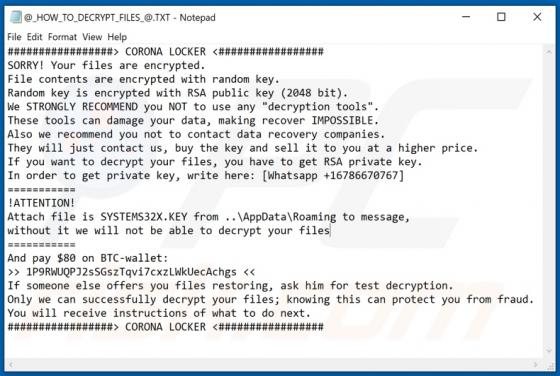
Maxi is a type of malware that encrypts files and keeps them inaccessible unless they are decrypted with tools held only by the attackers. Maxi also renames encrypted files by adding the maxicrypt@cock.li email address and appending the ".maxi" extension to filenames. For example, "1.jpg" is rena