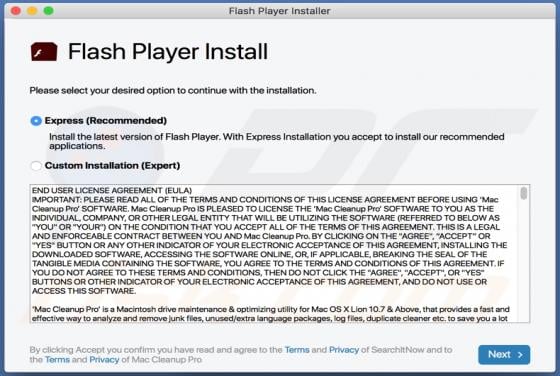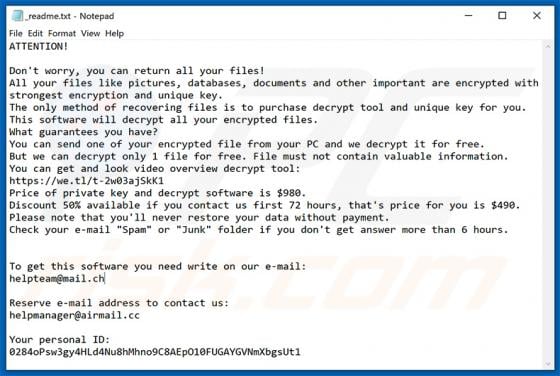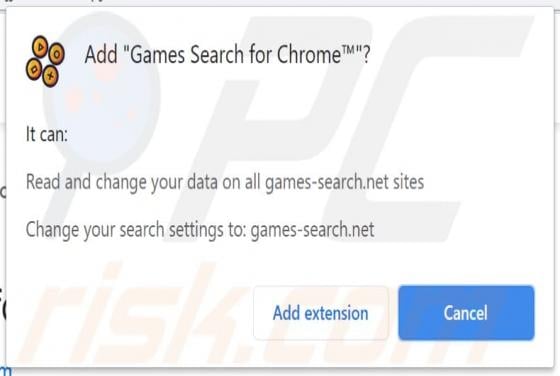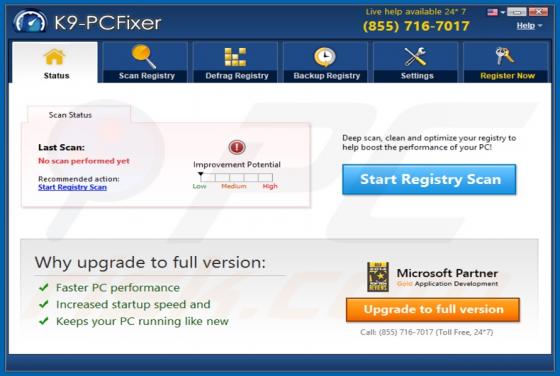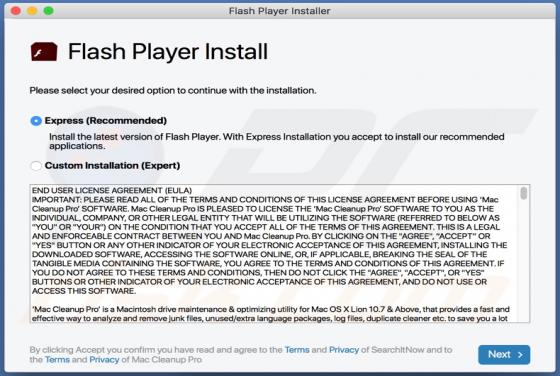
SkilledPanelSearch Adware (Mac)
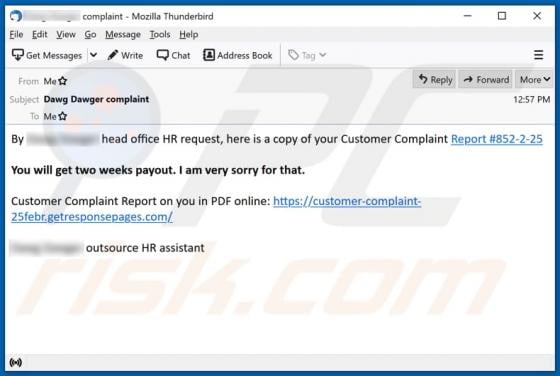
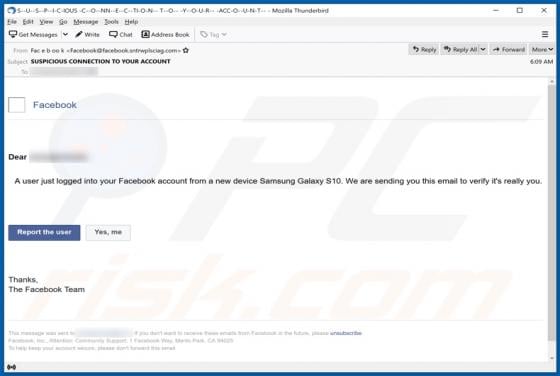
SkilledPanelSearch generates advertisements and alters the settings of browsers to promote a fake search engine. For this reason, SkilledPanelSearch is classified as not only an adware-type app, but also as a browser hijacker. These apps often gather information relating to internet browsing ac