How to spot scams like "I monitored your device on the net for a long time"
Phishing/ScamAlso Known As: I Monitored Your Device On The Net For A Long Time spam
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What kind of scam is "I monitored your device on the net for a long time"?
Sextortion emails are scams whereby scammers claim to have hacked into computers and recorded humiliating videos of recipients watching adult videos. Generally, scammers threaten to send the videos to other people on their contact lists unless recipients pay ransoms (usually in cryptocurrencies).
Ignore these emails, especially when computers have no webcam connected or integrated with them.
More about the "I monitored your device on the net for a long time" scam email
Scammers behind this email claim to have monitored the device for an extensive period, managed to hack it, and infect it with a virus. According to the scammers, they have access to the camera, microphone, messengers, telephone book, passwords to all social networks, etc.
Scammers attempt to trick recipients into believing that they have used the connected/integrated webcam and access to the screen to record videos of recipients watching pornography. Unless recipients pay US$1200 (equivalent in Bitcoins) to the provided BTC wallet address within 48 hours, they state that the videos will be uploaded to social networks.
Do not respond to these emails and, more importantly, do not pay the scammers. Remove the emails by marking them as spam.
Note that scammers behind such emails can use a spoofing technique to make it appear as if the emails are delivered from specific senders. I.e., scammers forge the sender's address to trick recipients into believing that they have received the email from people they know. Commonly, scammers make the sender's address identical as the recipient's.
| Name | I Monitored Your Device On The Net For A Long Time Email Scam |
| Threat Type | Phishing, Scam, Social Engineering, Fraud |
| Fake Claim | Scammers claim to have recorded a humiliating video and threaten to release (publish) it |
| Ransom Amount | US$1200 equivalent in Bitcoins |
| Cyber Criminal Cryptowallet Address | bc1qnkxjyxtdjmr8tkwzfz2t3rc4scdmnr4ll99kg9, bc1qpae26vlj5dnlxgwt2xjyw69sz3e596xs9xtwkn, bc1qyg3srjs0gz9l97xdp00vms4sgxa3ymj7aw7vae, bc1qvq53pjvx0gp3c5znercq6xvksps7vza5lh6ham, bc1qljx0ltxe0s2rhh7w0x9qzuhcdw0j79t0a6pxvv, 18bSTrufLfuvHwS7JYuF626MBGULSmxTgR |
| Symptoms | Unauthorized online purchases, changed online account passwords, identity theft, illegal access of the computer. |
| Distribution methods | Deceptive emails, rogue online pop-up ads, search engine poisoning techniques, misspelled domains. |
| Damage | Loss of sensitive private information, monetary loss, identity theft. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Examples of similar scams
More examples of email scams are "COVID-19 Vaccination NHS Email Scam", "Ruralvía Seguridad Email Scam" and "Stopped Processing Incoming Emails Scam".
Note that scammers/cyber criminals can use emails to trick recipient into providing sensitive information (e.g., credit card details, login credentials, social security numbers) and into opening malicious files designed to install rogue software (e.g., ransomware, Trojan-type malware).
How do spam campaigns infect computers?
Systems are often infected via malicious files distributed through spam campaigns. These files can be attached and/or linked inside the emails. Infectious files can be in various formats (e.g. Microsoft Office and PDF documents, archive and executable files, JavaScript, etc.).
When these files are executed, run or otherwise opened, the infection process (i.e. malware download/installation) is triggered. For example, Microsoft Office documents (e.g. "Invoice_24077.xlsb") cause infections by executing malicious macro commands.
In Microsoft Office versions released prior to 2010, malware download/installation begins when an infectious document is opened, however, newer versions have "Protected View" mode that prevents automatic execution of macros. Instead, users are asked to enable macro commands (i.e., to enable editing/content) and hence infection processes can only be started by manually enabling macros.
How to avoid installation of malware
Download software and files from official websites and via direct links. It is not safe to use torrent clients, eMule (or other Peer-to-Peer networks), third party downloaders, unofficial websites or other sources of this kind.
Avoid third party installers. Check "Advanced", "Custom" and other settings, and decline offers to download or install unwanted software. Do not click ads that are displayed on dubious websites, since they can open other untrusted websites or even cause unwanted downloads and installations.
Remove any unwanted, suspicious applications (extensions, add-ons, and plug-ins) that are installed on the browser. The same should be applied to programs of this kind that are installed on the operating system.
Regularly scan your computer with reputable antivirus or anti-spyware software and keep this software up to date.
If you have already opened malicious attachments, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Appearance of the email (GIF):
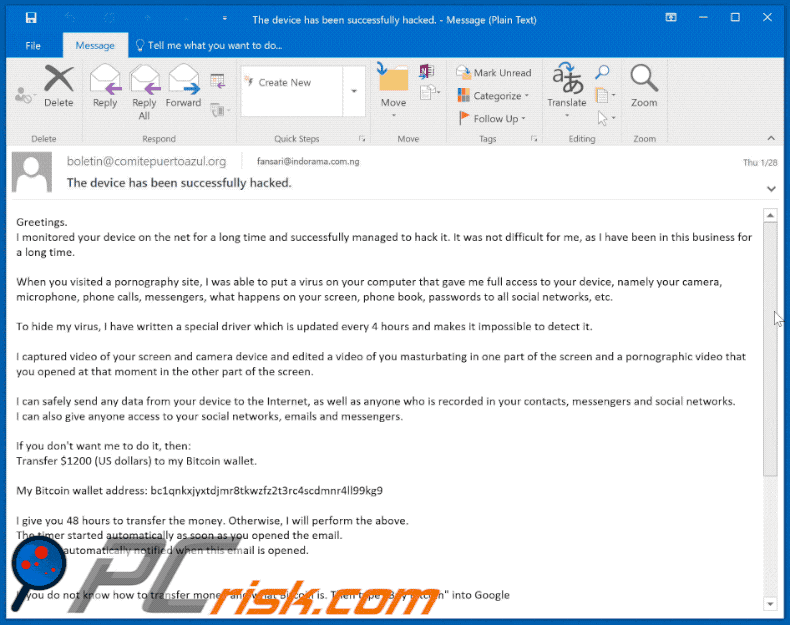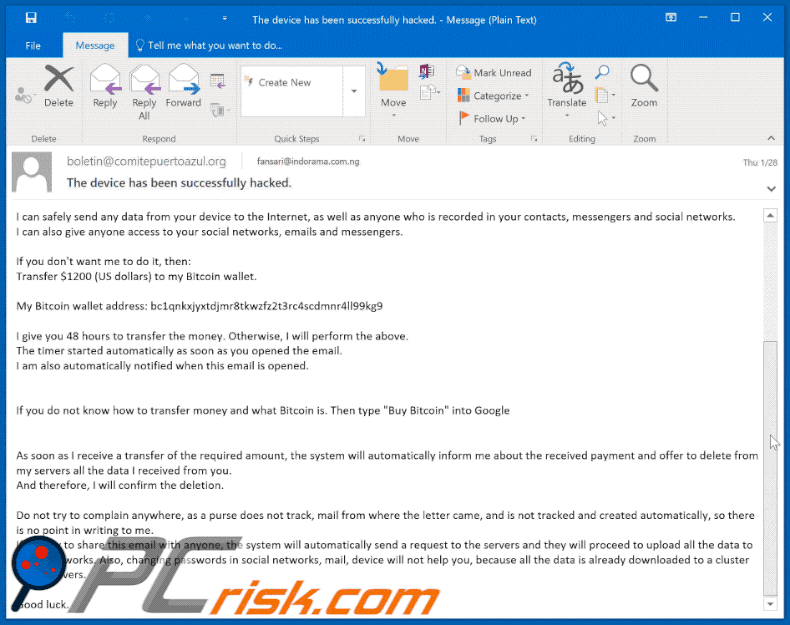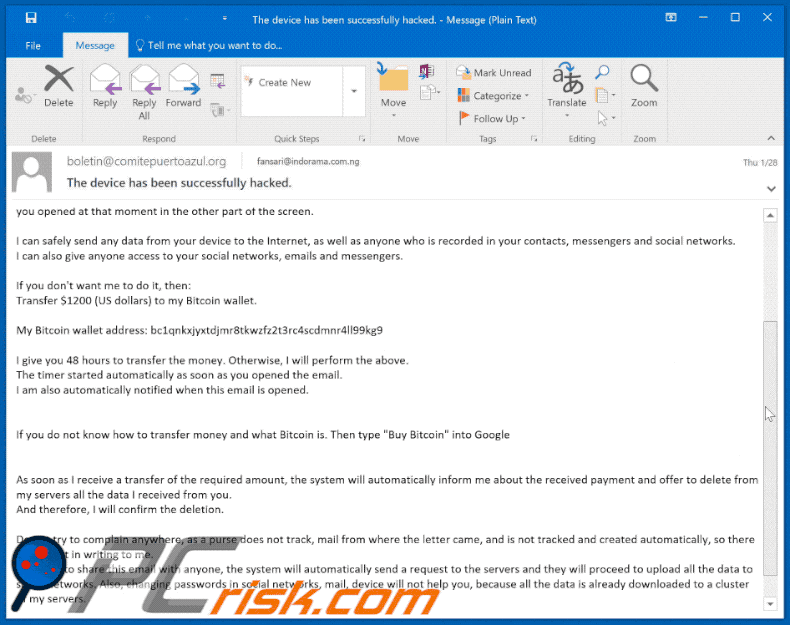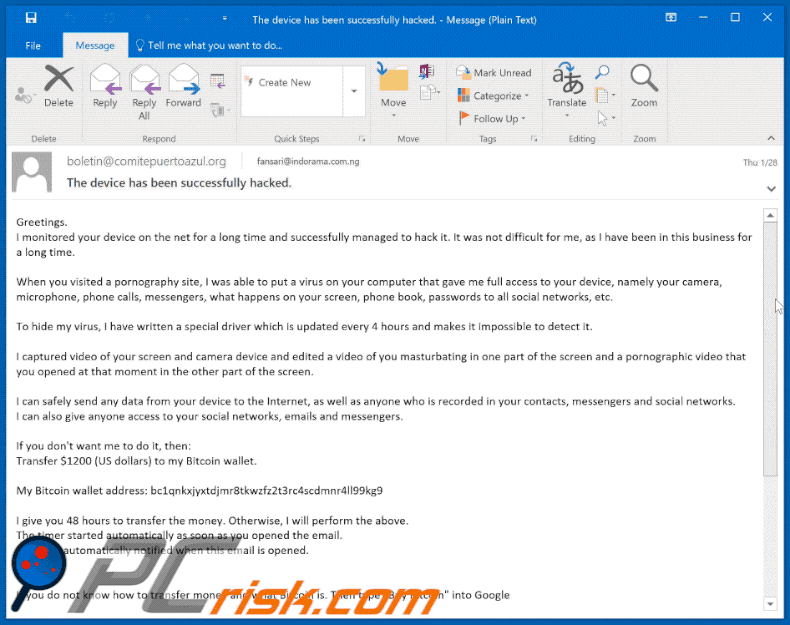
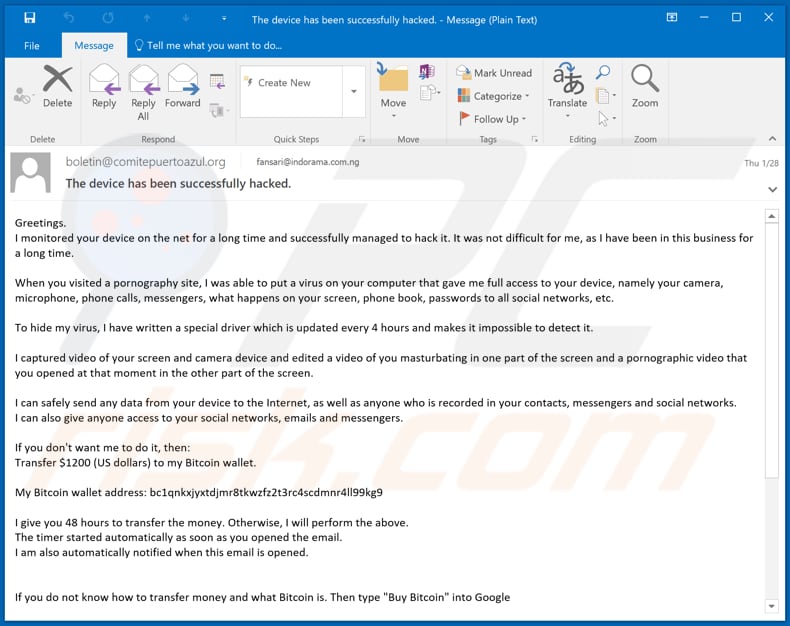
Text in the email:
Subject: The device has been successfully hacked.
Greetings.
I monitored your device on the net for a long time and successfully managed to hack it. It was not difficult for me, as I have been in this business for a long time.When you visited a pornography site, I was able to put a virus on your computer that gave me full access to your device, namely your camera, microphone, phone calls, messengers, what happens on your screen, phone book, passwords to all social networks, etc.
To hide my virus, I have written a special driver which is updated every 4 hours and makes it impossible to detect it.
I captured video of your screen and camera device and edited a video of you masturbating in one part of the screen and a pornographic video that you opened at that moment in the other part of the screen.
I can safely send any data from your device to the Internet, as well as anyone who is recorded in your contacts, messengers and social networks.
I can also give anyone access to your social networks, emails and messengers.If you don't want me to do it, then:
Transfer $1200 (US dollars) to my Bitcoin wallet.My Bitcoin wallet address: bc1qnkxjyxtdjmr8tkwzfz2t3rc4scdmnr4ll99kg9, bc1qpae26vlj5dnlxgwt2xjyw69sz3e596xs9xtwkn, bc1qljx0ltxe0s2rhh7w0x9qzuhcdw0j79t0a6pxvv
I give you 48 hours to transfer the money. Otherwise, I will perform the above.
The timer started automatically as soon as you opened the email.
I am also automatically notified when this email is opened.
If you do not know how to transfer money and what Bitcoin is. Then type "Buy Bitcoin" into Google
As soon as I receive a transfer of the required amount, the system will automatically inform me about the received payment and offer to delete from my servers all the data I received from you.
And therefore, I will confirm the deletion.Do not try to complain anywhere, as a purse does not track, mail from where the letter came, and is not tracked and created automatically, so there is no point in writing to me.
If you try to share this email with anyone, the system will automatically send a request to the servers and they will proceed to upload all the data to social networks. Also, changing passwords in social networks, mail, device will not help you, because all the data is already downloaded to a cluster of my servers.Good luck.
A Czech variant of "I Monitored Your Device On The Net For A Long Time" scam email:
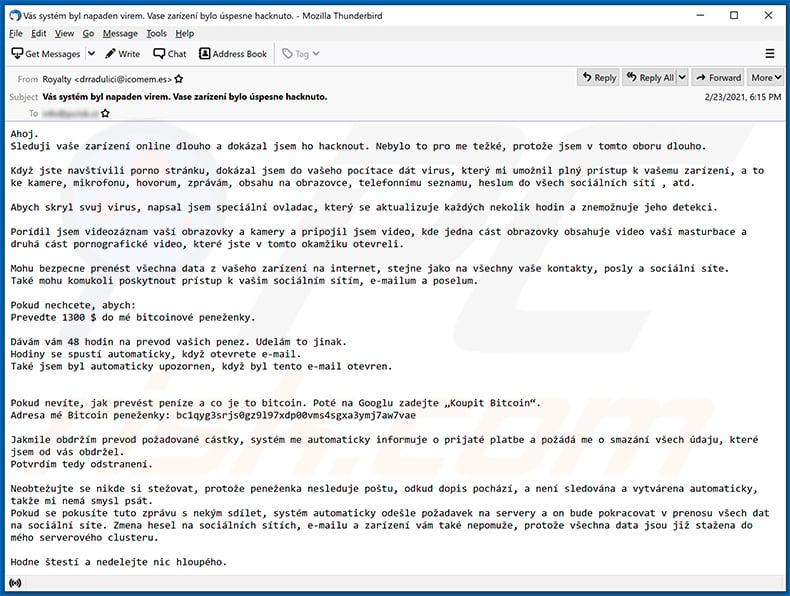
Text presented within:
Subject: Vás systém byl napaden virem. Vase zarízení bylo úspesne hacknuto.
Ahoj.
Sleduji vaše zarízení online dlouho a dokázal jsem ho hacknout. Nebylo to pro me težké, protože jsem v tomto oboru dlouho.Když jste navštívili porno stránku, dokázal jsem do vašeho pocítace dát virus, který mi umožnil plný prístup k vašemu zarízení, a to ke kamere, mikrofonu, hovorum, zprávám, obsahu na obrazovce, telefonnímu seznamu, heslum do všech sociálních sítí , atd.
Abych skryl svuj virus, napsal jsem speciální ovladac, který se aktualizuje každých nekolik hodin a znemožnuje jeho detekci.
Porídil jsem videozáznam vaší obrazovky a kamery a pripojil jsem video, kde jedna cást obrazovky obsahuje video vaší masturbace a druhá cást pornografické video, které jste v tomto okamžiku otevreli.
Mohu bezpecne prenést všechna data z vašeho zarízení na internet, stejne jako na všechny vaše kontakty, posly a sociální síte.
Také mohu komukoli poskytnout prístup k vašim sociálním sítím, e-mailum a poselum.Pokud nechcete, abych:
Prevedte 1300 $ do mé bitcoinové peneženky.Dávám vám 48 hodin na prevod vašich penez. Udelám to jinak.
Hodiny se spustí automaticky, když otevrete e-mail.
Také jsem byl automaticky upozornen, když byl tento e-mail otevren.
Pokud nevíte, jak prevést peníze a co je to bitcoin. Poté na Googlu zadejte „Koupit Bitcoin“.
Adresa mé Bitcoin peneženky: bc1qyg3srjs0gz9l97xdp00vms4sgxa3ymj7aw7vae, bc1qmmj4x3uadjf8ncs8vm85syjzf4vdqag46fjjny, bc1qq3g4zragva9s0ps5hdt78ugj79uecx4p6s8sw5Jakmile obdržím prevod požadované cástky, systém me automaticky informuje o prijaté platbe a požádá me o smazání všech údaju, které jsem od vás obdržel.
Potvrdím tedy odstranení.Neobtežujte se nikde si stežovat, protože peneženka nesleduje poštu, odkud dopis pochází, a není sledována a vytvárena automaticky, takže mi nemá smysl psát.
Pokud se pokusíte tuto zprávu s nekým sdílet, systém automaticky odešle požadavek na servery a on bude pokracovat v prenosu všech dat na sociální síte. Zmena hesel na sociálních sítích, e-mailu a zarízení vám také nepomuže, protože všechna data jsou již stažena do mého serverového clusteru.Hodne štestí a nedelejte nic hloupého.
A Portuguese variant of "I Monitored Your Device On The Net For A Long Time" scam email:
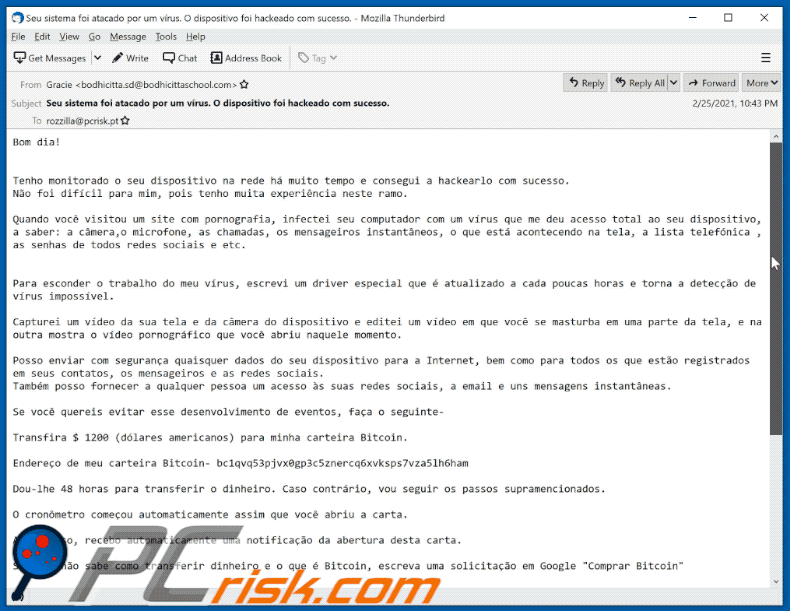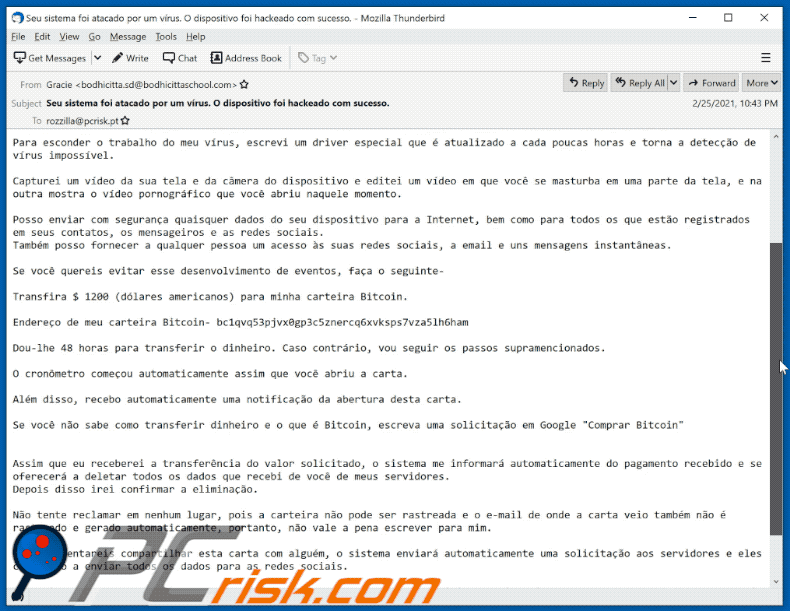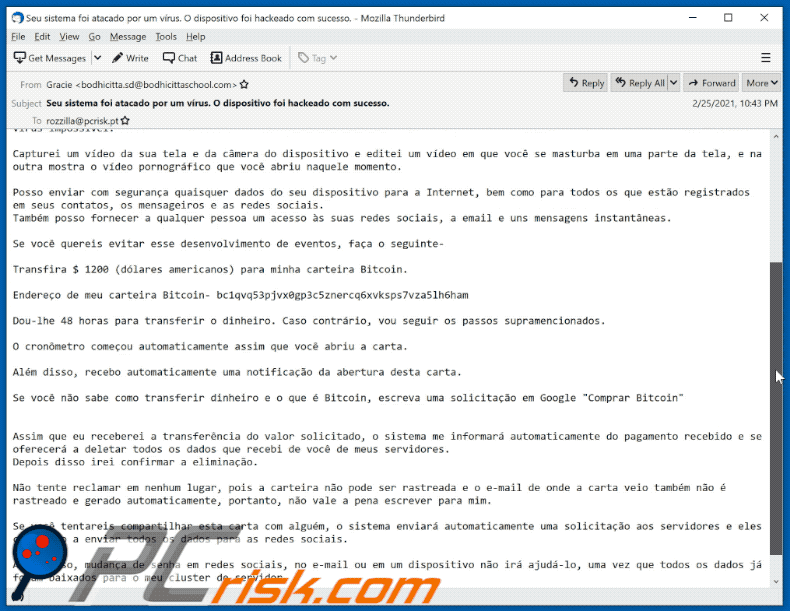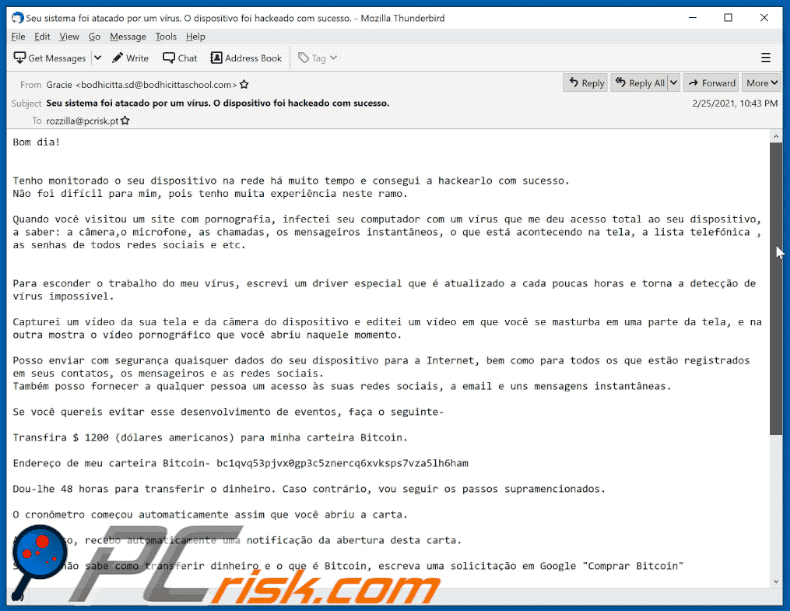
Text presented within:
Subject: Seu sistema foi atacado por um vírus. O dispositivo foi hackeado com sucesso.
Bom dia!
Tenho monitorado o seu dispositivo na rede há muito tempo e consegui a hackearlo com sucesso.
Não foi difícil para mim, pois tenho muita experiência neste ramo.Quando você visitou um site com pornografia, infectei seu computador com um vírus que me deu acesso total ao seu dispositivo,
a saber: a câmera,o microfone, as chamadas, os mensageiros instantâneos, o que está acontecendo na tela, a lista telefónica , as senhas de todos redes sociais e etc.
Para esconder o trabalho do meu vírus, escrevi um driver especial que é atualizado a cada poucas horas e torna a detecção de vírus impossível.Capturei um vídeo da sua tela e da câmera do dispositivo e editei um vídeo em que você se masturba em uma parte da tela, e na outra mostra o vídeo pornográfico que você abriu naquele momento.
Posso enviar com segurança quaisquer dados do seu dispositivo para a Internet, bem como para todos os que estão registrados em seus contatos, os mensageiros e as redes sociais.
Também posso fornecer a qualquer pessoa um acesso às suas redes sociais, a email e uns mensagens instantâneas.Se você quereis evitar esse desenvolvimento de eventos, faça o seguinte-
Transfira $ 1200 (dólares americanos) para minha carteira Bitcoin.
Endereço de meu carteira Bitcoin- bc1qvq53pjvx0gp3c5znercq6xvksps7vza5lh6ham
Dou-lhe 48 horas para transferir o dinheiro. Caso contrário, vou seguir os passos supramencionados.
O cronômetro começou automaticamente assim que você abriu a carta.
Além disso, recebo automaticamente uma notificação da abertura desta carta.
Se você não sabe como transferir dinheiro e o que é Bitcoin, escreva uma solicitação em Google "Comprar Bitcoin"
Assim que eu receberei a transferência do valor solicitado, o sistema me informará automaticamente do pagamento recebido e se oferecerá a deletar todos os dados que recebi de você de meus servidores.
Depois disso irei confirmar a eliminação.Não tente reclamar em nenhum lugar, pois a carteira não pode ser rastreada e o e-mail de onde a carta veio também não é rastreado e gerado automaticamente, portanto, não vale a pena escrever para mim.
Se você tentareis compartilhar esta carta com alguém, o sistema enviará automaticamente uma solicitação aos servidores e eles começarão a enviar todos os dados para as redes sociais.
Além disso, mudança de senha em redes sociais, no e-mail ou em um dispositivo não irá ajudá-lo, uma vez que todos os dados já foram baixados para o meu cluster de servidor.
Boa sorte e não faça coisas estúpidas.
An Italian variant of "I Monitored Your Device On The Net For A Long Time" scam email:
Text presented within:
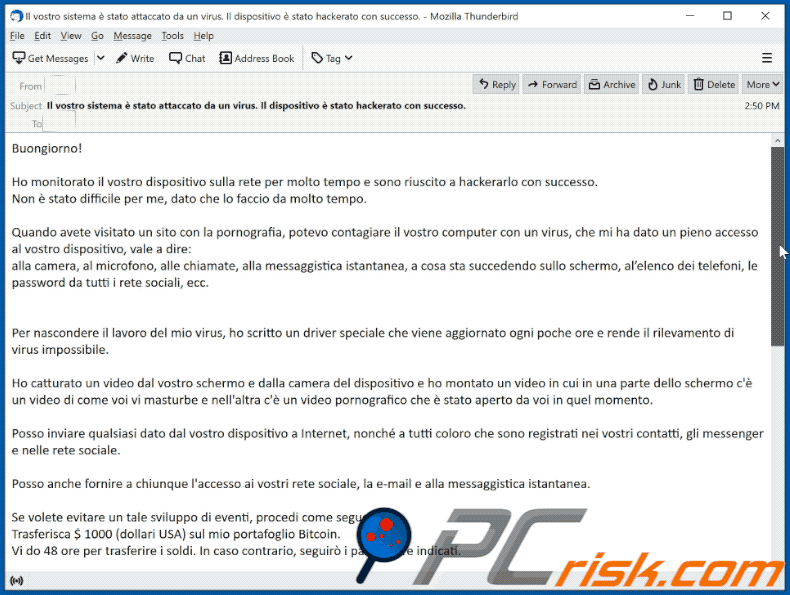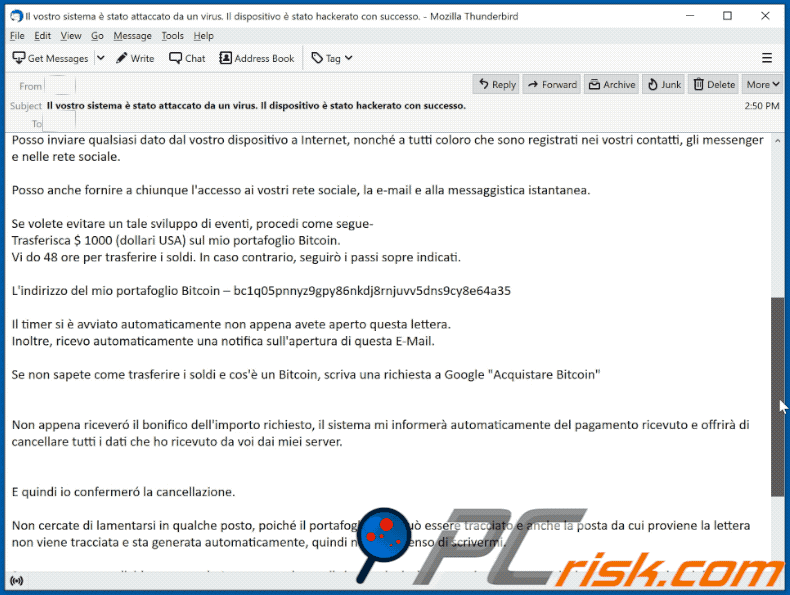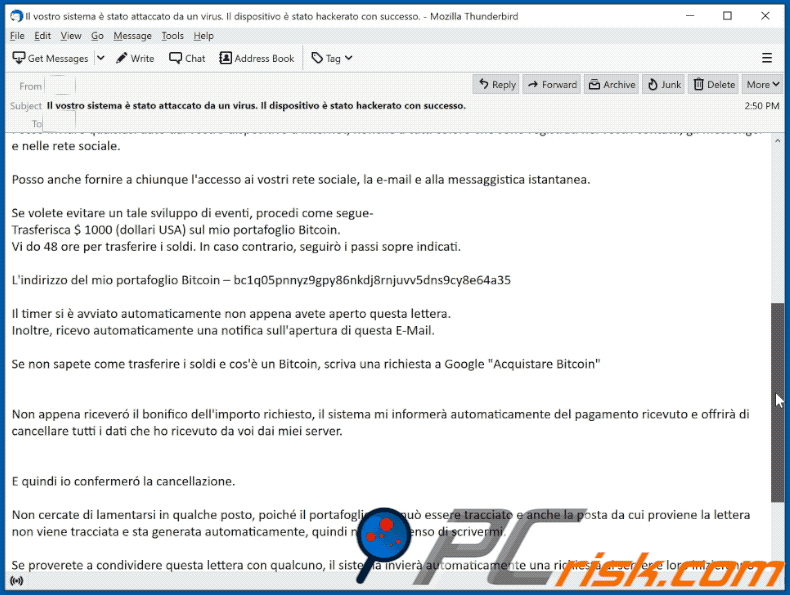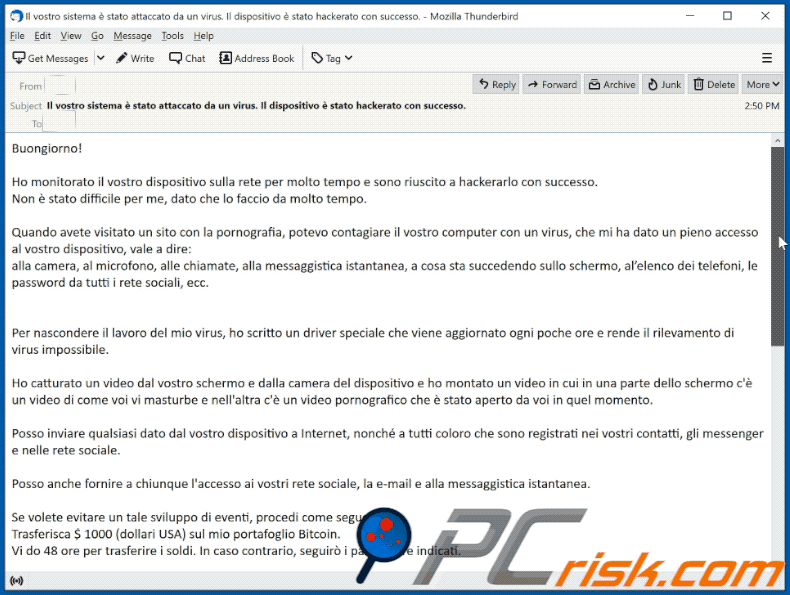
Subject: Il vostro sistema è stato attaccato da un virus. Il dispositivo è stato hackerato con successo.
Buongiorno!
Ho monitorato il vostro dispositivo sulla rete per molto tempo e sono riuscito a hackerarlo con successo.
Non è stato difficile per me, dato che lo faccio da molto tempo.
Quando avete visitato un sito con la pornografia, potevo contagiare il vostro computer con un virus, che mi ha dato un pieno accesso al vostro dispositivo, vale a dire:
alla camera, al microfono, alle chiamate, alla messaggistica istantanea, a cosa sta succedendo sullo schermo, al’elenco dei telefoni, le password da tutti i rete sociali, ecc.
Per nascondere il lavoro del mio virus, ho scritto un driver speciale che viene aggiornato ogni poche ore e rende il rilevamento di virus impossibile.
Ho catturato un video dal vostro schermo e dalla camera del dispositivo e ho montato un video in cui in una parte dello schermo c'è un video di come voi vi masturbe e nell'altra c'è un video pornografico che è stato aperto da voi in quel momento.
Posso inviare qualsiasi dato dal vostro dispositivo a Internet, nonché a tutti coloro che sono registrati nei vostri contatti, gli messenger e nelle rete sociale.
Posso anche fornire a chiunque l'accesso ai vostri rete sociale, la e-mail e alla messaggistica istantanea.
Se volete evitare un tale sviluppo di eventi, procedi come segue-
Trasferisca $ 1000 (dollari USA) sul mio portafoglio Bitcoin.
Vi do 48 ore per trasferire i soldi. In caso contrario, seguirò i passi sopre indicati.
L'indirizzo del mio portafoglio Bitcoin – bc1q05pnnyz9gpy86nkdj8rnjuvv5dns9cy8e64a35
Il timer si è avviato automaticamente non appena avete aperto questa lettera.
Inoltre, ricevo automaticamente una notifica sull'apertura di questa E-Mail.
Se non sapete come trasferire i soldi e cos'è un Bitcoin, scriva una richiesta a Google "Acquistare Bitcoin"
Non appena riceveró il bonifico dell'importo richiesto, il sistema mi informerà automaticamente del pagamento ricevuto e offrirà di cancellare tutti i dati che ho ricevuto da voi dai miei server.
E quindi io confermeró la cancellazione.
Non cercate di lamentarsi in qualche posto, poiché il portafoglio non può essere tracciato e anche la posta da cui proviene la lettera non viene tracciata e sta generata automaticamente, quindi non ha il senso di scrivermi.
Se proverete a condividere questa lettera con qualcuno, il sistema invierà automaticamente una richiesta ai server e loro inizieranno a caricare tutti i dati sui rete sociali.
Altresi, il cambio delle password di rete sociali, di posta o del dispositivo non vi aiuterà, poiché tutti i dati sono già stati scaricati nel cluster dei miei server.
Vi auguro buona fortuna e non fate sciocchezze.
A French variant of "I Monitored Your Device On The Net For A Long Time" scam email:
Text presented within:
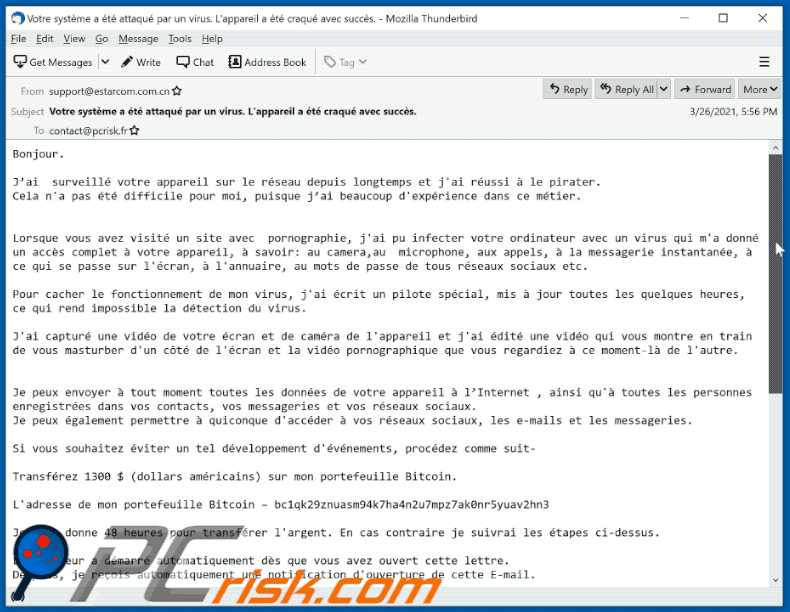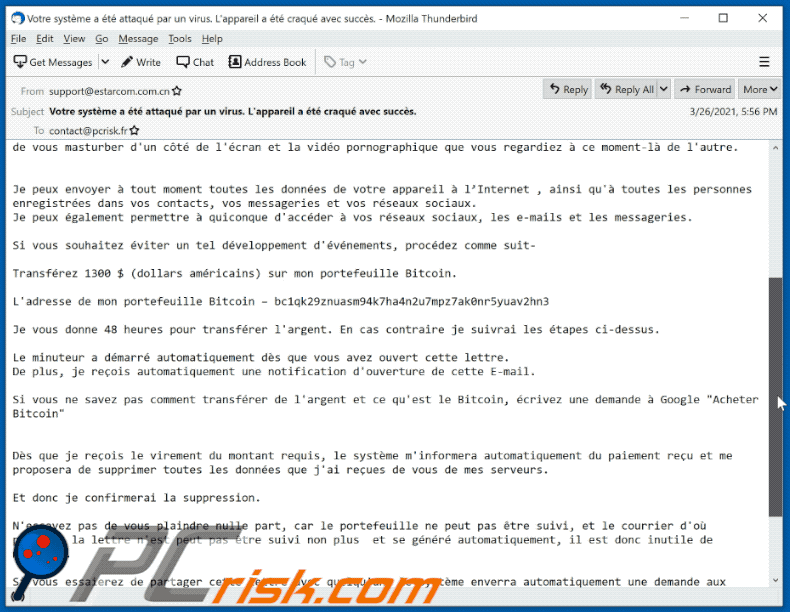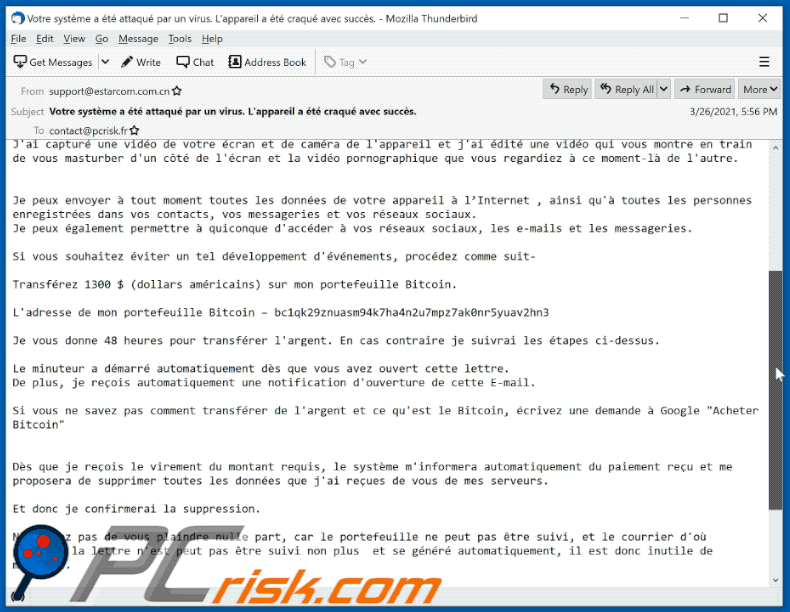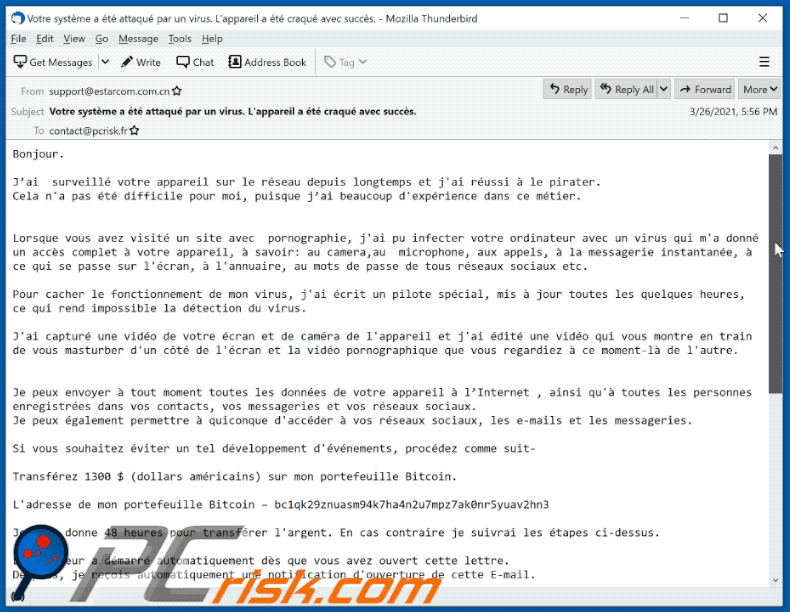
Subject: Votre système a été attaqué par un virus. L'appareil a été craqué avec succès.
Bonjour.
J’ai surveillé votre appareil sur le réseau depuis longtemps et j'ai réussi à le pirater.
Cela n'a pas été difficile pour moi, puisque j’ai beaucoup d'expérience dans ce métier.
Lorsque vous avez visité un site avec pornographie, j'ai pu infecter votre ordinateur avec un virus qui m'a donné un accès complet à votre appareil, à savoir: au camera,au microphone, aux appels, à la messagerie instantanée, à ce qui se passe sur l'écran, à l'annuaire, au mots de passe de tous réseaux sociaux etc.Pour cacher le fonctionnement de mon virus, j'ai écrit un pilote spécial, mis à jour toutes les quelques heures, ce qui rend impossible la détection du virus.
J'ai capturé une vidéo de votre écran et de caméra de l'appareil et j'ai édité une vidéo qui vous montre en train de vous masturber d'un côté de l'écran et la vidéo pornographique que vous regardiez à ce moment-là de l'autre.
Je peux envoyer à tout moment toutes les données de votre appareil à l’Internet , ainsi qu'à toutes les personnes enregistrées dans vos contacts, vos messageries et vos réseaux sociaux.
Je peux également permettre à quiconque d'accéder à vos réseaux sociaux, les e-mails et les messageries.Si vous souhaitez éviter un tel développement d'événements, procédez comme suit-
Transférez 1300 $ (dollars américains) sur mon portefeuille Bitcoin.
L'adresse de mon portefeuille Bitcoin – bc1qk29znuasm94k7ha4n2u7mpz7ak0nr5yuav2hn3
Je vous donne 48 heures pour transférer l'argent. En cas contraire je suivrai les étapes ci-dessus.
Le minuteur a démarré automatiquement dès que vous avez ouvert cette lettre.
De plus, je reçois automatiquement une notification d'ouverture de cette E-mail.Si vous ne savez pas comment transférer de l'argent et ce qu'est le Bitcoin, écrivez une demande à Google "Acheter Bitcoin"
Dès que je reçois le virement du montant requis, le système m'informera automatiquement du paiement reçu et me proposera de supprimer toutes les données que j'ai reçues de vous de mes serveurs.Et donc je confirmerai la suppression.
N'essayez pas de vous plaindre nulle part, car le portefeuille ne peut pas être suivi, et le courrier d'où provient la lettre n'est peut pas être suivi non plus et se généré automatiquement, il est donc inutile de m'écrire.
Si vous essaierez de partager cette lettre avec quelqu'un, le système enverra automatiquement une demande aux serveurs et ils commenceront à télécharger toutes les données sur les réseaux sociaux.
Par ailleurs, le changement des mots de passe sur les réseaux sociaux, sur la messagerie ou sur votre appareil ne vous aidera pas, puisque toutes les données ont déjà été téléchargées sur le cluster de mes serveurs.
Bonne chance et non faites pas des bêtises.
A Russian variant of "I Monitored Your Device On The Net For A Long Time" scam email:
Text presented within:
Subject: Запрос на оплату.
Хорошего вам времени суток!
Для вас от меня полохие новости.
Два-три месяца назад я получил доступ ко всем вашим устройствам, с помощью которых вы выходите в интернет.
Сразу же после этого, я начал следить за вашей сетевой активностью.Вы хотите узнать как это было? Запросто!
Итак:
Несколько месяцев назад я купил доступ к большой базе email адресов на черном рынке, это не сложно...
Когда я сделал сверку логинпароль, то получил доступ к нескольким тысяч почтовых аккаунтов, в том числе и вашему (********).Вы заходите на ******** довольно регулярно, и мне не составило труда установить свой троянец на все ваши устройства, с которых вы это делали..
Я вам присылал в некоторых регулярных письмах ссылки, а вы незадумываясь нажимали на них, переходя на ресурс с експлойтом.
Вы своими руками установили себе вредоносное ПО...
Как видите, быть хорошим хакером нетрудно!Моя программа-шпион дает мне доступ к микрофону, веб-камере или клавиатуре вашего устройства...
Я могу контролировать ваш экран, записывать звук или видео, вводить за вас сообщения!
После этого я закачал на свои удаленные сервера все ваши мультимедиа файлы (фото и видео), все ваши чаты и истории просмотра страниц браузеров.
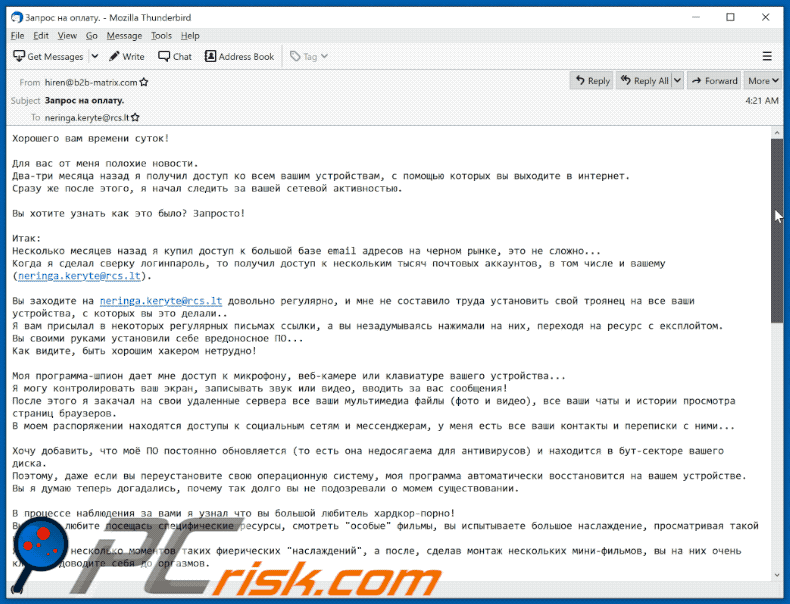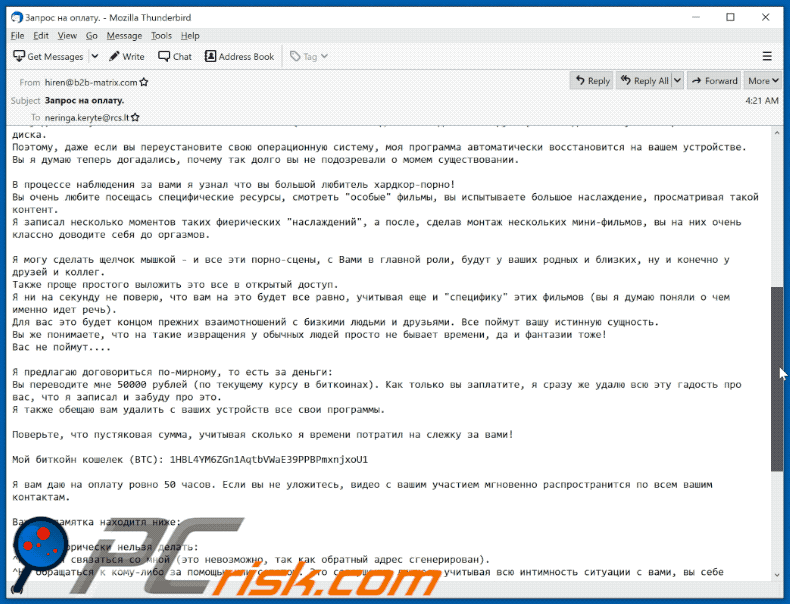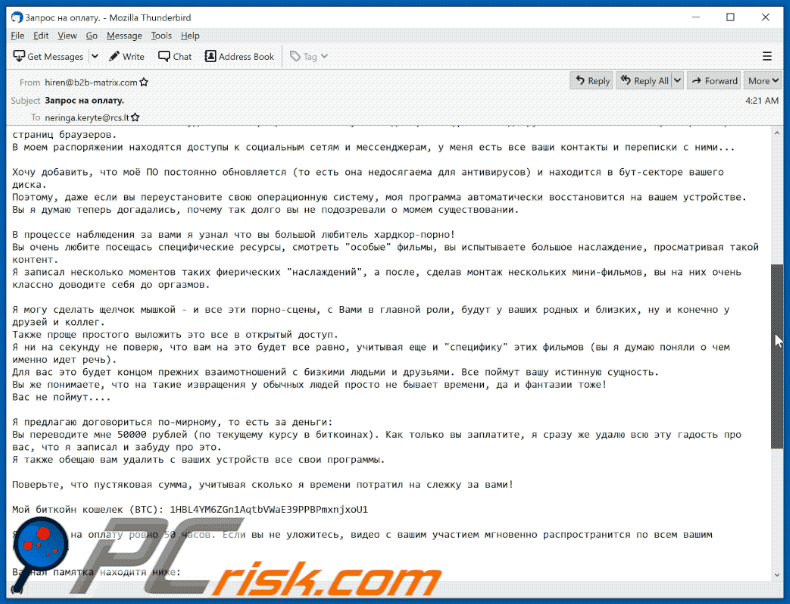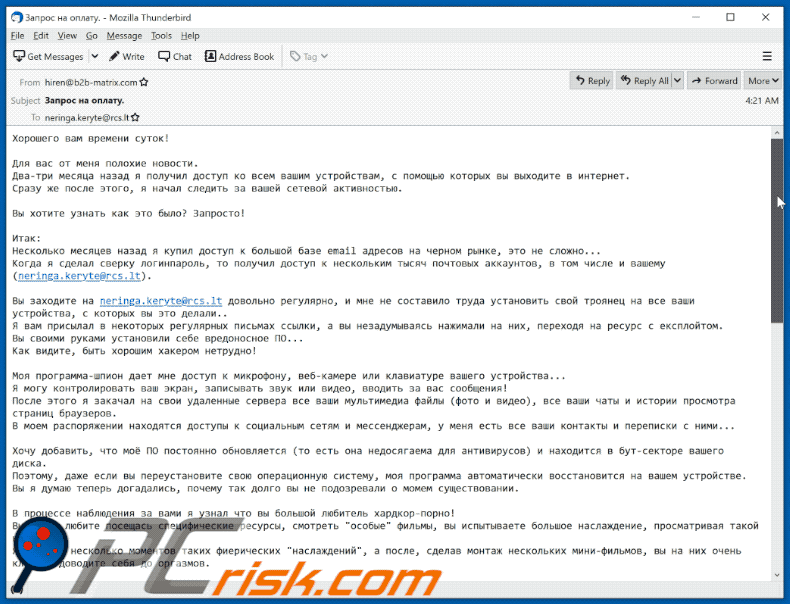
В моем распоряжении находятся доступы к социальным сетям и мессенджерам, у меня есть все ваши контакты и переписки с ними...Хочу добавить, что моё ПО постоянно обновляется (то есть она недосягаема для антивирусов) и находится в бут-секторе вашего диска.
Поэтому, даже если вы переустановите свою операционную систему, моя программа автоматически восстановится на вашем устройстве.
Вы я думаю теперь догадались, почему так долго вы не подозревали о момем существовании.В процессе наблюдения за вами я узнал что вы большой любитель хардкор-порно!
Вы очень любите посещась специфические ресурсы, смотреть "особые" фильмы, вы испытываете большое наслаждение, просматривая такой контент.
Я записал несколько моментов таких фиерических "наслаждений", а после, сделав монтаж нескольких мини-фильмов, вы на них очень классно доводите себя до оргазмов.Я могу сделать щелчок мышкой - и все эти порно-сцены, с Вами в главной роли, будут у ваших родных и близких, ну и конечно у друзей и коллег.
Также проще простого выложить это все в открытый доступ.
Я ни на секунду не поверю, что вам на это будет все равно, учитывая еще и "специфику" этих фильмов (вы я думаю поняли о чем именно идет речь).
Для вас это будет концом прежних взаимотношений с бизкими людьми и друзьями. Все поймут вашу истинную сущность.
Вы же понимаете, что на такие извращения у обычных людей просто не бывает времени, да и фантазии тоже!
Вас не поймут....Я предлагаю договориться по-мирному, то есть за деньги:
Вы переводите мне 50000 рублей (по текущему курсу в биткоинах). Как только вы заплатите, я сразу же удалю всю эту гадость про вас, что я записал и забуду про это.
Я также обещаю вам удалить с ваших устройств все свои программы.Поверьте, что пустяковая сумма, учитывая сколько я времени потратил на слежку за вами!
Мой биткойн кошелек (BTC): 1HBL4YM6ZGn1AqtbVWaE39PPBPmxnjxoU1
Я вам даю на оплату ровно 50 часов. Если вы не уложитесь, видео с вашим участием мгновенно распространится по всем вашим контактам.
Важная памятка находитя ниже:
Что категорически нельзя делать:
^Пытаться связаться со мной (это невозможно, так как обратный адрес сгенерирован).
^Не обращаться к кому-либо за помощью или советом. Это совершенно лишнее, учитывая всю интимность ситуации с вами, вы себе просто навредите.
^Не выкидывайте и не ломайте свое устройство или компьютер! Напоминаю, что все файлы с видео находятся УЖЕ у меня.НЕ переживайте о слудующем:
^Что я не увижу вашу транзакцию.
- Даже не задумывайтесь про это. Я полностью вижу что происходит у вас на экране, а вся история ваших действий записывается.
^Что я разошлю видео с вашим участием, даже если вы сделаете мне транзакцию в 50000 рублей.
- Во-первых, Если бы я хотел это сделать я бы уже сделал, во-вторых - зачем? я даже вас не знаю, зачем мне делать вам плохо, при том что свою часть сделки вы выполнили...Не сосмневайтесь в том, что все будет честно!
Я советую на данный момент проявить благоразумие, так как честь дороже.
А на будущее - используйте более безопасный софт для работы с почтой!И не тяните с оплатой, я ждать не буду!
A Spanish variant of "I Monitored Your Device On The Net For A Long Time" scam email:
Text presented within:
Subject: Confirmación de transferencia de dinero
¡Saludos!
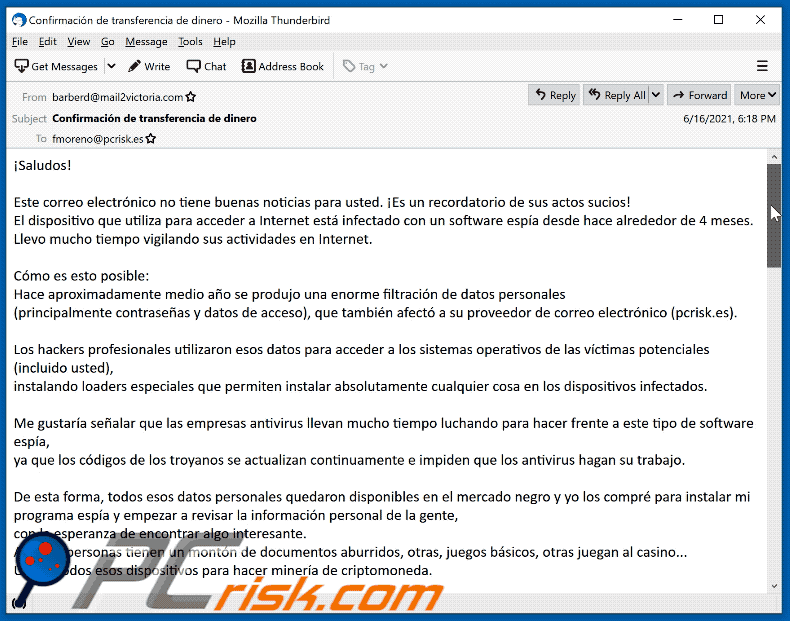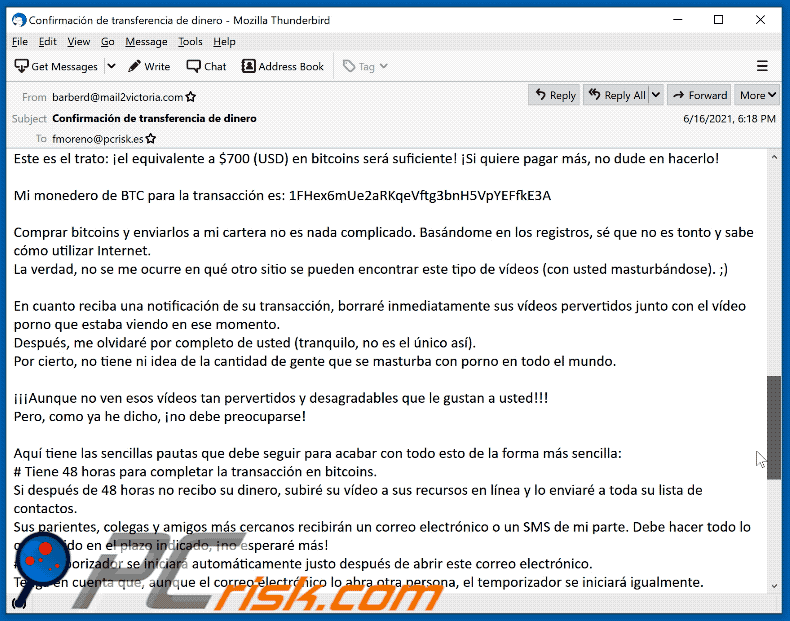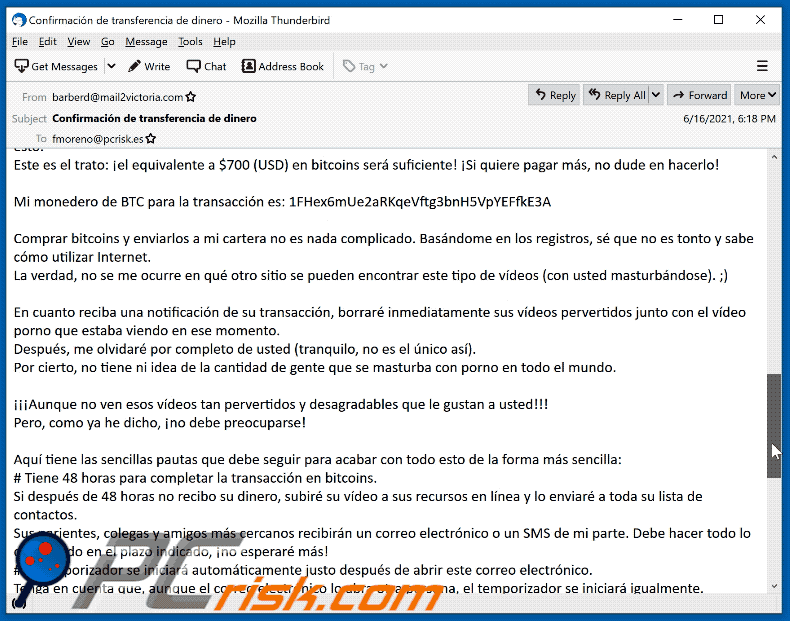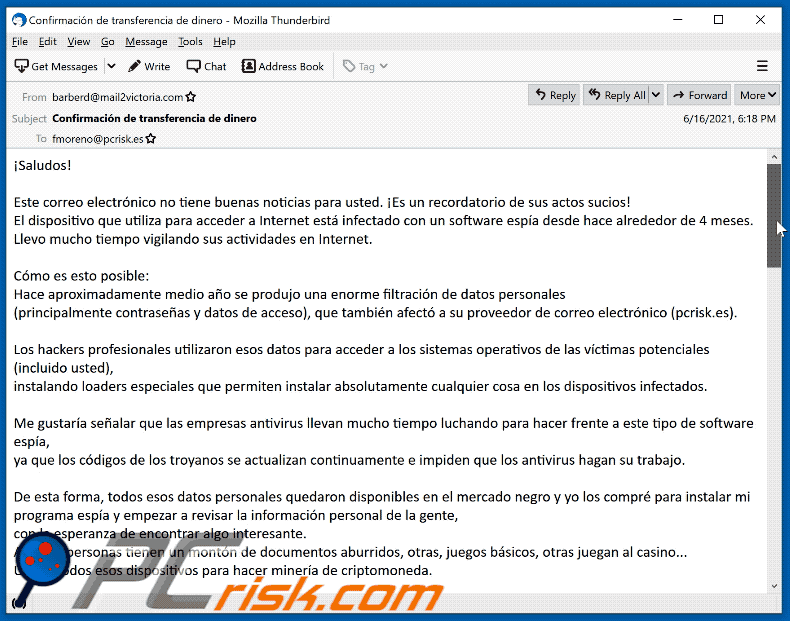
Este correo electrónico no tiene buenas noticias para usted. ¡Es un recordatorio de sus actos sucios!
El dispositivo que utiliza para acceder a Internet está infectado con un software espía desde hace alrededor de 4 meses.
Llevo mucho tiempo vigilando sus actividades en Internet.Cómo es esto posible:
Hace aproximadamente medio año se produjo una enorme filtración de datos personales
(principalmente contraseñas y datos de acceso), que también afectó a su proveedor de correo electrónico (pcrisk.es).Los hackers profesionales utilizaron esos datos para acceder a los sistemas operativos de las víctimas potenciales (incluido usted),
instalando loaders especiales que permiten instalar absolutamente cualquier cosa en los dispositivos infectados.Me gustaría señalar que las empresas antivirus llevan mucho tiempo luchando para hacer frente a este tipo de software espía,
ya que los códigos de los troyanos se actualizan continuamente e impiden que los antivirus hagan su trabajo.De esta forma, todos esos datos personales quedaron disponibles en el mercado negro y yo los compré para instalar mi programa espía y empezar a revisar la información personal de la gente,
con la esperanza de encontrar algo interesante.
Algunas personas tienen un montón de documentos aburridos, otras, juegos básicos, otras juegan al casino...
Utilicé todos esos dispositivos para hacer minería de criptomoneda.Sin embargo, al final me topé con algo realmente especial al comprobar sus datos personales
Parece que le gusta mucho ver vídeos pervertidos (es fácil confirmarlo comprobando el registro de actividad de sus reproductores multimedia y el historial del navegador).
Llevo tiempo filtrando los vídeos más impactantes con los que se masturba, y grabándolo a través de la cámara y el micrófono de su dispositivo.Como resultado, he generado algunos vídeos cortos donde sale dándose placer (de maneras realmente impresionantes a veces),
y en la parte inferior de la pantalla aparece el vídeo que estaba viendo en ese momento.
He conseguido crear una colección realmente buena en los últimos meses¿Qué cree que pasaría si compartiera esos vídeos con sus colegas, familiares y amigos?
Teniendo en cuenta la "peculiaridad" de los vídeos que suele ver, la opinión que tienen de usted cambiaría para siempre.
Supongo que incluso podría tener problemas con la ley debido a ciertos vídeos de esa colección...Pero no me interesa en absoluto meterle en ese tipo de problemas.
Solo quiero que me dé algo de dinero, ya que he invertido una importante cantidad de tiempo y esfuerzo en hacer todo esto.
Este es el trato: ¡el equivalente a $700 (USD) en bitcoins será suficiente! ¡Si quiere pagar más, no dude en hacerlo!Mi monedero de BTC para la transacción es: 1FHex6mUe2aRKqeVftg3bnH5VpYEFfkE3A
Comprar bitcoins y enviarlos a mi cartera no es nada complicado. Basándome en los registros, sé que no es tonto y sabe cómo utilizar Internet.
La verdad, no se me ocurre en qué otro sitio se pueden encontrar este tipo de vídeos (con usted masturbándose). ;)En cuanto reciba una notificación de su transacción, borraré inmediatamente sus vídeos pervertidos junto con el vídeo porno que estaba viendo en ese momento.
Después, me olvidaré por completo de usted (tranquilo, no es el único así).
Por cierto, no tiene ni idea de la cantidad de gente que se masturba con porno en todo el mundo.¡¡¡Aunque no ven esos vídeos tan pervertidos y desagradables que le gustan a usted!!!
Pero, como ya he dicho, ¡no debe preocuparse!Aquí tiene las sencillas pautas que debe seguir para acabar con todo esto de la forma más sencilla:
# Tiene 48 horas para completar la transacción en bitcoins.
Si después de 48 horas no recibo su dinero, subiré su vídeo a sus recursos en línea y lo enviaré a toda su lista de contactos.
Sus parientes, colegas y amigos más cercanos recibirán un correo electrónico o un SMS de mi parte. Debe hacer todo lo que le pido en el plazo indicado, ¡no esperaré más!
# El temporizador se iniciará automáticamente justo después de abrir este correo electrónico.
Tenga en cuenta que, aunque el correo electrónico lo abra otra persona, el temporizador se iniciará igualmente.
# No tiene sentido responder a este correo. He generado la dirección del remitente (simplemente he utilizado una dirección aleatoria de Internet).
Lo único que debe hacer es pagar.
# Intentar localizarme es una mala idea, ya que utilizo nodos y un sistema blockchain para realizar las transacciones de bitcoin.
# Reinstalar el Sistema Operativo tampoco le servirá de nada. Aunque queme su dispositivo, no se solucionará el problema.
Todos los archivos ya han sido encriptados y guardados en sitios web de alojamiento de archivos remotos.
# Una vez que la transacción se haya completado, no hace falta que me lo notifique. Podré verlo por mí mismo, ya que vigilo toda su actividad en Internet.Por favor, tenga en cuenta lo más importante:
Una vez que complete la transacción, eliminaré mi virus troyano de su dispositivo, así como todos los vídeos humillantes, de los recursos remotos en línea.
Después, podrá olvidarse de mí y de esta desagradable situación. ¡Esa es la mejor solución para este problema!Un último consejo: ¡cambie todos los datos de acceso a todos sus servicios de Internet, ya que puede que no sea el único que tenga acceso a sus cuentas!
Sea sensato. ¡Buena suerte!
Another example of "I Monitored Your Device On The Net For A Long Time" scam email:
Text presented within:
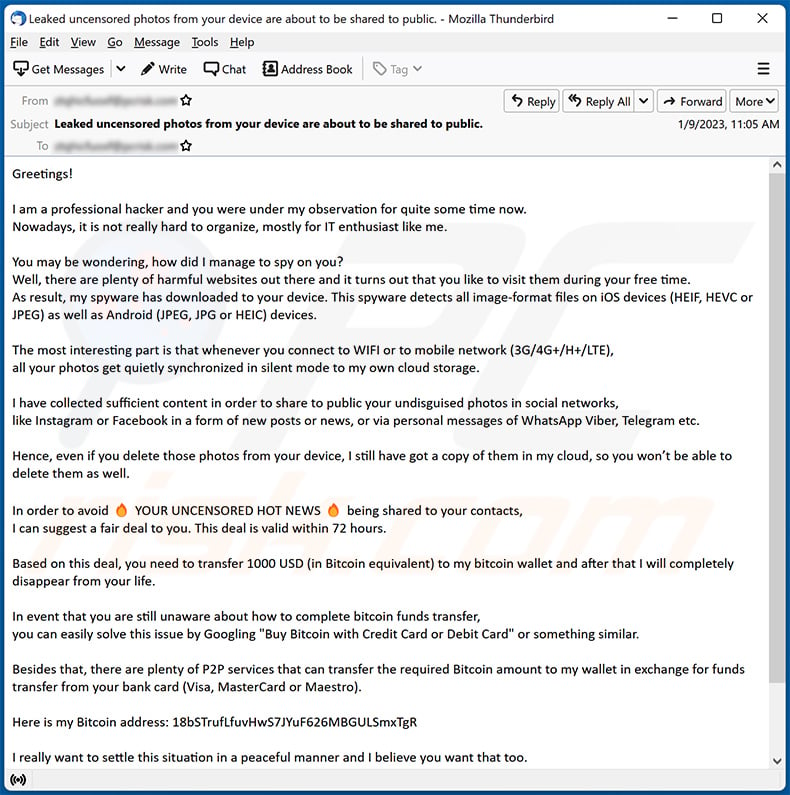
Subject: Leaked uncensored photos from your device are about to be shared to public.
Greetings!
I am a professional hacker and you were under my observation for quite some time now.
Nowadays, it is not really hard to organize, mostly for IT enthusiast like me.You may be wondering, how did I manage to spy on you?
Well, there are plenty of harmful websites out there and it turns out that you like to visit them during your free time.
As result, my spyware has downloaded to your device. This spyware detects all image-format files on iOS devices (HEIF, HEVC or JPEG) as well as Android (JPEG, JPG or HEIC) devices.The most interesting part is that whenever you connect to WIFI or to mobile network (3G/4G+/H+/LTE),
all your photos get quietly synchronized in silent mode to my own cloud storage.I have collected sufficient content in order to share to public your undisguised photos in social networks,
like Instagram or Facebook in a form of new posts or news, or via personal messages of WhatsApp Viber, Telegram etc.Hence, even if you delete those photos from your device, I still have got a copy of them in my cloud, so you won’t be able to delete them as well.
In order to avoid YOUR UNCENSORED HOT NEWS being shared to your contacts,
I can suggest a fair deal to you. This deal is valid within 72 hours.Based on this deal, you need to transfer 1000 USD (in Bitcoin equivalent) to my bitcoin wallet and after that I will completely disappear from your life.
In event that you are still unaware about how to complete bitcoin funds transfer,
you can easily solve this issue by Googling "Buy Bitcoin with Credit Card or Debit Card" or something similar.Besides that, there are plenty of P2P services that can transfer the required Bitcoin amount to my wallet in exchange for funds transfer from your bank card (Visa, MasterCard or Maestro).
Here is my Bitcoin address: 18bSTrufLfuvHwS7JYuF626MBGULSmxTgR
I really want to settle this situation in a peaceful manner and I believe you want that too.
Nothing personal, it is simply my job.
Make sure you use valid Antivirus software and stay away from unwanted websites.
Take care of yourself.
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is I Monitored Your Device On The Net For A Long Time spam?
- Types of malicious emails.
- How to spot a malicious email?
- What to do if you fell for an email scam?
Types of malicious emails:
![]() Phishing Emails
Phishing Emails
Most commonly, cybercriminals use deceptive emails to trick Internet users into giving away their sensitive private information, for example, login information for various online services, email accounts, or online banking information.
Such attacks are called phishing. In a phishing attack, cybercriminals usually send an email message with some popular service logo (for example, Microsoft, DHL, Amazon, Netflix), create urgency (wrong shipping address, expired password, etc.), and place a link which they hope their potential victims will click on.
After clicking the link presented in such email message, victims are redirected to a fake website that looks identical or extremely similar to the original one. Victims are then asked to enter their password, credit card details, or some other information that gets stolen by cybercriminals.
![]() Emails with Malicious Attachments
Emails with Malicious Attachments
Another popular attack vector is email spam with malicious attachments that infect users' computers with malware. Malicious attachments usually carry trojans that are capable of stealing passwords, banking information, and other sensitive information.
In such attacks, cybercriminals' main goal is to trick their potential victims into opening an infected email attachment. To achieve this goal, email messages usually talk about recently received invoices, faxes, or voice messages.
If a potential victim falls for the lure and opens the attachment, their computers get infected, and cybercriminals can collect a lot of sensitive information.
While it's a more complicated method to steal personal information (spam filters and antivirus programs usually detect such attempts), if successful, cybercriminals can get a much wider array of data and can collect information for a long period of time.
![]() Sextortion Emails
Sextortion Emails
This is a type of phishing. In this case, users receive an email claiming that a cybercriminal could access the webcam of the potential victim and has a video recording of one's masturbation.
To get rid of the video, victims are asked to pay a ransom (usually using Bitcoin or another cryptocurrency). Nevertheless, all of these claims are false - users who receive such emails should ignore and delete them.
How to spot a malicious email?
While cyber criminals try to make their lure emails look trustworthy, here are some things that you should look for when trying to spot a phishing email:
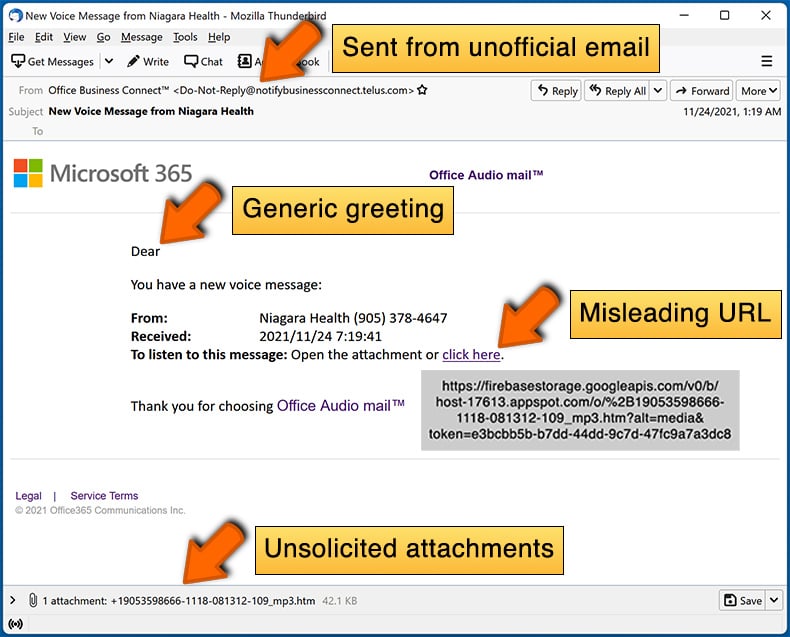
- Check the sender's ("from") email address: Hover your mouse over the "from" address and check if it's legitimate. For example, if you received an email from Microsoft, be sure to check if the email address is @microsoft.com and not something suspicious like @m1crosoft.com, @microsfot.com, @account-security-noreply.com, etc.
- Check for generic greetings: If the greeting in the email is "Dear user", "Dear @youremail.com", "Dear valued customer", this should raise suspiciousness. Most commonly, companies call you by your name. Lack of this information could signal a phishing attempt.
- Check the links in the email: Hover your mouse over the link presented in the email, if the link that appears seems suspicious, don't click it. For example, if you received an email from Microsoft and the link in the email shows that it will go to firebasestorage.googleapis.com/v0... you shouldn't trust it. It's best not to click any links in the emails but to visit the company website that sent you the email in the first place.
- Don't blindly trust email attachments: Most commonly, legitimate companies will ask you to log in to their website and to view any documents there; if you received an email with an attachment, it's a good idea to scan it with an antivirus application. Infected email attachments are a common attack vector used by cybercriminals.
To minimise the risk of opening phishing and malicious emails we recommend using Combo Cleaner Antivirus for Windows.
Example of a spam email:
What to do if you fell for an email scam?
- If you clicked on a link in a phishing email and entered your password - be sure to change your password as soon as possible. Usually, cybercriminals collect stolen credentials and then sell them to other groups that use them for malicious purposes. If you change your password in a timely manner, there's a chance that criminals won't have enough time to do any damage.
- If you entered your credit card information - contact your bank as soon as possible and explain the situation. There's a good chance that you will need to cancel your compromised credit card and get a new one.
- If you see any signs of identity theft - you should immediately contact the Federal Trade Commission. This institution will collect information about your situation and create a personal recovery plan.
- If you opened a malicious attachment - your computer is probably infected, you should scan it with a reputable antivirus application. For this purpose, we recommend using Combo Cleaner Antivirus for Windows.
- Help other Internet users - report phishing emails to Anti-Phishing Working Group, FBI’s Internet Crime Complaint Center, National Fraud Information Center and U.S. Department of Justice.
Frequently Asked Questions (FAQ)
Why did I receive this email?
This email is non-targeted. It means that all recipients received the same letter. Scammers behind emails of this type do not target anyone in particular.
I have provided my personal information when tricked by this email, what should I do?
If you have provided login information (e.g., usernames and passwords), change all passwords as soon as possible. If you have provided other information like credit card details, ID card information, social security numbers, etc., contact the corresponding authorities.
Was my computer actually hacked and does the sender have any information?
Scammers behind such emails often use various scare tactics (e.g., they provide old passwords) to trick recipients into believing that their computers are infected. However, computers are never actually hacked or infected.
I have sent cryptocurrency to the address presented in such email, can I get my money back?
Crypto transactions are irreversible. Thus, if you have sent cryptocurrency to scammers, you will not be able to retrieve it.
Will Combo Cleaner remove malware infections that were present in email attachment?
Yes, Combo Cleaner can detect almost all known malware infections. Computers infected with high-end malware must be scanned using a full scan. Typically, malware of this kind hides deep in the system.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion