Zybvqxefmh Ransomware
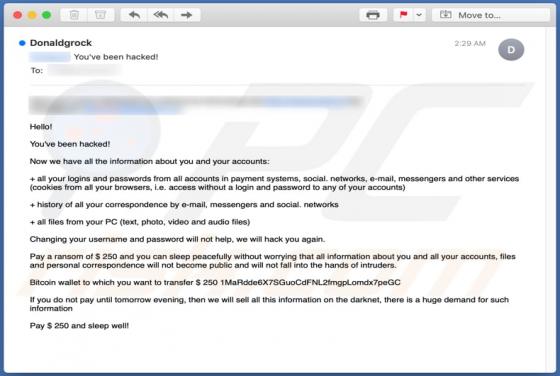
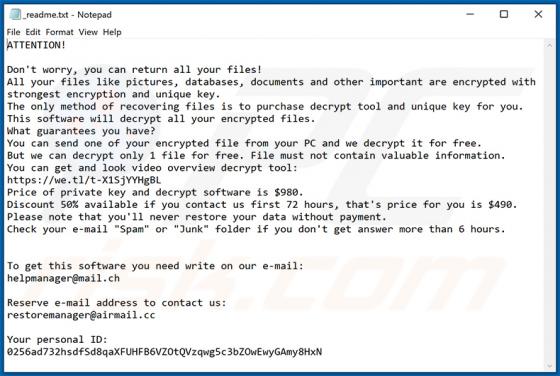
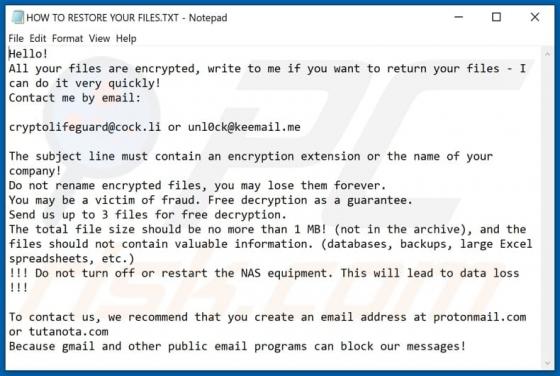
Discovered by S!Ri, Zybvqxefmh ransomware encrypts victims' files and renames them by appending its extension. It also creates the "HOW TO RESTORE YOUR FILES.TXT" text file in folders that contain encrypted files. Zybvqxefmh appends the ".zybvqxefmh" extension to filenames. For example, "1.jpg" i