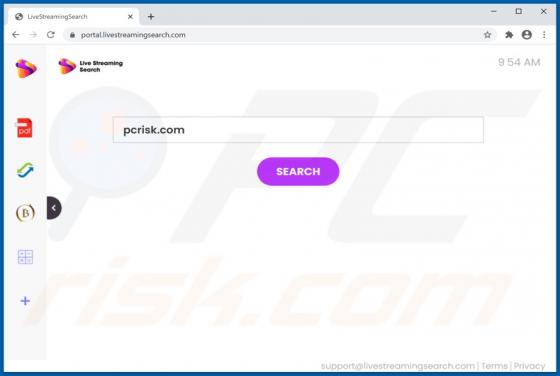
LiveStreamingSearch Browser Hijacker
LiveStreamingSearch is rogue software categorized as a browser hijacker. Following successful installation, it makes alterations to browser settings to promote livestreamingsearch.com (a fake search engine). Additionally, this browser hijacker has data tracking capabilities, which are employed to