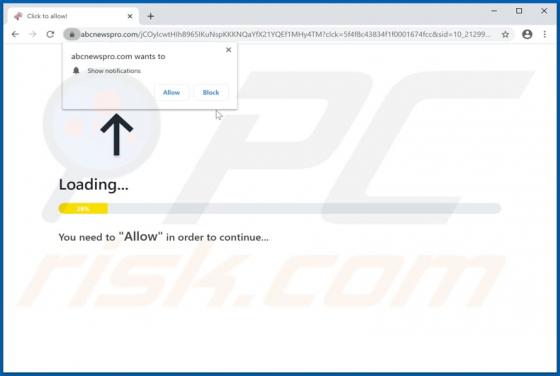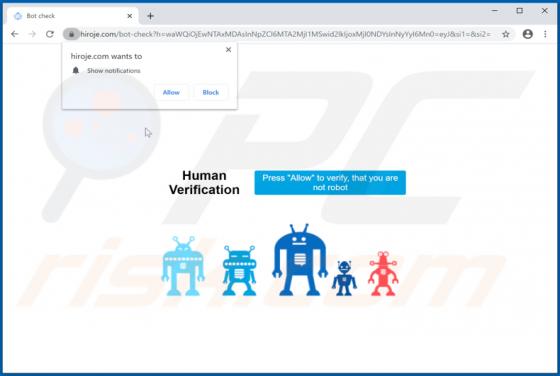
Hiroje.com Ads
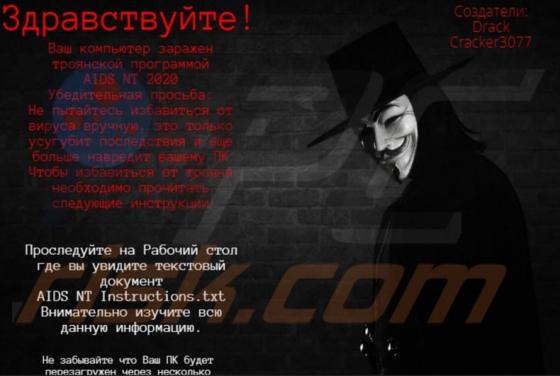
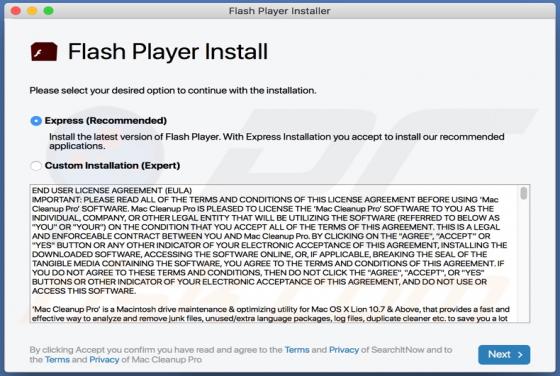
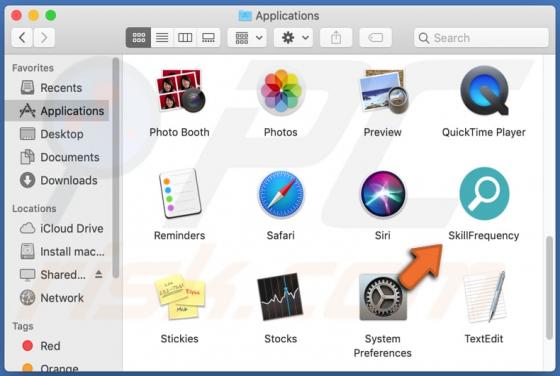
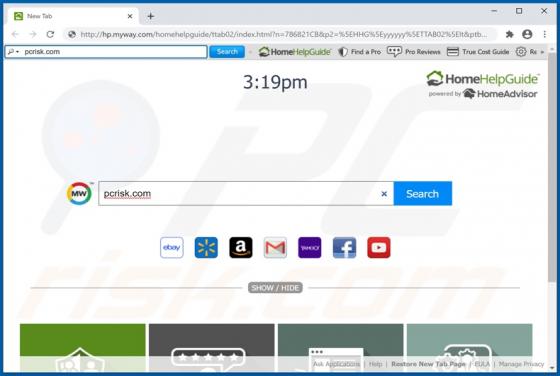
hiroje[.]com is a rogue web page designed to load dubious content or open other bogus websites. This is not the only website that functions in this way - more examples are abcnewspro[.]com, sferverification[.]com and alondondon[.]xyz. These pages are usually opened by installed potentially unwant