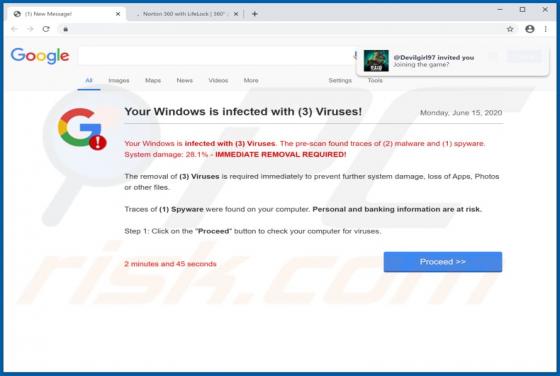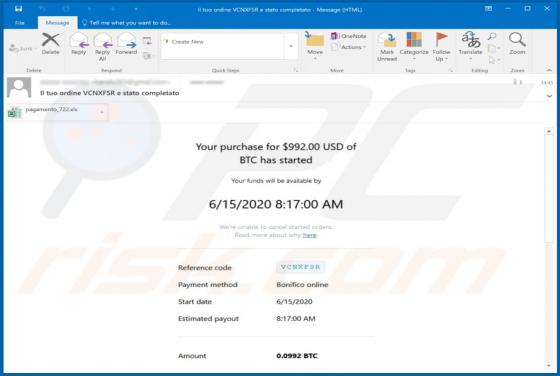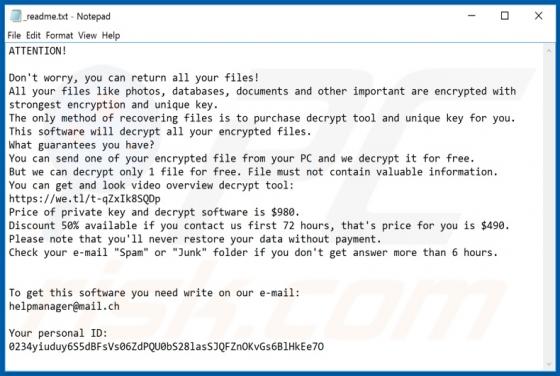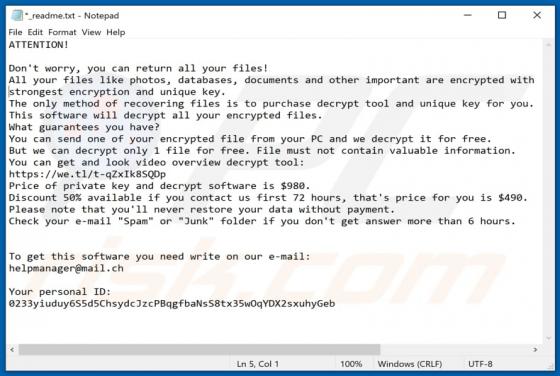
Gdjlosvtnib Ransomware
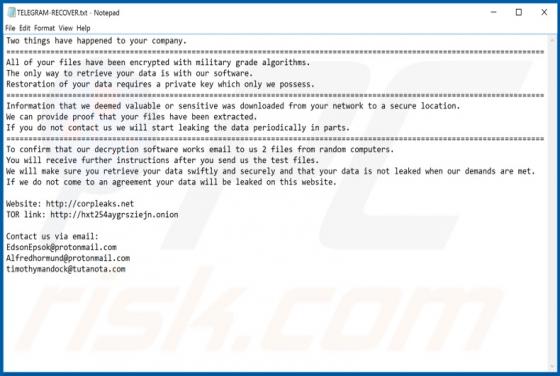
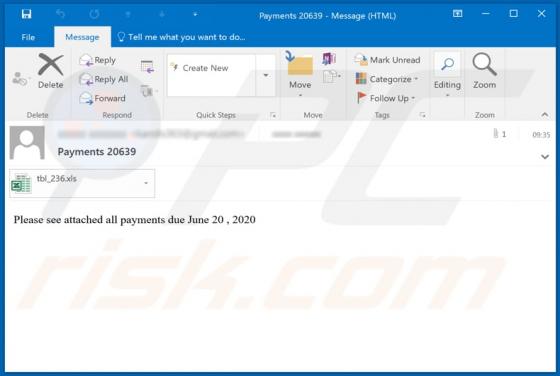
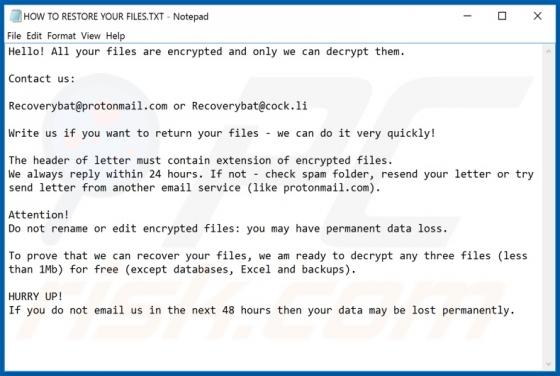
Discovered by GrujaRS, Gdjlosvtnib is malicious software (malware) belonging to the Snatch ransomware family. Systems infected with this ransomware experience data encryption and users receive ransom demands for decryption. During the encryption process, all affected file are appended with the ".g