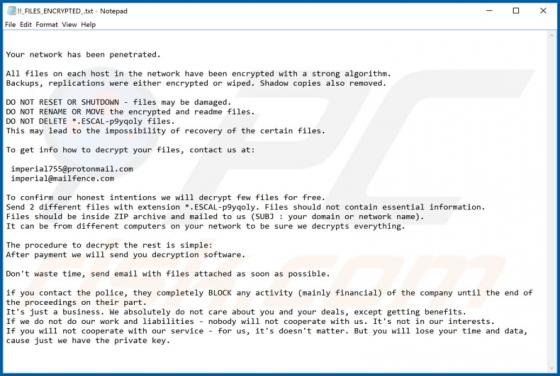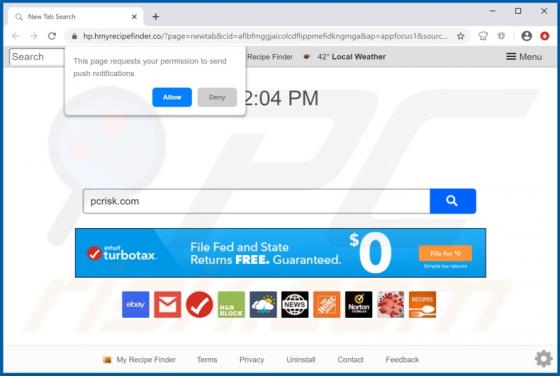
My Recipes Finder Browser Hijacker
My Recipes Finder is a rogue application advertised as a tool for easy access to various culinary recipes. It is categorized as a browser hijacker, due to the modifications it makes to browser settings to promote hmyrecipesfinder.co (a fake search engine). Furthermore, this app also monitors and c