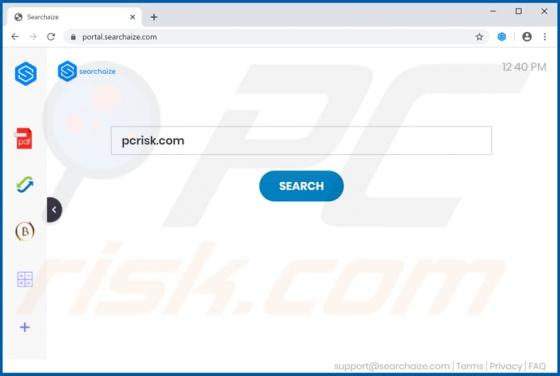
Searchaize Browser Hijacker
Searchaize is a browser hijacker which promotes searchaize.com, a fake search engine by modifying certain browser settings. As well as hijacking browsers, this app might collect various user-system information. Commonly, people download and install browser hijackers inadvertently and, therefore, t