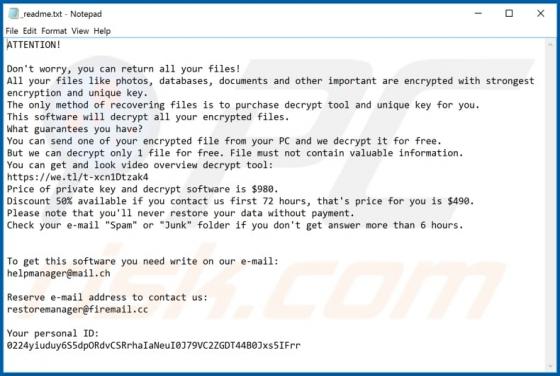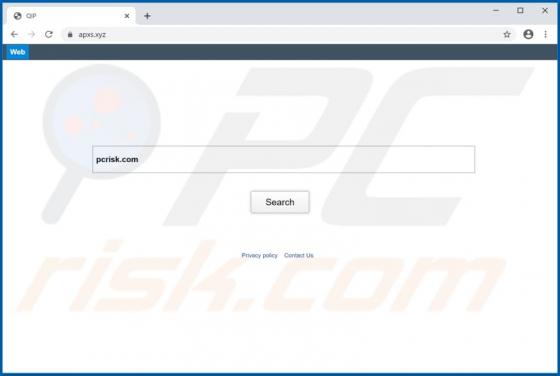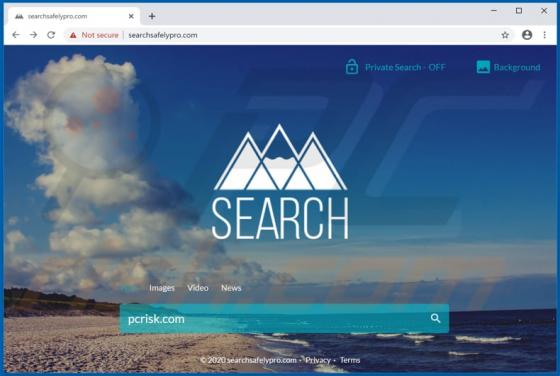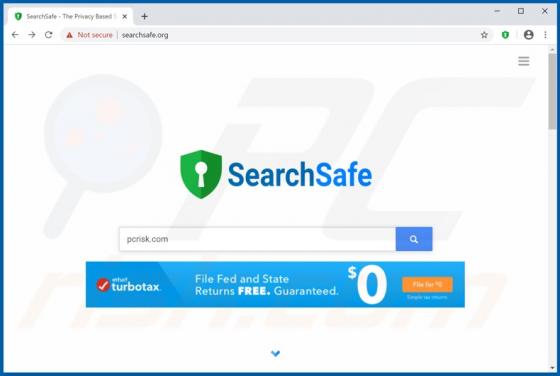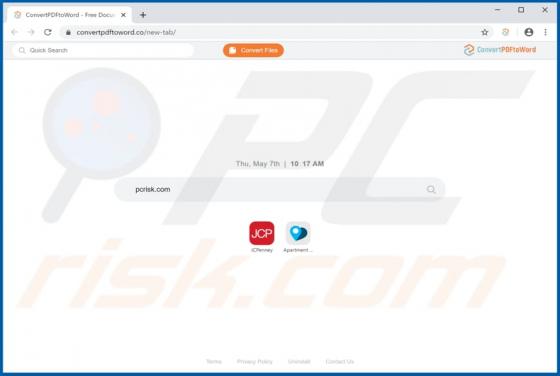
ConvertPDFToWord Browser Hijacker
ConvertPDFToWord is a browser hijacker which reassigns certain browser settings to convertpdftoword.co. In this way, it promotes this fake search engine. Furthermore, these apps often collect information relating to users' browsing habits, and other details. Since people often download and instal