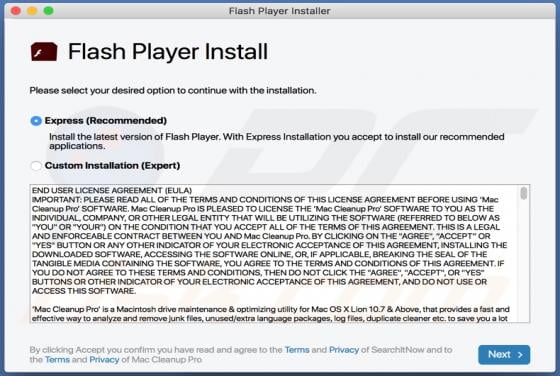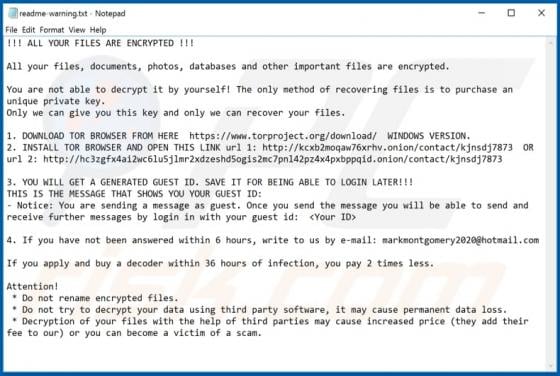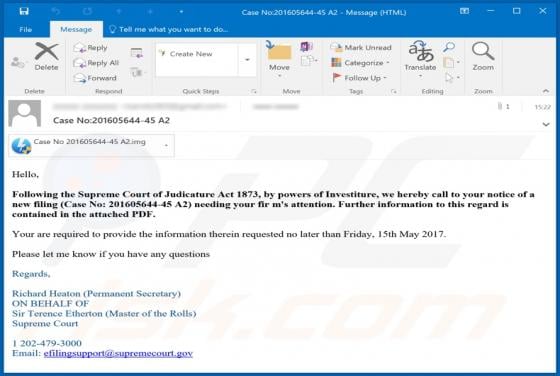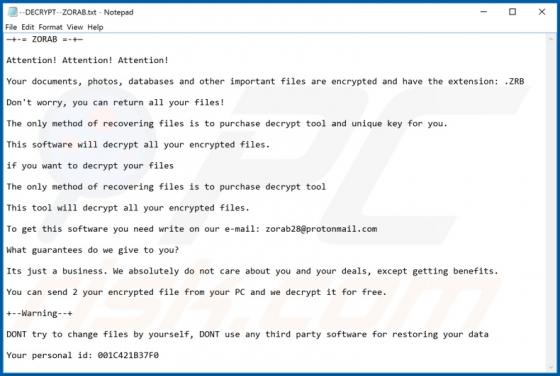
ZORAB Ransomware
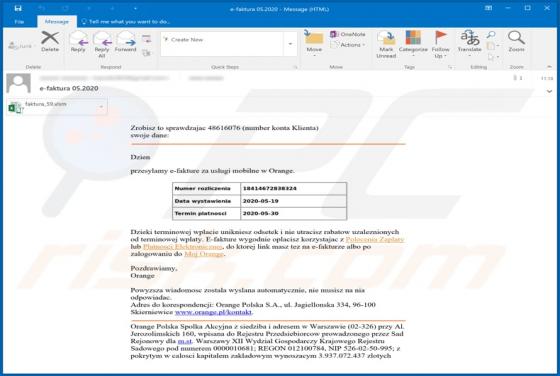
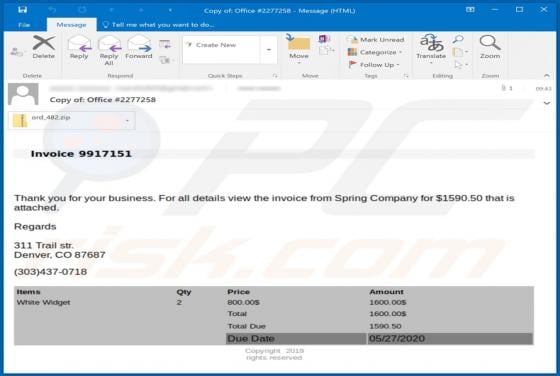
Discovered by malware researcher S!Ri, ZORAB is a malicious program classified as ransomware. Systems infected with this program experience data encryption and users receive ransom demands for decryption tools/software. During the encryption process, files are appended with the ".ZRB" extension.