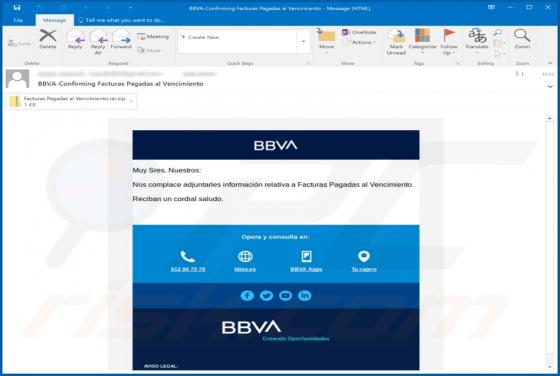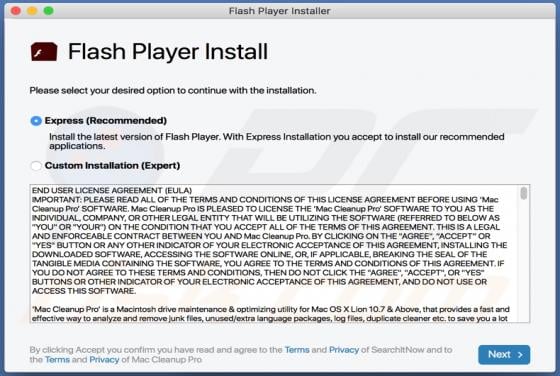
SearchModule Adware (Mac)
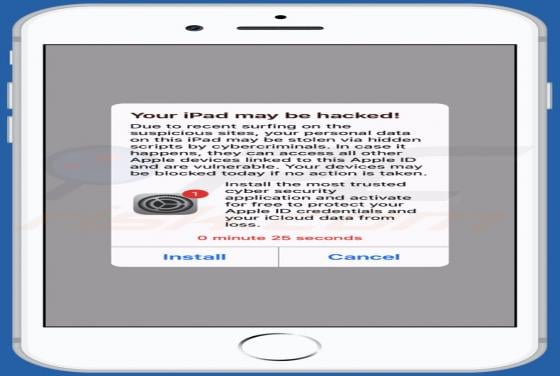
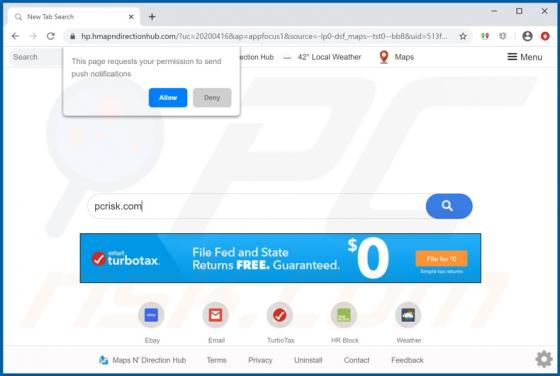
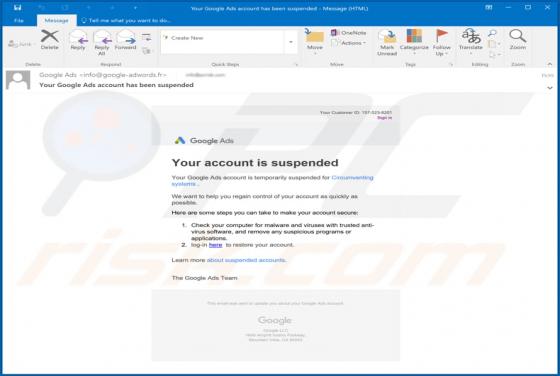
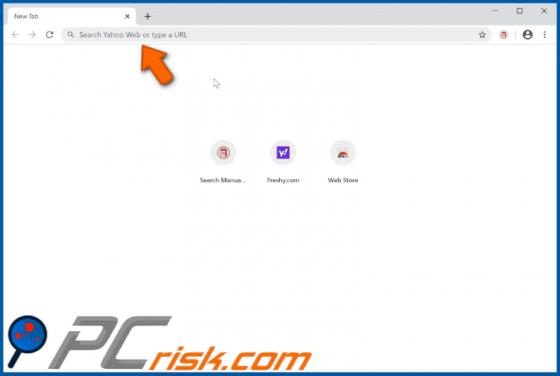
SearchModule is an adware-type application with browser hijacker characteristics. Following successful infiltration, this app delivers various unwanted and dangerous advertisements, modifies browsers and promotes a fake search engine. Additionally, most adware and browser hijackers can record br