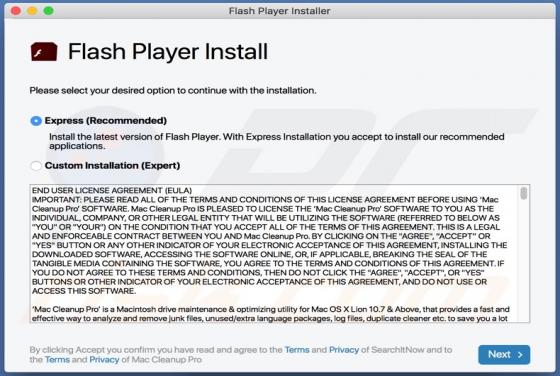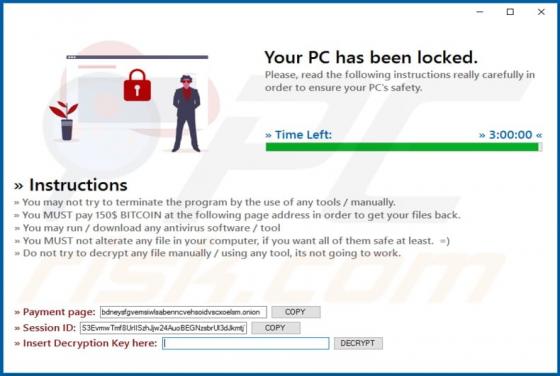
Dodged Ransomware
Discovered by MalwareHunterTeam, Dodged ransomware encrypts victims' files, changes filenames, disables Task Manager and displays a pop-up window containing the ransom message. Dodged renames encrypted files by appending the ".dodged" extension to filenames. For example, it renames "1.jpg" to "1.j