Mzlq Ransomware
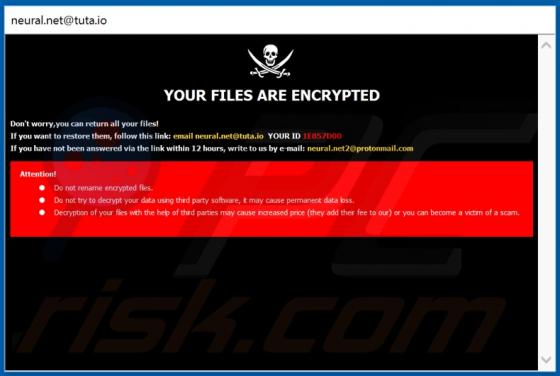
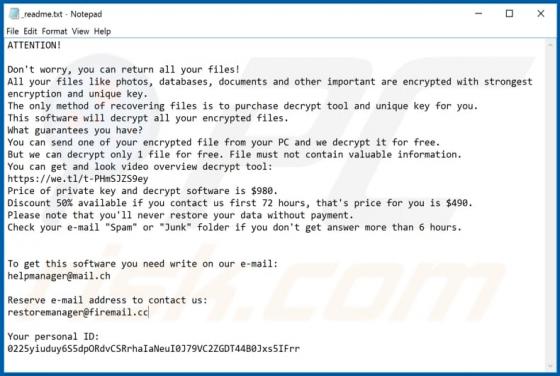
Mzlq is a malicious program belonging to the Djvu ransomware family. It renames all encrypted files by appending the ".mzlq" extension. For example, it changes a file named "1.jpg" to "1.jpg.mzlq", "2.jpg" to "2.jpg.mzlq", and so on. Instructions about how to contact Mzlq's developers, cost of de