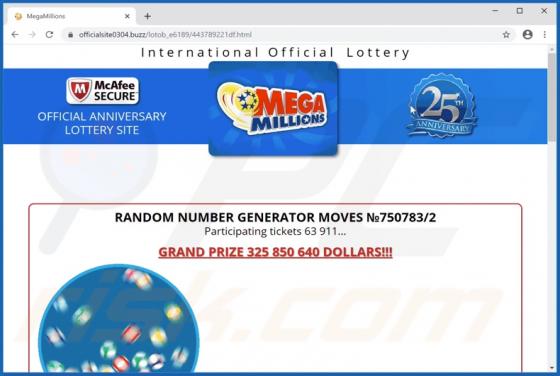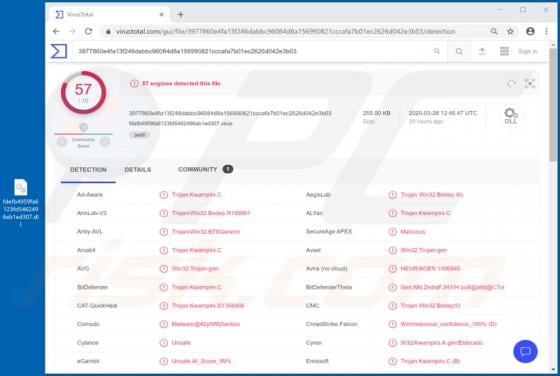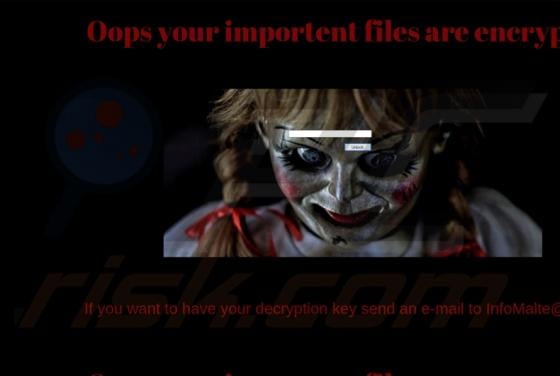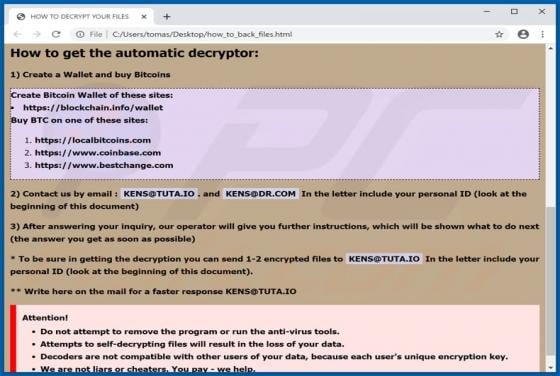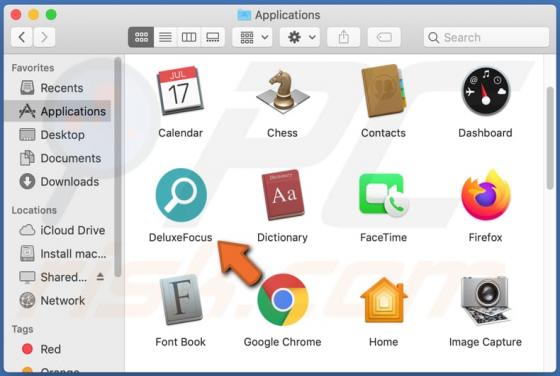
DeluxeFocus Adware (Mac)
DeluxeFocus is one of many applications that supposedly improves the browsing experience and delivers various other features. In fact, it is classified as a potentially unwanted application (PUA) that feeds users with advertisements and gathers information. These applications are classified as a