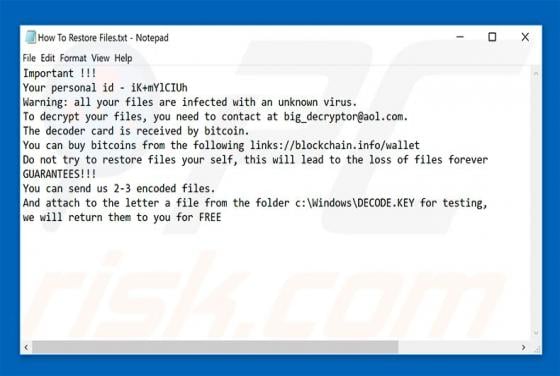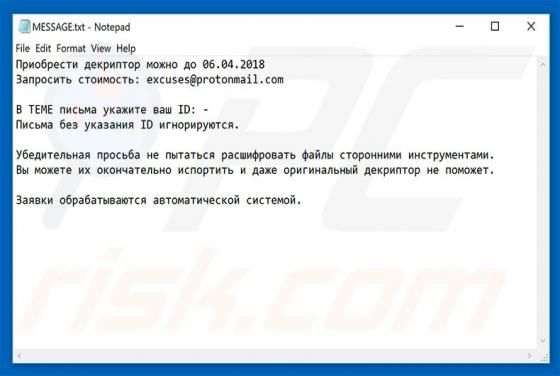
Excuses Ransomware
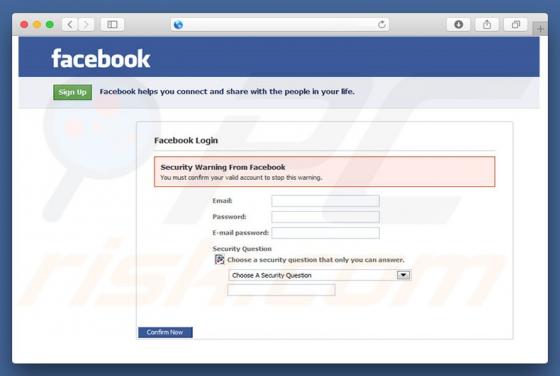
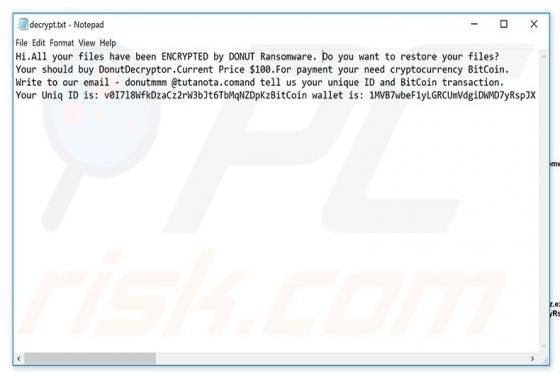
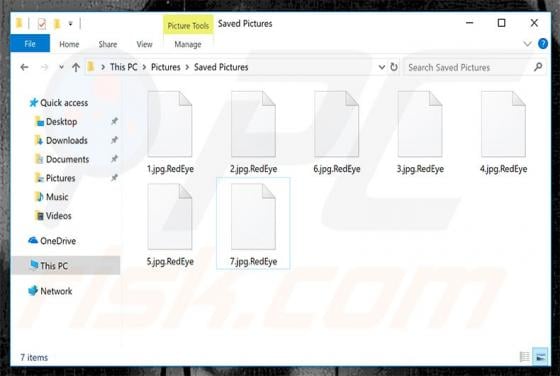
Excuses is another ransomware-type virus discovered by malware security researcher, Michael Gillespie. Once infiltrated, Excuses encrypts most stored files (thereby making them unusable) and adds the ".excuses" extension to each filename. For example, "sample.jpg" is renamed to "sample.jpg.excuse