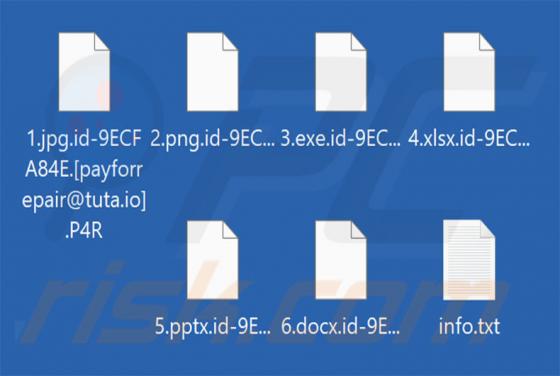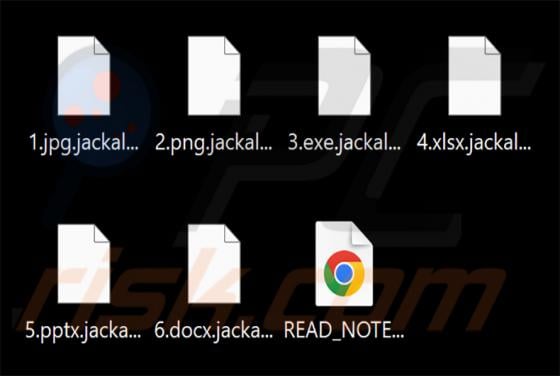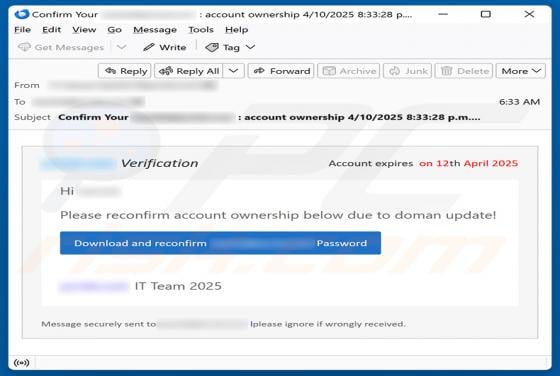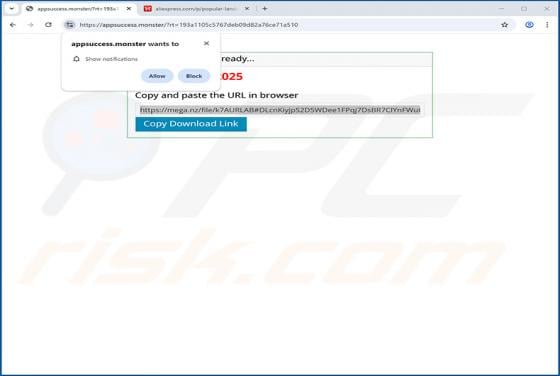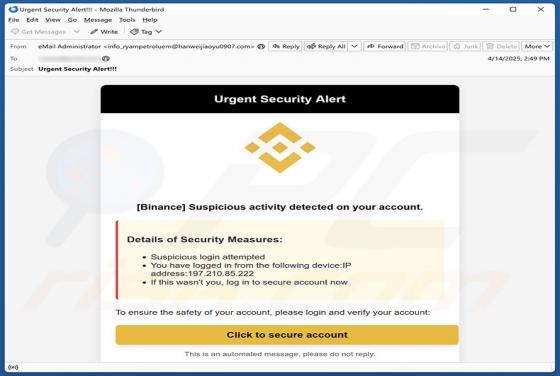
Binance - Urgent Security Alert Email Scam
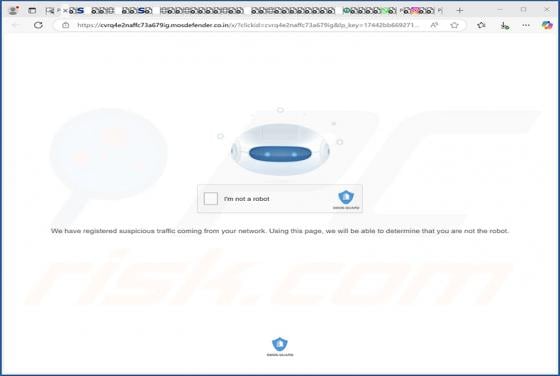
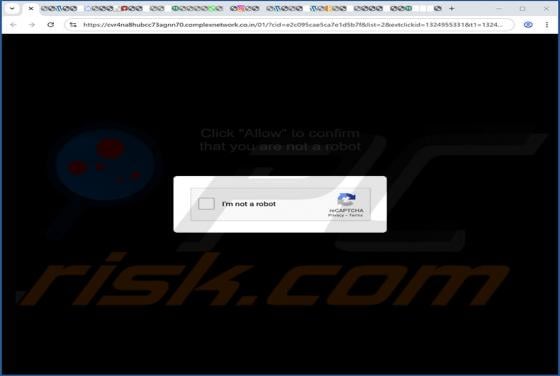
Our inspection of the "Binance - Urgent Security Alert" email, revealed that it is spam. This phishing message claims a suspicious sign-in attempt has been detected on the recipient's Binance account. By trying to investigate the supposed sign-in, users are lured into disclosing their account log-