Mitsubishi Corp. Email Scam
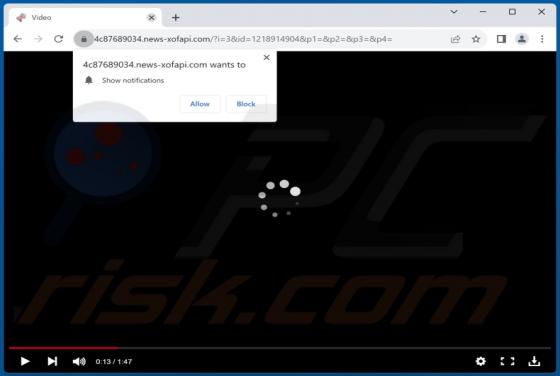
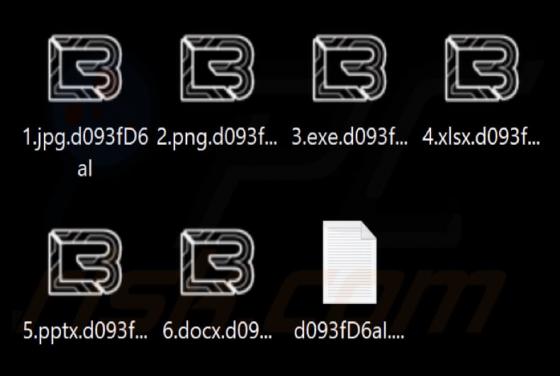
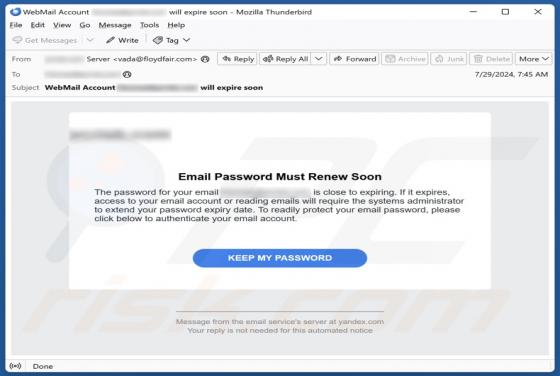
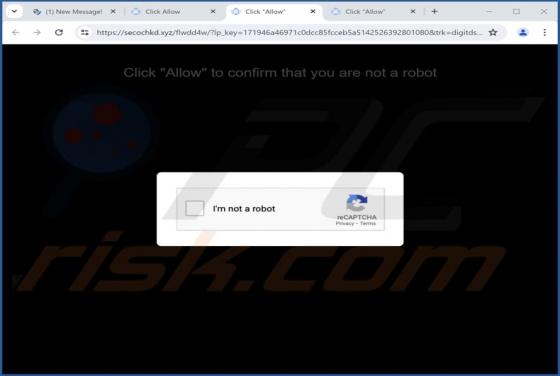
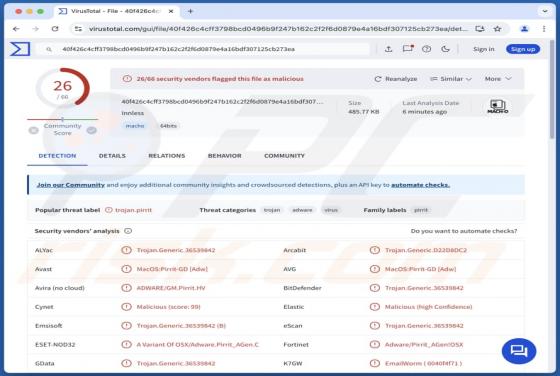
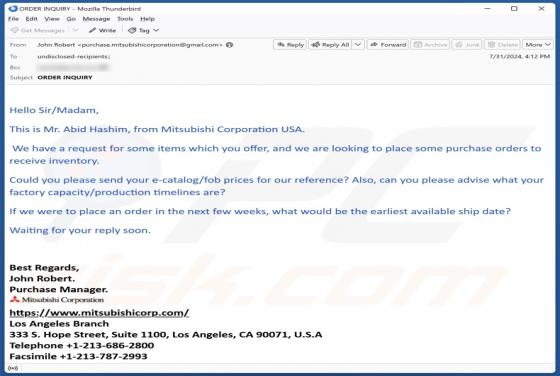
After inspecting this "Mitsubishi Corp." email, we determined that it is spam. The fake message impersonates an order inquiry from "Mitsubishi Corporation USA". This scam can operate in a variety of ways, most likely by targeting sensitive information or victims' funds directly. It must be emphas