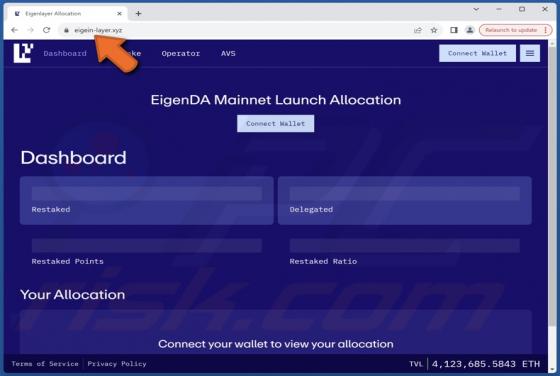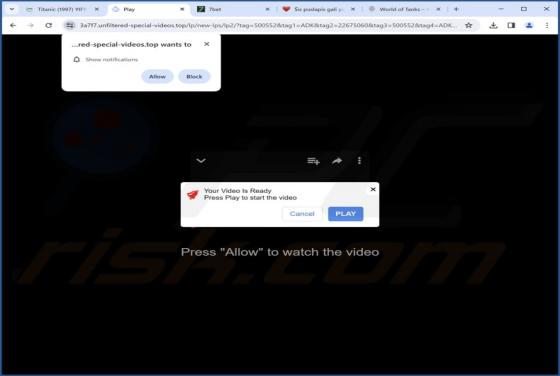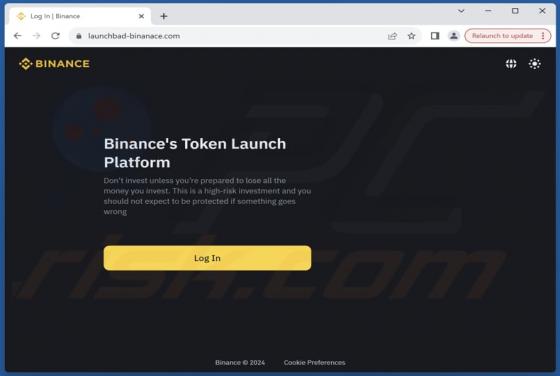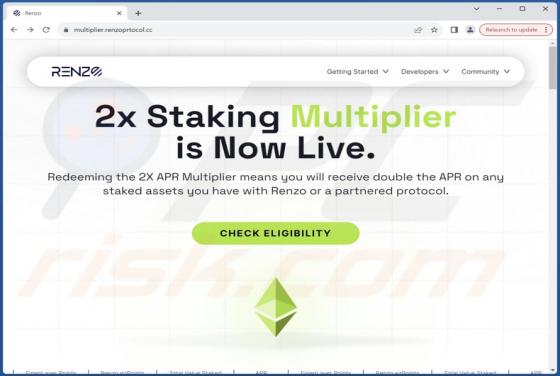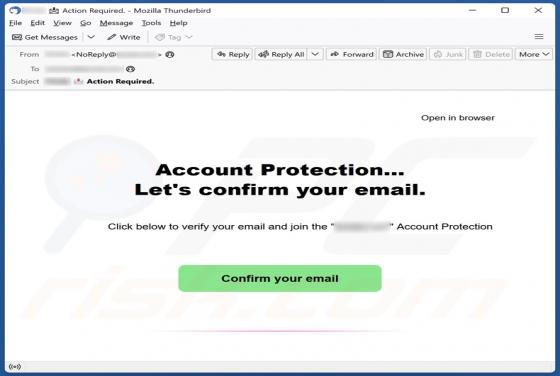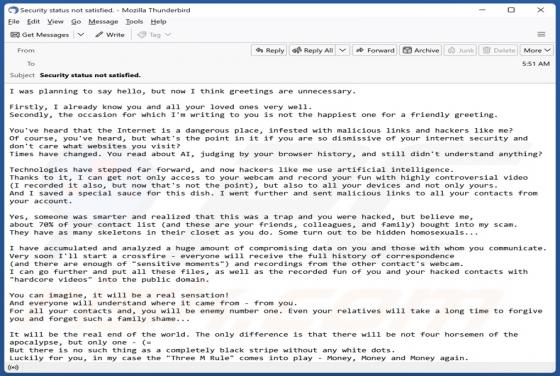
Internet Is A Dangerous Place Email Scam
After we inspected the "Internet Is A Dangerous Place" email, it became evident that this is a sextortion scam. This bogus letter claims that the recipient's devices were infected, and the infection proliferated to their contacts and family. This unauthorized and illegal access was used to collect