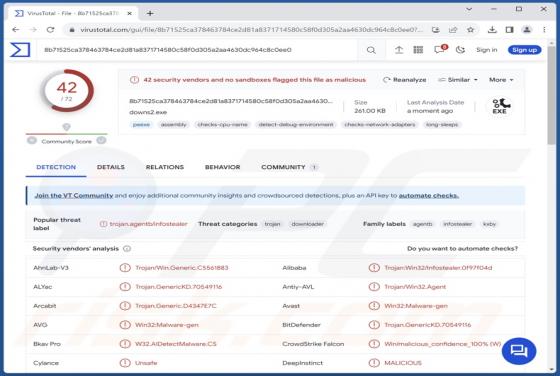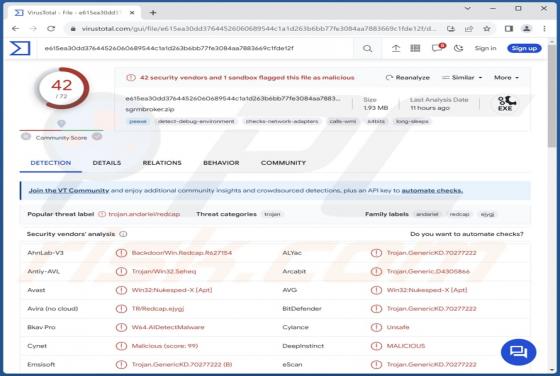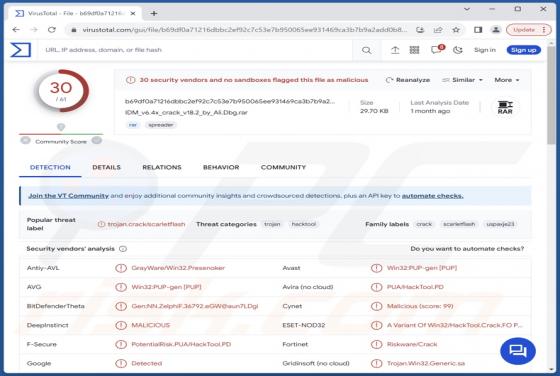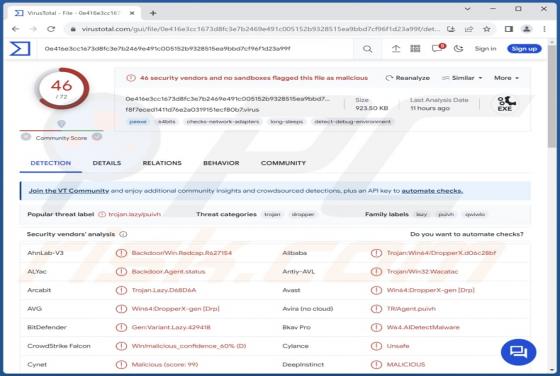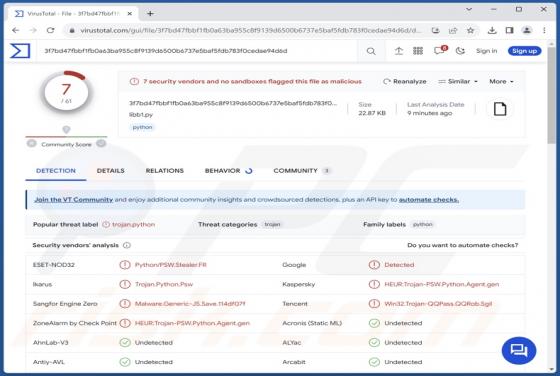
Editbot Stealer
Editbot is a piece of malicious software capable of extracting vulnerable information from infected devices. Targeted data includes browsing information, Internet cookies, log-in credentials, and other sensitive details. This stealer is written in the Python programming language. Editbot has been