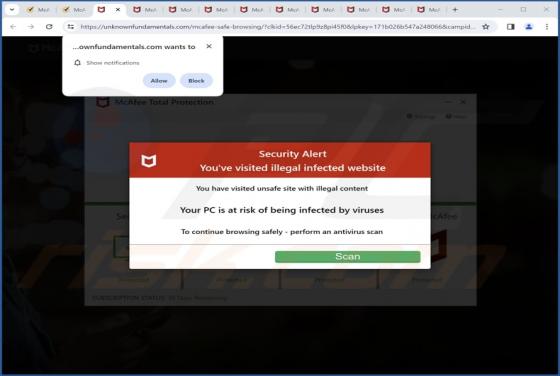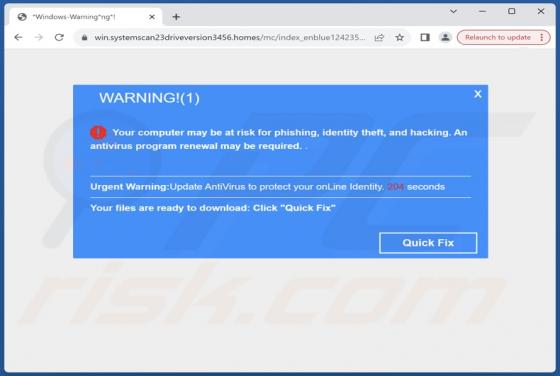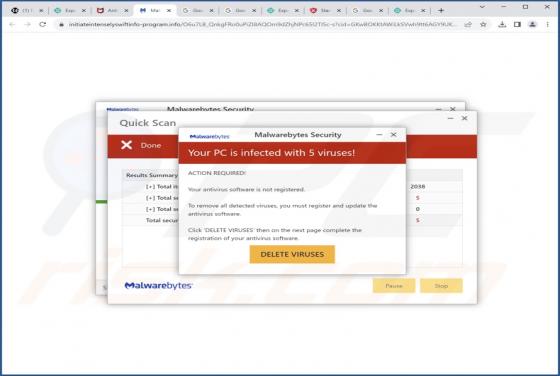
Malwarebytes - Your PC Is Infected With 5 Viruses! POP-UP Scam
"Malwarebytes - Your PC Is Infected With 5 Viruses!" is a scam that our researchers discovered while investigating rogue webpages. It displays a fake system scan that finds multiple viruses on users' systems. However, no website can detect threats on visitors' devices, and this is not an exceptio