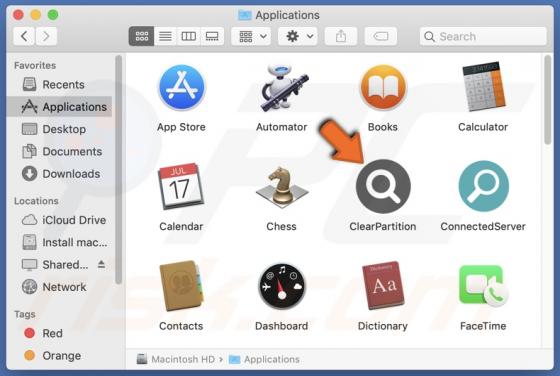
ClearPartition Adware (Mac)
ClearPartition is the name of a rogue application that we discovered while reviewing file submissions to the VirusTotal website. Upon inspection, we determined that it is advertising-supported software (adware) from the AdLoad malware family. ClearPartition is designed to feed users with undesir