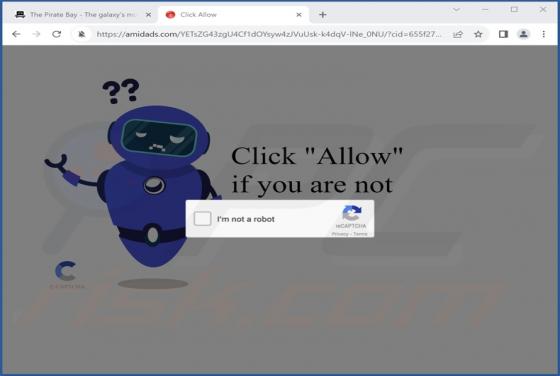
Veinmaster.top Ads
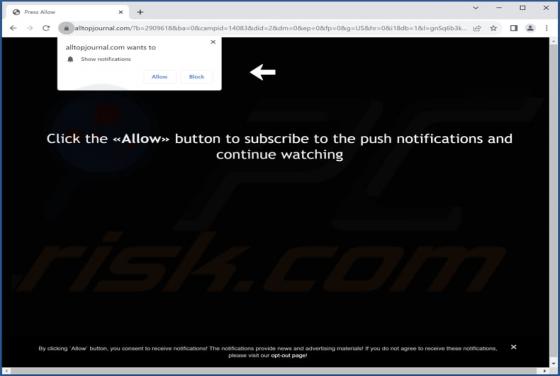
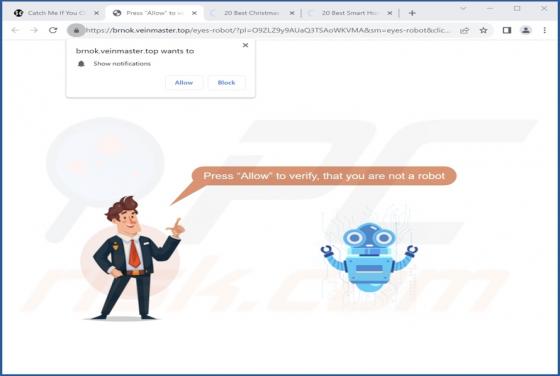
Veinmaster[.]top is a rogue webpage designed to promote browser notification spam and redirect users to other (likely untrustworthy/harmful) sites. The majority of visitors to such pages access them via redirects caused by websites that utilize rogue advertising networks. Our researchers discover