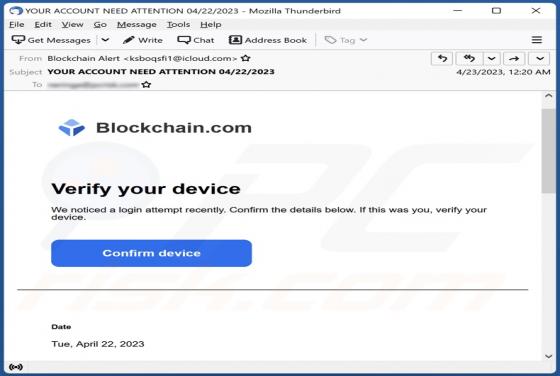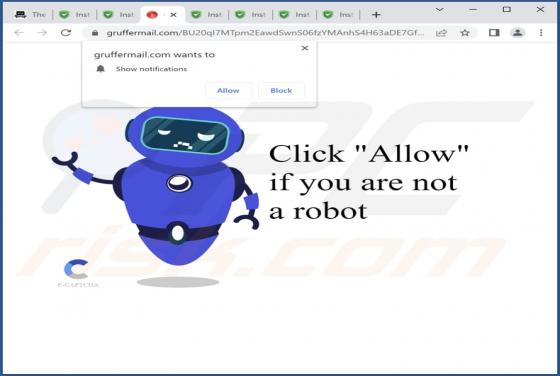
Gruffermail.com Ads
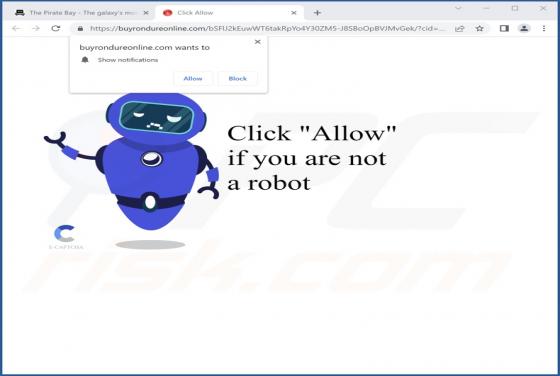
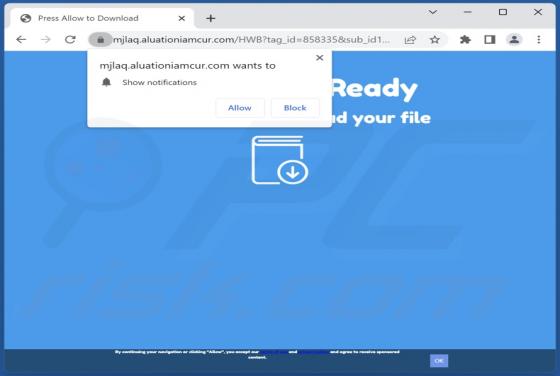
After analyzing gruffermail[.]com, we discovered that this website intends to deceive users into subscribing to push notifications. Gruffermail[.]com displays deceptive content to achieve it. Also, this site redirects its visitors to other untrustworthy websites. Typically, sites such as grufferma