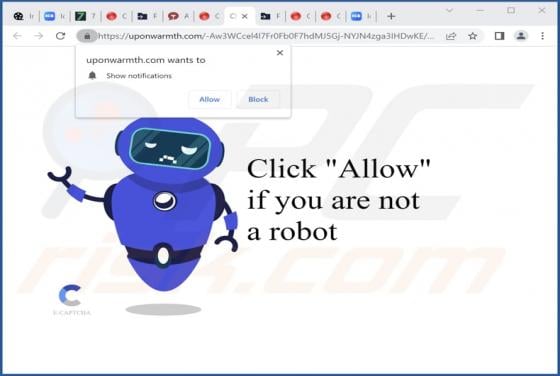
Uponwarmth.com Ads
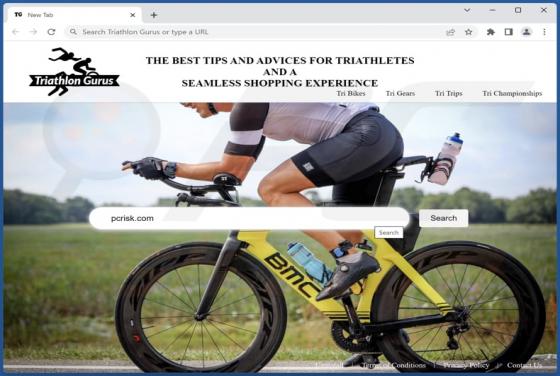
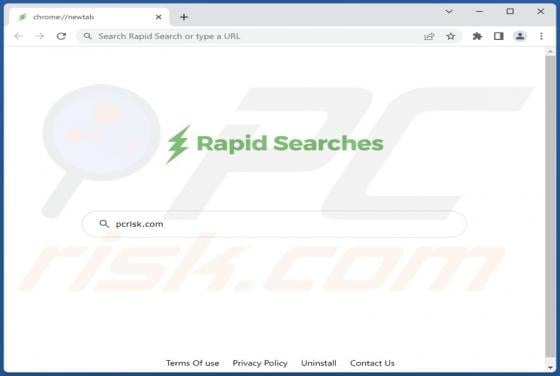
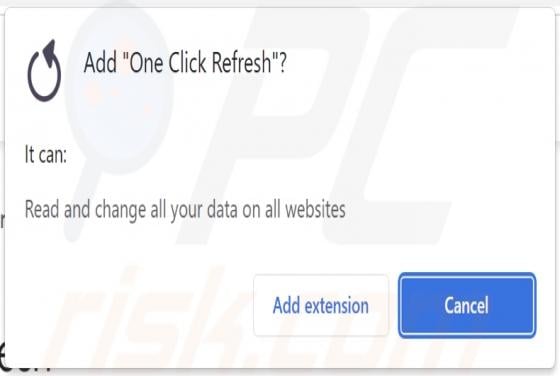
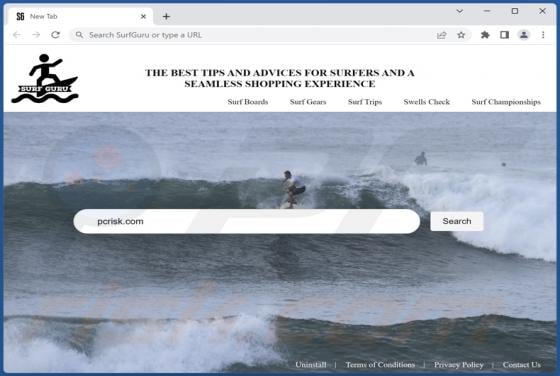
While investigating websites that use rogue advertising networks, we discovered uponwarmth[.]com. This deceptive website presents visitors with false information (in the guise of a fake CAPTCHA) to trick them into accepting notifications. Furthermore, accessing uponwarmth[.]com leads to other dubi