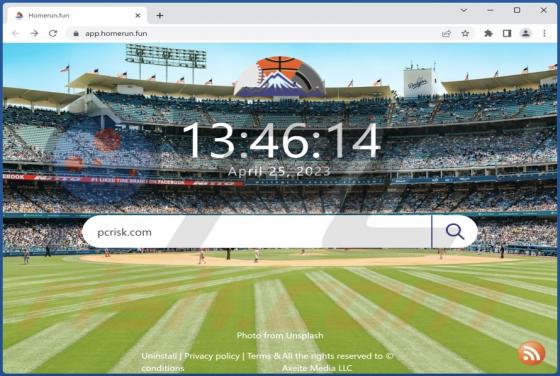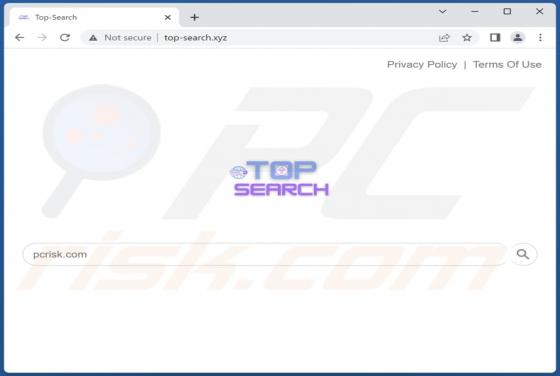
Top-search.xyz Redirect
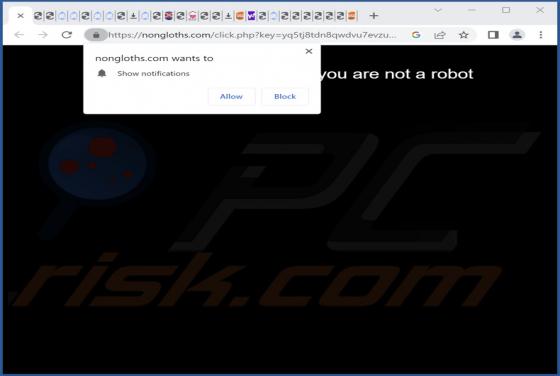
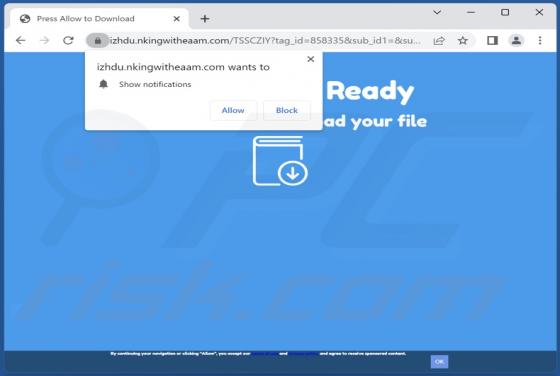
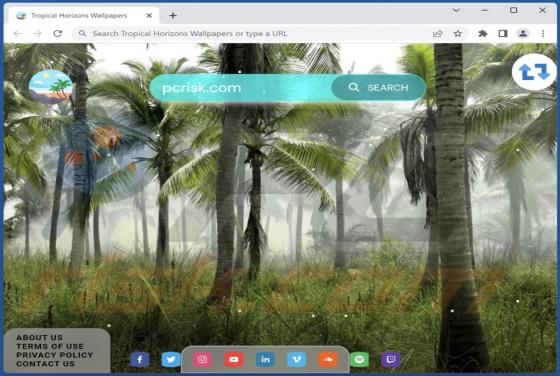
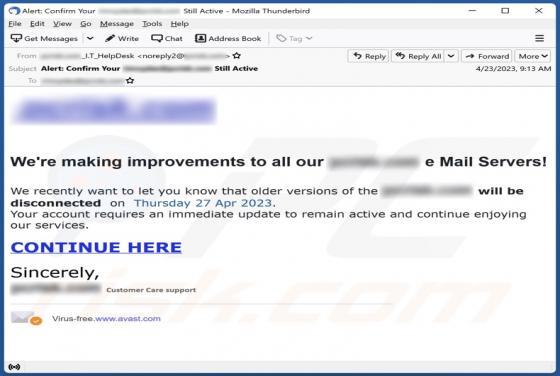
Our examination has revealed that top-search.xyz is a fake search engine. Such search engines are usually promoted through browser hijackers, which users unknowingly install on computers or add to browsers as apps. As a result, the browser settings are modified without their knowledge or consent.