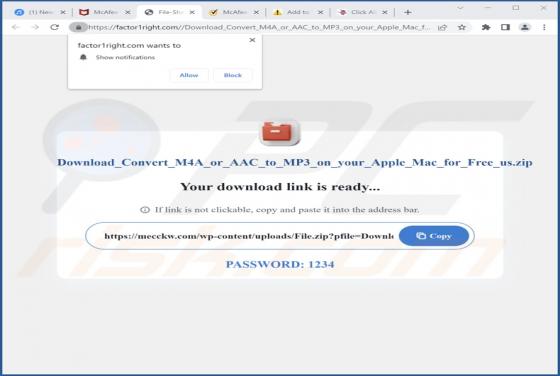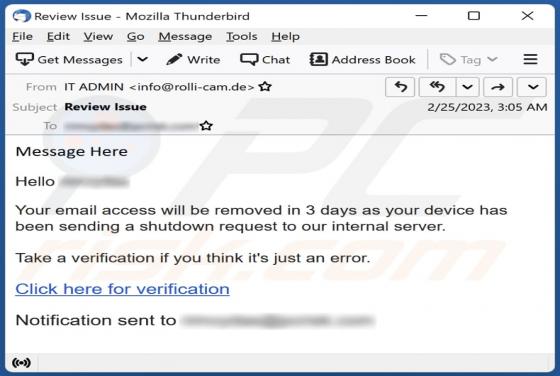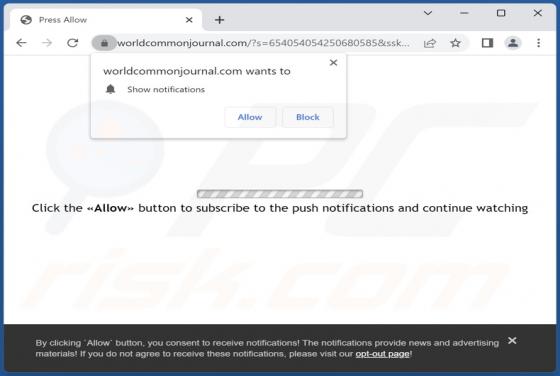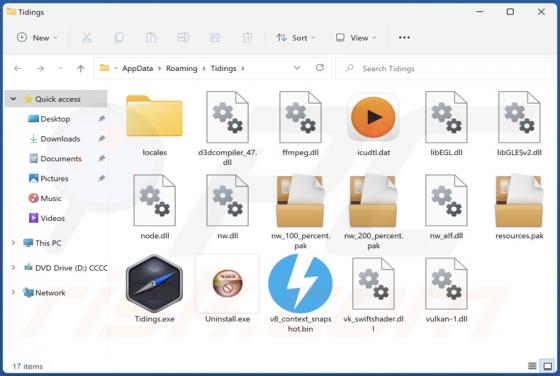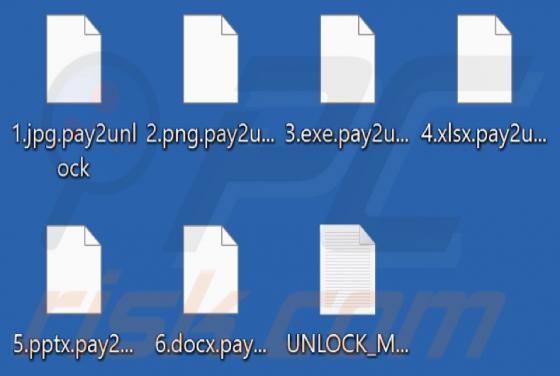
Blacksnaketeam Ransomware
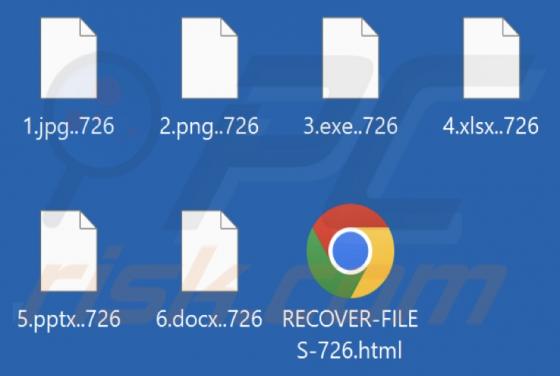
Blacksnaketeam is a ransomware-type program designed to encrypt data and demand payment for its decryption. When we executed a sample of Blacksnaketeam on our test machine, it began encrypting files. The filenames of affected files were appended with a ".pay2unlock" extension. For example, a file