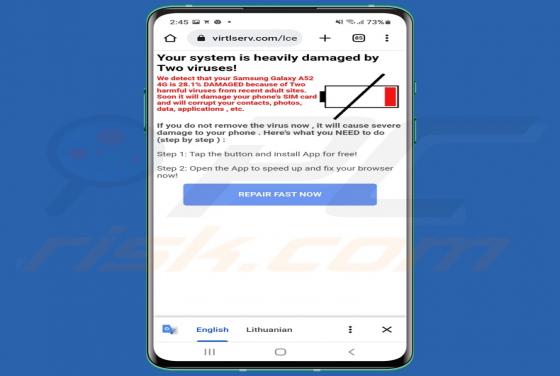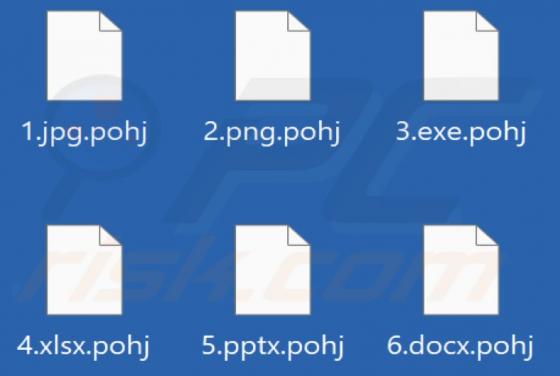
Pohj Ransomware
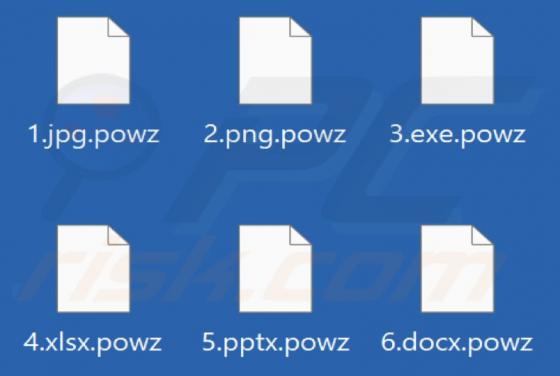
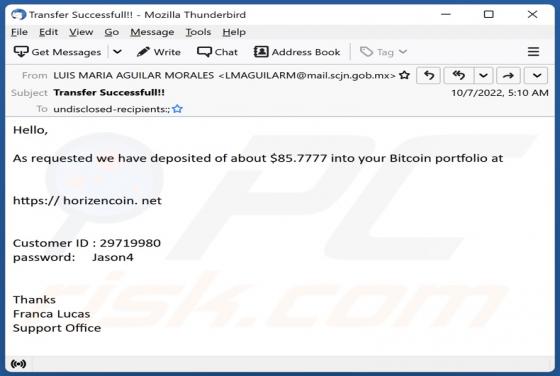
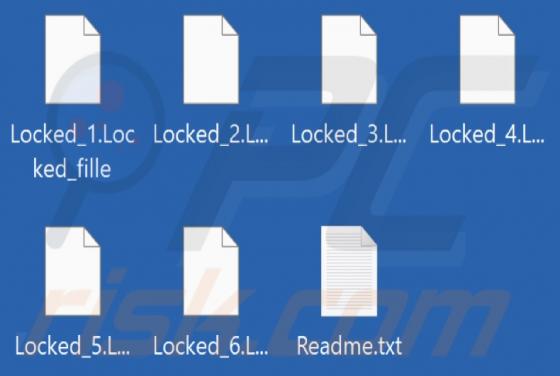
Pohj is ransomware that belongs to the Djvu family (one of the most widespread ransomware families). We discovered this ransomware while examining malware samples submitted to VirusTotal. Pohj encrypts data, appends the ".pohj" extension to filenames, and drops the "_readme.txt" file containing a