Reporting ransomware to authorities
Table of Contents:
- Should ransomware attacks be reporter?
- Reasons to report an attack.
- How to report an attack?
- List of authorities where reports should be sent.
Falling victim to a cyberattack, let alone a ransomware attack, requires making several difficult decisions. It is clear from a recent Europol report that reporting the incident to authorities is one of those difficult decisions. The report highlighted how under-reported ransomware incidents are and often authorities only hear about incidents through the media rather than the victim.
It is easy to demand that victims of crimes report them for numerous legal and ethical reasons, let alone to help authorities catch those that perpetrate crimes. The reality is that falling victim to a crime has a level of stigma attached to it. It can be embarrassing to admit that you were tricked or scammed. For organizations that fall victim to ransomware attacks, this stigma appears to be one of the major reasons the specific crime goes unreported.
The current ransomware threat landscape has evolved to include several ransomware gangs or even gags that have formed “cartels” that specifically target large organizations, be they private companies or government agencies. This shift, which occurred towards the start of 2019 in earnest has resulted in massive organizations, some Fortune 500 companies, added to ever-increasing lists of victims. Garmin, Canon, and Konica Minolta are just some of the high profile victims that have been massively impacted by a ransomware gang.
The stigma of falling victim to ransomware has taken on new meaning as companies fear the impact such an attack will have on their customer and stakeholder relationships. This may be one reason behind the under-reporting of the crime. Any cyber incident not only affects the bottom line and recovery can be an expensive prospect, but reputational damage is to be expected. It is felt by experts that being transparent with regards to a ransomware incident can help repair the reputational damage more effectively than when attempts are made to sweep the matter under the rug. The rest of this article is dedicated to why ransomware incidents should be reported to authorities and, importantly, how to do so.
Should ransomware incidents be reported?
The short answer is yes, but short answers do little to convey the importance of the question in the first place. The easiest answer to give is that for many organizations that are required to adhere to certain pieces of compliance legislation, or a set of standards data breaches need to be reported. A year ago, you could argue that a ransomware incident did not amount to a data breach or put differently a cyber incident where sensitive information belonging to customers or registered users of a service has been compromised. The start of 2020 shattered the academic debate regarding whether a ransomware attack was a data breach or not.
In January 2020, news reports began emerging that the Maze ransomware gang were threatening to release data stolen from victims before the ransomware was executed and data encrypted.
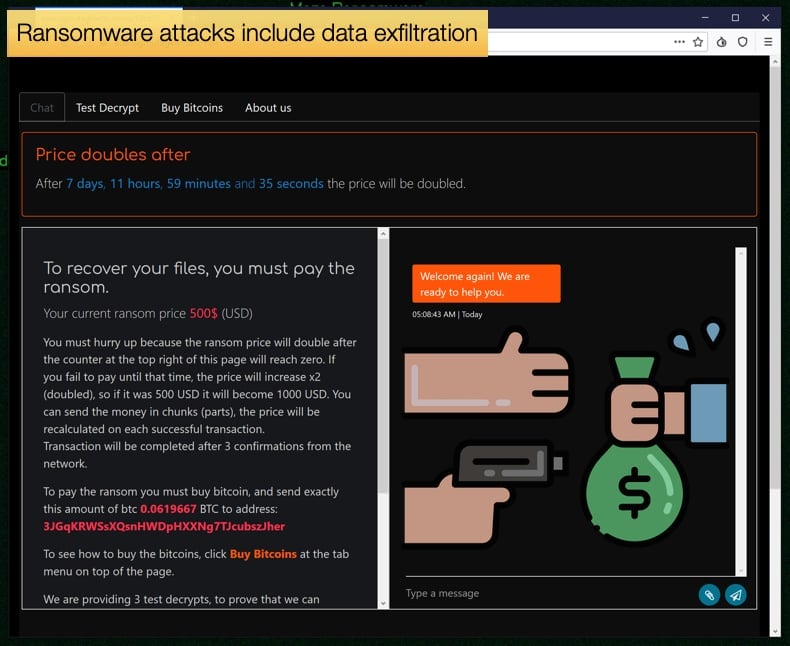
Soon the threats became reality when Maze started releasing data, they had stolen via what would be called a “leak site”, typically hosted in one of the corners of the dark web. This placed specific ransomware incidents firmly in the category of a data breach and needed to be treated as such. For many pieces of legislation and compliance standards, there is a requirement to report incidents to the relative authorities specified within the legislation.
It is important to note that despite the evolution in ransomware attacks now including data exfiltration, sometimes referred to as “double extortion”, not all ransomware attacks are also data breaches. The determining factor will be if data was exfiltrated or not. The most recent evolution in tactics is ransomware gangs employing call centers to further threaten victims, in many countries this heightened level of abuse may be considered a crime and thus should also be reported to law enforcement authorities.
More Reasons
If a victim is obliged to report ransomware because of legislation a strong argument to report the incident exists. There are several other reasons to report ransomware incidents independent of laws stipulating they should. Firstly, the information law enforcement officials get from the reporting of the incident to facts given by forensic cybersecurity specialists go a long way in helping to catch those involved.
Due to high levels of anonymity afforded to cybercriminals through the use of technologies like the Dark Web and other anonymizing services catching those involved can be a difficult task. One that at the beginning may be near impossible. However, over time researchers can piece together who is behind the attack or in many cases a series of attacks. Reporting the incident allows investigators access to vital information needed to do exactly that.
Secondly, the more data that is collected the better in terms of awareness and education. This is the case with regards to law enforcement and other authorities tasked with defending against cybercrime being able to issue alerts. Typically, these alerts contain information regarding tactics used by specific gangs, favored vectors of compromise, and measures that can be taken by other organizations to help prevent falling victim to the specific ransomware strain covered in the alert. To make these alerts effective in combating ransomware gangs, information must be of the highest quality, and victims reporting on incidents help ensure correct information is disseminated.
Lastly, it is important to discuss the international nature of cybercrime. Cybercriminal organizations like ransomware gangs will target organizations outside of their country of origin for several reasons. In Russia, as has been well-documented, the government turns a blind eye to cybercriminals that target foreign organizations as the attacks do not harm the government's foreign relations policy, or it might even further specific aims.
Such geopolitical influences can make it hard for law enforcement agencies to bring those to justice, but it is not impossible. Many law enforcement agencies work together to combat cybercrime including international organizations like Interpol and Europol. Reported incidents help close the ring on cybercriminals leading to the seizure of servers and arrests if the organization's linchpins travel overseas. Governments can also place sanctions on states believed to harbor cybercriminals.
The above reasons certainly put the case forward that reporting ransomware incidents benefit law enforcement agencies but what of the organization that is affected? When incidents are reported law enforcement is capable of providing valuable remediation advice that could easily prove beneficial to an organization’s speedy recovery. Further, several law enforcement agencies have established partnerships with private security firms to make free decryptors available to those affected. Reporting an incident may help business leaders get the decryptor they need to recover from an attack. Partnerships like No More Ransom are looking to create a database of ransomware information along with decryptors to help all those affected.
How to report a ransomware incident?
To report an incident, the relevant local authority will need to be contacted. Before, this can happen as much forensic data pertaining to the incident needs to be collected. This can be done by qualified IT staff. Note that the information needed to report a ransomware attack will be different depending on the fact if you are reporting an attack on behold of your company or simply as a personal computer user. In general organizations may be asked to provide the following information when reporting the incident:
- Your organization’s information (industry, business type, size) and who is best placed to communicate with authorities moving forward.
- Approximate date and time of the ransomware attack.
- How the attack occurred (via an email link or attachment, exploited vulnerability, misconfigured RDP port, etc.)
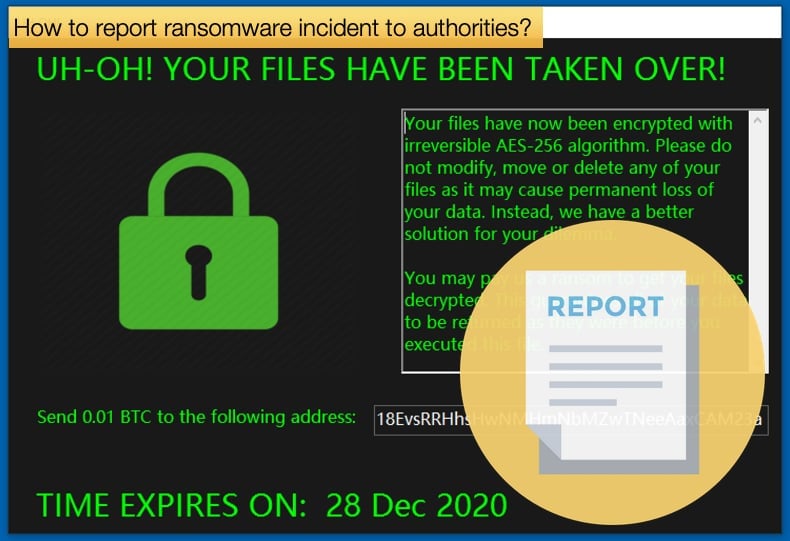
- A copy or photo of the ransom demand note or lock screen.
- Name of the ransomware variant (usually included in the ransom note or encrypted file extension added after encryption.)
- Any relevant IP addresses that are connected to your network that you do not recognize.
- The file extension of encrypted files.
- Email address, URL, or any other communication method provided by the threat actor.
- Electronic copies of any communication you have had with the threat actor.
- Threat actor’s bitcoin wallet address, this is often provided either on the ransom note or in subsequent communications with the attacker.
- Ransom amount demanded and ransom amount paid.
- Overall losses associated with the ransomware attack including ransom amount.
If you are a victim of ransomware please report this incident to your local authorities:
ACSC |
Polizei |
Police |
Polícia Federal |
CyberCrime |
Centre for Cyber Security |
Ministry of the Interior |
Cyber Crime Police |
Policie |
Politi |
Action Fraud |
Politsei |
Poliisi |
Ministère de l'Intérieur |
Polizei |
Hellenic Police |
Hong Kong Police |
Rendőrség |
Cyber Crime Cell |
Cyber Police |
Garda Síochána |
Nomoreransom project |
Polizia di Stato |
Cybercrime Project |
Policija |
ePolicija |
Police |
Pulizija |
Politie |
Police |
Ministry of Internal Affairs |
Police Scotland |
Singapore Police Force |
Ministerstvo Vnútra |
Policija |
National Police Agency |
Policía Nacional |
Polisen |
Cyber Police |
IC3 |
|
|
