Maze’s Sneaky New Trick
The Maze gang was last in the news when they managed to pull off a successful attack on Canon. This is but one of the gang’s many exploits and once more the group is in the news, not for a high profile victim but for tactics adopted that will likely add to the growing list of Maze’s victims. The gang is no stranger to adopting new tactics successfully. The gang was in all likelihood the first to start releasing data stolen from victims who do not pay promptly. Now the group has adopted a tactic seen used by Ragnar Locker to remain undetected until it is too late.
According to Sophos Labs, the Maze gang has now been seen using Ragnar Locker’s virtual machine technique to remain undetected by endpoint security applications. Sophos Labs’ published an article detailing the discovery and how it is carried out recently, however, the discovery was made when tracking a Maze campaign dating back to July 2020. Simply put the attack is carried out by placing the various components of the ransomware within a virtual machine once access to a file server has been achieved. Based on the evidence provided by researchers it would appear that this deployment of components to a virtual machine occurs late in the attack chain as the ransomware’s operators had already compromised the victim’s defenses and lurked on the network for some time.
The compromising on networks and waiting for the right time to strike has become a hallmark of human-operated ransomware. The main aim then of deployment via virtual machine is to help keep the malware under the radar until the encryption process can begin. This is often the noisiest part of the process and when stealth is not the primary goal but speed.
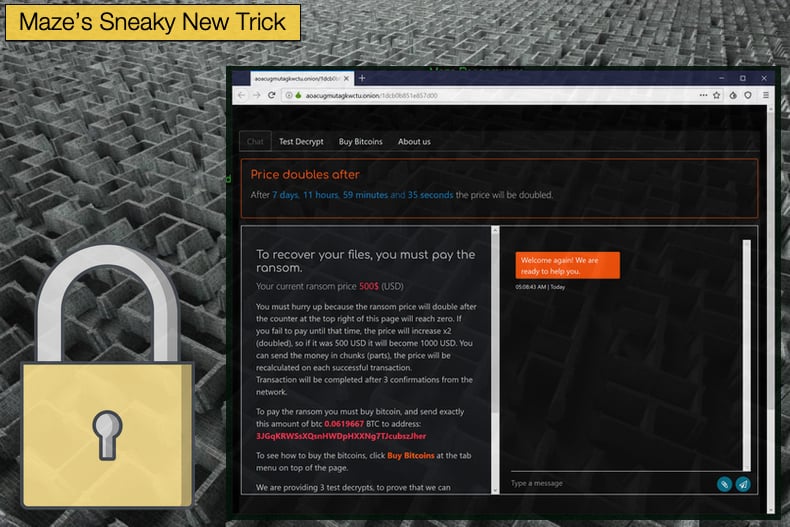
In the Maze incident, the gang managed to distribute the file-encrypting payload of the ransomware on the VM’s virtual hard drive (a VirtualBox virtual disk image (.vdi) file), which was delivered inside of a Windows .msi installer file. The file itself was more than 700MB in size. This all ran on Window’s 7 which is one of the key differences between the Maze incident and those involving Ragnar Locker, which ran on Windows XP. Another significant discovery regarded the length of time the attackers were on the victim’s network before beginning the encryption process. Researchers noted,
“A threat hunt through telemetry data initially indicated the attackers may have been present on the attack target’s network for at least three days before the attack beginning in earnest, but subsequent analysis revealed that the attackers had penetrated the network at least six days before delivering the ransomware payload. The investigation also turned up several installer scripts that revealed the attackers’ tactics, and found that the attackers had spent days preparing to launch the ransomware by building lists of IP addresses inside the target’s network, using one of the target’s domain controller servers, and exfiltrating data to cloud storage provider Mega.nz.”
The Cartel
Once the victim’s data had been encrypted and the ransom note dropped, the gang demanded 15 million USD in exchange for the decryption key. Sophos Labs stated that the victim did not pay the ransom. As mentioned above it was Ragnar Locker that first implemented the technique which was also investigated by Sophos Labs. While the two gangs used the same technique, the approaches differed only slightly. This would suggest some kind of connection between the two gangs. Not mentioned in the Sophos article, reports Bleeping Computer emerged in June 2020 that Maze had formed a partnership with Ragnar Locker. The news followed reports on the same platform that Maze had partnered with the LockBit gang.
This cooperation between the gangs of competing ransomware operations who collude with each other to increase profits and increase the success of their attacks has been labeled by some as a “cartel.” Functionally, it does act as one and shares resources as the LockBit gang does not, to the best of the writer’s knowledge, has a data release website, also referred to as a leak site, which is becoming increasingly common amongst ransomware gangs looking to announce new victims as well as prove that they have indeed stolen data. Maze has confirmed that they are indeed working with the two above mentioned ransomware gangs, stating with regards to LockBit after announcing their cooperation via their leak site,
“In a few days another group will emerge on our news website, we all see in this cooperation the way leading to mutual beneficial outcome, for both actor groups and companies. Even more, they use not only our platform to post the data of companies, but also our experience and reputation, building the beneficial and solid future. We treat other groups as our partners, not as our competitors. Organizational questions is behind every successful business,”
That other group was confirmed as being Ragnar Locker. The use of the same virtual machine technique would further give credence to the cartel existing and perhaps even a greater level of co-operation between the gangs than immediately thought. The exact details to the extent of cooperation are unknown and might never be known, however, its existence has caused several waves in the underground cyber-criminal community as it looks like other gangs are willing to join, even if Maze is not so keen to buddy up. One gang in particular that operates the Suncrypt strain announced that they too had partnered with Maze, with latter publicly stating later that they had not had any contact with SunCrypt. Regardless, SunCrypt managed to add the North Carolina School District to its steadily growing victim list.
Ransomware’s First Death
Unrelated to the Maze cartel and the gang’s new tactics, another bit of ransomware news will mark a turning point in the history of ransomware and the drive to combat it. On September 17, 2020, the Associated Press and ZDNet reported that German authorities are investigating the death of a patient at a hospital in Duesseldorf as a result of a ransomware attack. Hospitals have long been a target of ransomware gangs, with this publication covering a SamSam infection at a hospital in 2018. For as long as hospitals have been the crosshairs of ransomware operators so has the fear that patients may be denied critical care and deaths may result. Often seen as a worst-case scenario, if German authorities do indeed prove it to be the case then those worst fears have been realized.
In this incident, the patient, identified only as a woman who needed urgent medical care, died after being re-routed to a hospital in the city of Wuppertal. The second hospital in Wuppertal is more than 30 km away from her initial intended destination, the Duesseldorf University Hospital. The Dusseldorf hospital was unable to receive the patient as it had been dealing with a ransomware attack which occurred on September 10. This incident marks the first-ever fatal casualty due to a ransomware attack. This is new ground for ransomware, as it has officially crossed the line between creating financial victims to ones who may have suffered the ultimate price.
According to RTL, the ransomware gang has withdrawn its ransom demand after German police reached out. The hospital has since received decryption and is restoring its systems. The hospital blamed the infection on a vulnerability found within widely used commercial software. In the above mentioned Associated Press report, it may be the attack was by mistake as the ransom note was addressed to the Duesseldorf Heinrich Heine University and not the Dusseldorf University Hospital that was affected but is still part of the wider university network. Whether an accident or not, the event is still tragic and a further black mark against ransomware, and those who chose to distribute it for financial gain. Financial crimes are a serious matter but the courts tend to treat loss of life both intentional and accidental, as incredibly serious not only to the victim and their family but to society as a whole.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion